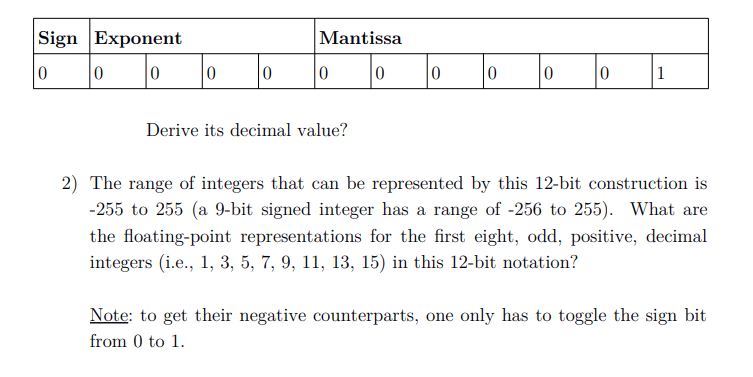
Sign Exponent Mantissa Derive its decimal value? 2) The range of integers that can be represented by this 12-bit construction is -255 to 255 (a 9-bit signed integer has a range of -256 to 255). What are the floating-point representations for the first eight, odd, positive, decimal integers (i.e., 1, 3, 5, 7, 9, 11, 13, 15) in this 12-bit notation? Note: to get their negative counterparts, one only has to toggle the sign bit from 0 to 1.
Q: The Government of United States of America has decided to issue new currency notes with special…
A: Code is below:
Q: Soundex System Soundex is a system that encodes a word into a letter followed by three digtis that…
A: the code in python below
Q: Encoding Input- Write a program to take input a string from user and encode the string according…
A: Write a C++ program to take input a string from user and encode the string according to rules given…
Q: Floating-point struct Part 1 Define a struct Single that describes the bit layout for a…
A: According to the information given:- We have to define the single precision floating point numbers.
Q: Given a representation 112345 siæ Complete its positional notation and calculate its decimal…
A: Given representation: 112345six Position Hundred-thousand Ten-Thousand Thousand Hundreds Tens…
Q: int cal_media() { cout>name; cout>marks1>>marks2; totalamarks = marks1 + marks2; } On above code…
A: GIVEN: int cal_media(){cout<<"Enter the name"<<endl;cin>>name;cout<<"Enter…
Q: Define a struct Single that describes the bit layout for a single-precision floating-point number.…
A: The answer is given below:-
Q: Q2. Find the errors in each of the following code segments and correct it 1. #define Pl=3.14; 2.…
A:
Q: Write a procedure called HexOutput that displays the content of register EBX as a hexadecimal…
A: INCLUDE Irvine32.inc .data strPrompt BYTE "What do you want to do, Lovely?",0…
Q: 4. Write down a regular expression for floating point numbers in Scientific notation. First write a…
A: Regular expression for floating point numbers in scientific notation
Q: 1. Any character is entered through the keyboard, write a program to determine whether the character…
A: Pseudocode: Input character checks if the character is a Capital letter (A-Z) checks if the…
Q: Character arrays and pointers in C: I have to search and sort through an EXTREMELY large text file…
A:
Q: Binary numbers are inconvenient because they're too long and not easy to read. Write C+ code that…
A: Here I have created a function named binaryToDecimal(), which takes the input parameter as a binary…
Q: Soundex System Soundex is a system that encodes a word into a letter followed by three digtis that…
A: Form1.visual basic Public Class Form1Private Sub ButtonEncode_Click(sender As Object, e As…
Q: c++ using simple parallel arrays and a random number generator. one string should have [rock, paper,…
A: Code: #include <iostream>using namespace std; // Constant variablesconst char roCK =…
Q: Postfix notation is a way of writing expression without using parentheses. For example, the…
A: Actually, Java is a programming language originally developed by James Gosling at Sun Microsystems…
Q: Sum of Even Numbers: Complete the code below to get the sum of all even numbers from M tO N (all…
A: mov byte[sum] ,0 ; initializes sum=0 mov cl, bye[M] ;initializes counter to M mov…
Q: (C PROGRAMMING ONLY) 1. Pointing Fingers by CodeChum Admin I am so mad at my brothers, they always…
A: Assign address pointer to each of the input variables in c programing
Q: Write the python syntax for implementing a backward finite difference scheme for the right most…
A: Write the python syntax for implementing a backward finite difference scheme for the right most…
Q: Example code structure for how to find the total number of characters in 2 seperate strings at once…
A: In this Programming question we have to determine code and output of number of characters in 2…
Q: lect a e notation for the following code fragment
A: Theta notation means the time complexity of the given code. It defines the number of iteration the…
Q: Explain with an example the situation where using read() is appropriate and also an example where…
A: A file is storage place where data is stored. Python has many functions to read the content in…
Q: 1) largest Write a function int largest(int al],int n) that will find the largest int in the n ints…
A: Find the code implementation below.
Q: e equivalent decimal value in the two cases of representation: signed and unsigned integer,…
A: Positive numbers (including zero) are interpreted as unsigned numbers in mathematics. That is, the…
Q: 1. Sort the following binary operators in order of high to low precedence ,* ,- ,+: 2. Write a C++…
A: 1) The order of precedence in order of high to low is as follows: * > + > -…
Q: Using C (NOT C++,C#) I need help in coding this practice problem without the use of Strings and…
A: Doing this opearation without array or the string is very easy , We can take the input from the…
Q: Write in C Language Description Give you a matrix. Please output the elements in clockwise spiral…
A: Introduction of the Program: The C program takes the number of rows and columns from the user as…
Q: Provide your own short C++ code example that uses Searching and Sorting Arrays
A: array in c++ is use to store multiple values of same data type in contiguous manner. syntax:…
Q: A palindrome is a string that reads the same in its reverse. For example maam, wow, racecar, madam…
A: The code is written below for you problem: #include <string.h> // header files #include…
Q: C programming( I have asked this in C programming not C++. I have gotten this in C++ I want it in C…
A: The answer is given below:-
Q: 2. LEGV8 coding (a) For the following C statement, write the corresponding LEGV8 assembly code.…
A:
Q: Solve the following C++ question correctly please experts. Perform operator overloading for both…
A: Sample Response: //C++ program to perform operator overloading for addition, subtraction,…
Q: problem. A character string that represents the number n, a number b1 that represents the base on…
A: It is defined as a powerful general-purpose programming language. It is used in web development,…
Q: Solve the following C++ question correctly please. Perform operator overloading for both unary and…
A: Required: Solve the following C++ question correctly please. Perform operator overloading for both…
Q: Draw a C++ string descriptor. Illustrate how the storage and the string value in that storage is…
A: ALGORITHM:- 1. Take input for a string. 2. Store its value. 3. Print the result. 4. Finish.
Q: C++ Programming Make a source code using C++ Programming 11. Body Mass Index by CodeChum Admin…
A: As per our guideline, we can answer only 3 questions. Question 11 The first question takes two…
Q: Use C++ coding A palindrome is a number or a text phrase that reads the same backwards as forwards.…
A: PROGRAM CODE: #include <stdio.h> int main() { int n, a, b, c, d, e; int digit = 0;…
Q: Answer in Java Tim while preparing for his CAT exam, was studying the topic Number Systems. He…
A: import java.util.Scanner;//to readinputpublic class Main{ //method to find highest common factors…
Q: Define a struct Single that describes the bit layout for a single-precision floating-point number.…
A: Answer: I have given answer in the brief explanation
Q: Q3- What do you mean by sequential code, self complementing code, cyclic code. Give the one example…
A: Sequential Code - In case of seq. code, each succeeding code is one binary no. greater than the…
Q: en inline, bl
A: The difference between inline, block and inline-block?
Q: code required in mips programming language a .s or .asm code not a c code. Write a MIPS procedure…
A: #include <stdio.h>#include <string.h>#define MAX_SIZE 40 // Maximum string size…
Q: QUESTION 8.14: User input of salary and response that is a calculation for the user maximum…
A: Declare the macros like TENPERCENT, EIGHTPERCENT, and FIVEPERCENT initially so whenever these values…
Q: stion) The following character string is to be transmitted using dynamic Huffman coding: BABIATA…
A: Task : Given String : BABIATA The task is to derive the Huffman code tree.
Q: QI) Write a complete program to convert Decimal number to Binary number by using suitable data…
A: Algorithm: Store the remainder when the number is divided by 2 in an array. Divide the number by 2…
Q: Computer Engineering Lab The Government of United States of America has decided to issue new…
A: Program Explanation First-line contains T the number of test-cases. Every test-case contains an…
Q: function avg and pass x and y printi (the avg of x and y is din', avgl) give_sqrt (avgl); return 0,…
A: There is one C program given with some blanks. We have to fill those blanks so that it can display…
Q: Computer Science code in c++ please .Do NOT use ANY string/character manipulation or…
A: Given The answer is given below.
Q: convert this in C language #include using namespace std; int main() { cout << 1 << "," << 5;…
A: Here I have used a print statement to print the integers 1 and 5 separated by a comma. Next, I have…
Q: Assume these declarations in C/C++: int32_t Func(int32_t a); int32_t Array[65536]; int32_t b;…
A: Given : int32_t Func(int32_t a); int32_t Array[65536]; int32_t b; int32_t a;…
What is the process of writing these odd numbers in this 12-bit floating point representation
Trending now
This is a popular solution!
Step by step
Solved in 9 steps with 8 images

- code in java pls Summary: Given integer values for red, green, and blue, subtract the gray from each value. Computers represent color by combining the sub-colors red, green, and blue (rgb). Each sub-color's value can range from 0 to 255. Thus (255, 0, 0) is bright red, (130, 0, 130) is a medium purple, (0, 0, 0) is black, (255, 255, 255) is white, and (40, 40, 40) is a dark gray. (130, 50, 130) is a faded purple, due to the (50, 50, 50) gray part. (In other words, equal amounts of red, green, blue yield gray). Given values for red, green, and blue, remove the gray part. Ex: If the input is: 130 50 130 the output is: 80 0 80 Find the smallest value, and then subtract it from all three values, thus removing the gray.09.coded in it When analyzing data sets, such as data for human heights or for human weights, a common step is to adjust the data. This adjustment can be done by normalizing to values between 0 and 1, or throwing away outliers. For this program, adjust the values by dividing all values by the largest value. The input begins with an integer indicating the number of floating-point values that follow. Output each floating-point value with two digits after the decimal point, which can be achieved as follows:print(f'{your_value:.2f}') Ex: If the input is: 5 30.0 50.0 10.0 100.0 65.0 the output is: 0.30 0.50 0.10 1.00 0.65..We usually write numbers in decimal form (or base 10), meaning numbers are composed using 10 different “digits” {0,1,…,9}.{0,1,…,9}. Sometimes though it is useful to write numbers hexadecimal or base 16. Now there are 16 distinct digits that can be used to form numbers: {0,1,…,9,A,B,C,D,E,F}.{0,1,…,9,A,B,C,D,E,F}.So for example, a 3 digit hexadecimal number might be 2B8. How many 2-digit hexadecimals start with a letter (A-F) or end with a numeral (0-9) (or both)?
- C programming( I have asked this in C programming not C++. I have gotten this in C++ I want it in C programming) The field of astronomy has been significantly advanced through the use of computer technology. Algorithms can automatically survey digital images of the night sky, looking for new patterns. For this problem, you should write such an analysis program which counts the number of stars visible in an bitmap image. An image consists of pixels, and each pixel is either black or white (represented by the characters # and -, respectively). All black pixels are considered to be part of the sky, and each white pixel is considered to be part of a star. White pixels that are adjacent vertically or horizontally are part of the same star. Input Each test case begins with a line containing a pair of integers 1≤m, n≤100. This is followed by mm lines, each of which contains exactly nn pixels. Input contains at least one and at most 50 test cases, and input ends at the end of file. Output…Soundex System Soundex is a system that encodes a word into a letter followed by three digtis that roughly describe how the word sounds. That is, similar sounding words have similar four-character codes. For instance, the words carrot and caret are both coded as C123. A slight variation of the Soundex coding algorithm is as follows: 1. Retain the first letter. 2. For the remaining letters, delete all occurrences of a, e, i, o, u, h, y, and w. 3. Replace the letters that remain with numbers so that (a) b, f, p, and v become 1 (b) c, g, j, k, q, s, x, and z become 2 (c) d and t both become 3 (d) l (that is, el) becomes 4 (e) m and n become 5 (f) r becomes 6 4. If the result contains two adjacent identical digits, eliminate the second of them. 5. Keep only the first four characters of what you have left. If you have fewer than four, then add zeros on the end to make the string have length four. Write a program that carries out the algorithm. See Fig. 6.86.Soundex System Soundex is a system that encodes a word into a letter followed by three digtis that roughly describe how the word sounds. That is, similar sounding words have similar four-character codes. For instance, the words carrot and caret are both coded as C123. A slight variation of the Soundex coding algorithm is as follows: 1. Retain the first letter. 2. For the remaining letters, delete all occurrences of a, e, i, o, u, h, y, and w. 3. Replace the letters that remain with numbers so that (a) b, f, p, and v become 1 (b) c, g, j, k, q, s, x, and z become 2 (c) d and t both become 3 (d) l (that is, el) becomes 4 (e) m and n become 5 (f) r becomes 6 4. If the result contains two adjacent identical digits, eliminate the second of them. 5. Keep only the first four characters of what you have left. If you have fewer than four, then add zeros on the end to make the string have length four. Write a program that carries out the algorithm. See Fig. 6.86. THIS IS DONE IN VISUAL BASIC
- 1. Write a C++ program that takes two binary numbers of 8 bits eachrepresented with the letters Z and O (for zero or one) and displays thesum in binary with Zs and Os. Do this by converting the numbers to ints,adding the its using +, displaying the 3 ints, then converting the sum toZ and Os and displaying the result. 1 a.) Redo number 1, by doing a bit-by-bit addition, not forgetting the carry. 1b.) Write a program to take two numbers represented with romannumerals and display the sum. Assume the sum will be less than 20.Hints: Ask the user to terminate each number with a semicolon and usechars to hold the roman ‘digits’.The numbers are I, II, III IV, V, VI, VII, VIII, IX, X, XI, XII, XIII, XIV, XV…isfive, Change the program to allow the sum to go up to 49 See how large a number you can handle. L is 50, C is 100, M is 1000. Using basic C++ int, char, if- else statements, and switch statements, please! no functions, or strings, or Cmath etc.T/F Bit arrays and bit fields are same.1.8.1: Sphere volume. Using C++ Given sphereRadius, compute the volume of a sphere and assign sphereVolume with the result. Use (4.0 / 3.0) to perform floating-point division, instead of (4 / 3) which performs integer division.Volume of sphere = (4.0 / 3.0) π r3 (Hint: r3 can be computed using *) #include <iostream>#include <iomanip>#include <cmath> using namespace std; int main() { double sphereVolume; double sphereRadius; cin >> sphereRadius; cout << (4.0 / 3.0) * M_PI * sphereRadius * sphereRadius * sphereRadius; cout << fixed << setprecision(2) << sphereVolume << endl; return 0;}
- the odd numbers are the numbers in the sequence 1,3,5,7,9, .... Define the sequence of S - numbers as follows: the first S - number is 1 The second S - number is the sum of the first S - number and the second odd number the third s - number is the sum of the second S- number and the third odd number. the fourth S- number is the sum of the third S- number and the fourth odd number, etc..,... compute the first seven S- numbers. make a note of any patterns you notice. enter the first seven S- numbers as a comma - seperated list: first seven S- numbers = ________________In CORAL LANGUAGE please and thank you! Summary: Given integer values for red, green, and blue, subtract the gray from each value. Computers represent color by combining the sub-colors red, green, and blue (rgb). Each sub-color's value can range from 0 to 255. Thus (255, 0, 0) is bright red, (130, 0, 130) is a medium purple, (0, 0, 0) is black, (255, 255, 255) is white, and (40, 40, 40) is a dark gray. (130, 50, 130) is a faded purple, due to the (50, 50, 50) gray part. (In other words, equal amounts of red, green, blue yield gray). Given values for red, green, and blue, remove the gray part. Ex: If the input is: 130 50 130 the output is: 80 0 80 Hint: Find the smallest value, and then subtract it from all three values, thus removing the gray.Q25. Write about the following, (a) Block codes (b) Convolutional codes (c) Hamming distance.

