
1)
To determine: Whether anyone can read the message.
Introduction:
1)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
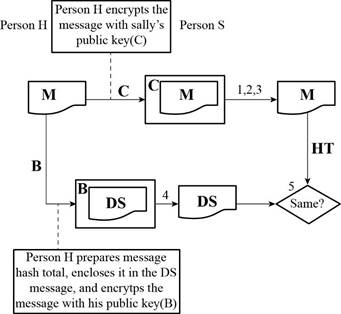
Given diagram:
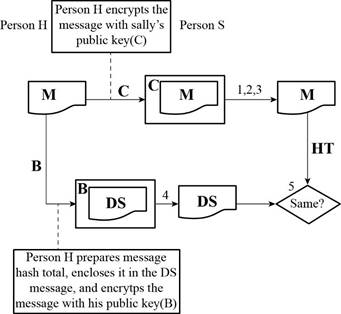
Here,
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether anyone can read the message:
Not everyone can read the message. Only the person who has the private key of Person S can be able to open the message.
2)
To determine: Whether Person S can be sure that the message is from Person H.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
2)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
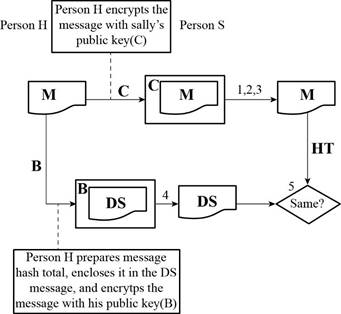
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether Person S can be sure that the message is from Person H:
Anyone with the public key of Person S can be able to send the message
3)
To determine: Whether digital signature message is secret.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
3)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
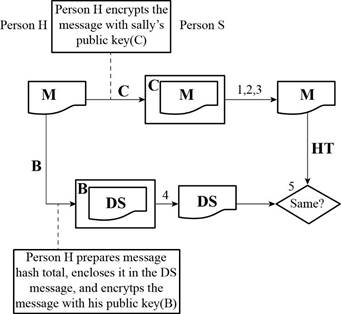
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether a digital signature message is secret:
Anyone with the public key of Person H can be able to open the digital signature message.
4)
To determine: Whether someone other than Person H can send the digital signature message.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
4)
Answer to Problem 2SP
Hence, the answer is No.
Explanation of Solution
Given diagram:
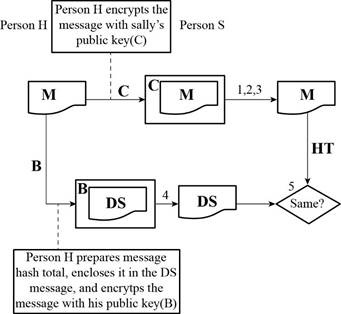
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine whether someone other than Person H can send the digital signature message:
A person with the private key of Person H can be able to send the digital signature message.
5)
To determine: How Person S know that the message has not been corrupted in transit.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
5)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine how Person S know that the message has not been corrupted in transit:
If the hash total of digital signature equals the hash total that Person S calculated from the message then the message has not been corrupted in transit.
6)
To determine: The sub-part that is related to authenticity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
6)
Explanation of Solution
Determine the subpart that is related to authenticity:
Subpart (2) and Subpart (4) are about authenticity.
7)
To determine: The sub-part that is related to integrity.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
7)
Explanation of Solution
Given diagram:

A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to integrity:
Subpart (5) is about integrity.
8)
To determine: The sub-part that is related to confidentiality.
Introduction:
Accounting Information System (AIS) is said to be the specialized subsystem of the Information System (IS). AIS can be used in the business events for the purpose of collecting, processing, and reporting the financial information.
8)
Explanation of Solution
Given diagram:
A refers the public key of Person H
B refers the private key of Person H
C refers the public key of Person S
D refers the private key of Person S
M refers the message
HT refers the hash total
DS refers the digital signature
Determine the subpart that is related to confidentiality:
Subpart (1) and Subpart (3) are about the confidentially.
Want to see more full solutions like this?
Chapter 9 Solutions
Accounting Information Systems
- Listed here are two scenarios. For each scenario, discuss the possible damages that can occur.Suggest a preventive control.A. An intruder taps into a telecommunications device and retrieves the identifying codes andpersonal identification numbers for ATM cardholders. (The user subsequently codes thisinformation onto a magnetic coding device and places this strip on a blank bank card.)B. Because of occasional noise on a transmission line, electronic messages received are extremelygarbled.Problem # 4 (30arrow_forwardRefer to the given system flowchart, and we have discussed the control weakness and the risk associated with these control weaknesses. Based on these control weaknesses and the associated risk, what types of frauds are possible in this business environment.(200 words)arrow_forwardAC. 1. What kind of big data-based fraud prevention product can be used in fraud monitoring? 2. What kind of big data-based fraud prevention product can be used in fraud risk management? Please explain with examplesarrow_forward
- Communication via the internet is fraught with major security problems. When it comes to Internet communications, which of these aspects poses the biggest security risk?arrow_forwardA digital signaturea. is the encrypted mathematical value of the message sender’s name.b. is derived from the digest of a document that has been encrypted with the sender’s private key.c. is derived from the digest of a document that has been encrypted with the sender’s public key.d. is the computed digest of the sender’s digital certificate.e. allows digital messages to be sent over an analog telephone line.arrow_forwardWhat are the risk management happened in the Scandal of Fraud about Wiredcard AGarrow_forward
- The following is a list of 10 common security problems. For each problem, describe why it is a problem and choose a control plan from this chapter that would prevent or detect the problem from occurring. Criminals posing as small business owners obtained names, addresses, and social security numbers from an organization whose business is providing such information only to legitimate customers who have a right to the data. An executive of a financial services firm implements a wireless network so that she can work at home from anywhere in her house. After setting up the network, she logs on using the default password. An organization’s top salesman uses a consumer-grade instant messaging (IM) client (e.g., AOL Instant Messaging). Such clients bypass antivirus and spam software, don’t have auditing and logging capabilities, and allow users to choose their IM names. A financial analyst’s laptop was stolen from his car. The laptop contained the names and social security numbers of…arrow_forwardWhich of the following provides a decentralized database or digital ledger of transactions that everyone on the network can see? a.Block chain technologies b.Crowd funding c.Crypto currencies d.Investment bankingarrow_forwardA group of IT experts disclosed the “internet cookies” vulnerability of your organisation in a recent online security test. Describe to your management the security concerns that “internet cookies” portend?arrow_forward
 Accounting Information SystemsFinanceISBN:9781337552127Author:Ulric J. Gelinas, Richard B. Dull, Patrick Wheeler, Mary Callahan HillPublisher:Cengage Learning
Accounting Information SystemsFinanceISBN:9781337552127Author:Ulric J. Gelinas, Richard B. Dull, Patrick Wheeler, Mary Callahan HillPublisher:Cengage Learning Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning,Principles of Accounting Volume 1AccountingISBN:9781947172685Author:OpenStaxPublisher:OpenStax College
Accounting Information SystemsAccountingISBN:9781337619202Author:Hall, James A.Publisher:Cengage Learning,Principles of Accounting Volume 1AccountingISBN:9781947172685Author:OpenStaxPublisher:OpenStax College


