Assignment 7B: Caesar Cipher. One of the simplest methods to encrypt a message is to "shift" the letters by a literal value. For example, if we take the letter 'A' and shift it by 2, we get 'C'. This "substitution cipher" gets its name from the Roman emperor Julius Caesar, who was one of the first person known to encode secret messages this way. For this assignment, you will create a program that prompts the user for a message to encode, as well as an offset to encrypt it with. You will then create and use the following methods:
Assignment 7B: Caesar Cipher. One of the simplest methods to encrypt a message is to "shift" the letters by a literal value. For example, if we take the letter 'A' and shift it by 2, we get 'C'. This "substitution cipher" gets its name from the Roman emperor Julius Caesar, who was one of the first person known to encode secret messages this way. For this assignment, you will create a program that prompts the user for a message to encode, as well as an offset to encrypt it with. You will then create and use the following methods:
Database System Concepts
7th Edition
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Chapter1: Introduction
Section: Chapter Questions
Problem 1PE
Related questions
Question
Solving this problem in the Java language
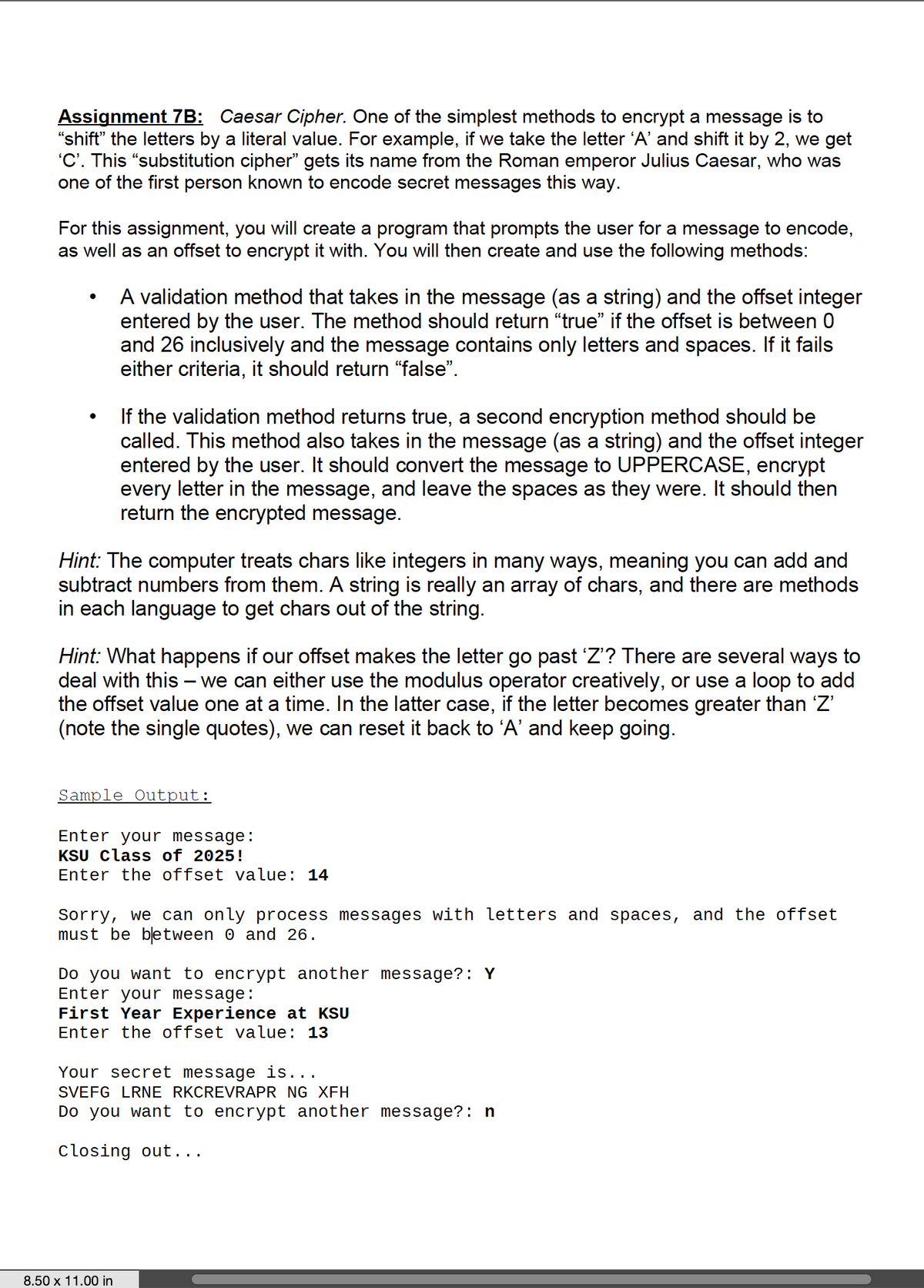
Transcribed Image Text:Assignment 7B: Caesar Cipher. One of the simplest methods to encrypt a message is to
"shift" the letters by a literal value. For example, if we take the letter 'A' and shift it by 2, we get
'C'. This "substitution cipher" gets its name from the Roman emperor Julius Caesar, who was
one of the first person known to encode secret messages this way.
For this assignment, you will create a program that prompts the user for a message to encode,
as well as an offset to encrypt it with. You will then create and use the following methods:
A validation method that takes in the message (as a string) and the offset integer
entered by the user. The method should return "true" if the offset is between 0
and 26 inclusively and the message contains only letters and spaces. If it fails
either criteria, it should return “false".
If the validation method returns true, a second encryption method should be
called. This method also takes in the message (as a string) and the offset integer
entered by the user. It should convert the message to UPPERCASE, encrypt
every letter in the message, and leave the spaces as they were. It should then
return the encrypted message.
Hint: The computer treats chars like integers in many ways, meaning you can add and
subtract numbers from them. A string is really an array of chars, and there are methods
in each language to get chars out of the string.
Hint: What happens if our offset makes the letter go past 'Z'? There are several ways to
deal with this – we can either use the modulus operator creatively, or use a loop to add
the offset value one at a time. In the latter case, if the letter becomes greater than 'Z'
(note the single quotes), we can reset it back to 'A' and keep going.
Sample Output:
Enter your message:
KSU class of 2025!
Enter the offset value: 14
Sorry, we can only process messages with letters and spaces, and the offset
must be between 0 and 26.
Do you want to encrypt another message?: Y
Enter your message:
First Year Experience at KSU
Enter the offset value: 13
Your secret message is...
SVEFG LRNE RKCREVRAPR NG XFH
Do you want to encrypt another message?: n
Closing out...
8.50 x 11.00 in
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 4 steps with 3 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Database System Concepts
Computer Science
ISBN:
9780078022159
Author:
Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:
McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:
9780134444321
Author:
Tony Gaddis
Publisher:
PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:
9780132737968
Author:
Thomas L. Floyd
Publisher:
PEARSON

Database System Concepts
Computer Science
ISBN:
9780078022159
Author:
Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:
McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:
9780134444321
Author:
Tony Gaddis
Publisher:
PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:
9780132737968
Author:
Thomas L. Floyd
Publisher:
PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:
9780133976892
Author:
Paul J. Deitel, Harvey Deitel
Publisher:
PEARSON

Database Systems: Design, Implementation, & Manag…
Computer Science
ISBN:
9781337627900
Author:
Carlos Coronel, Steven Morris
Publisher:
Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:
9780073373843
Author:
Frank D. Petruzella
Publisher:
McGraw-Hill Education