Phishing Site Malware Download Site Warez/Piracy Server Child Pornography Server Spam Site Webmail Spam Stranded Abroad Advance Scams Harvesting E-mail Contact E-mail Attacks Harvesting Associated Accounts Access to Corporate E-mail Web Server Online Gaming Characters Online Gaming Goods/Currency PC Game License Keys Operating System License Key Virtual Goods HACKED PC Spam Zombie Bot Activity DDOS Extortion Zombie Click Fraud Zombie Anonymization Proxy CAPTCHA Solving Zombie eBay/Paypal Fake Auctions Online Gaming Credentials Account Credentials Web Site FTP Credentials Skype/VolP Credentials Client Side Encryption Certificates Financial Credentials Bank Account Data Credit Card Data Stock Trading Account Mutual Fund/401k Account
Phishing Site Malware Download Site Warez/Piracy Server Child Pornography Server Spam Site Webmail Spam Stranded Abroad Advance Scams Harvesting E-mail Contact E-mail Attacks Harvesting Associated Accounts Access to Corporate E-mail Web Server Online Gaming Characters Online Gaming Goods/Currency PC Game License Keys Operating System License Key Virtual Goods HACKED PC Spam Zombie Bot Activity DDOS Extortion Zombie Click Fraud Zombie Anonymization Proxy CAPTCHA Solving Zombie eBay/Paypal Fake Auctions Online Gaming Credentials Account Credentials Web Site FTP Credentials Skype/VolP Credentials Client Side Encryption Certificates Financial Credentials Bank Account Data Credit Card Data Stock Trading Account Mutual Fund/401k Account
Related questions
Question
a)The attackers are always looking for ways to obtain control of a computer connected to the
Internet. Brian Krebs, author of the popular information security blog, krebsonsecurity, has plotted the
possible uses of a compromised PC19 (Figure below).
Internet. Brian Krebs, author of the popular information security blog, krebsonsecurity, has plotted the
possible uses of a compromised PC19 (Figure below).
b)If your PC were compromised, provide a brief description of how your PC could be used by an
attacker to perform any three of the above activities. Be very specific and detailed in your answer
attacker to perform any three of the above activities. Be very specific and detailed in your answer
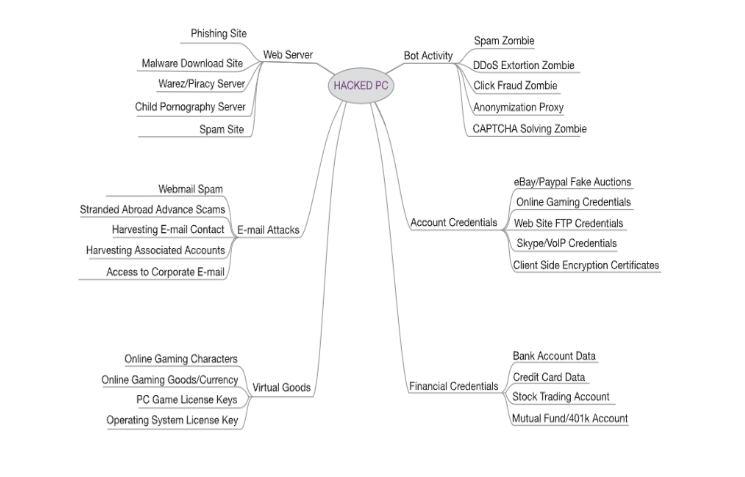
Transcribed Image Text:Phishing Site
Malware Download Site
Warez/Piracy Server
Child Pornography Server
Spam Site
Webmail Spam
Stranded Abroad Advance Scams
Harvesting E-mail Contact E-mail Attacks
Harvesting Associated Accounts
Access to Corporate E-mail
Web Server
Online Gaming Characters
Online Gaming Goods/Currency
PC Game License Keys
Operating System License Key
Virtual Goods
HACKED PC
Spam Zombie
Bot Activity DDOS Extortion Zombie
Click Fraud Zombie
Anonymization Proxy
CAPTCHA Solving Zombie
eBay/Paypal Fake Auctions
Online Gaming Credentials
Account Credentials Web Site FTP Credentials
Skype/VolP Credentials
Client Side Encryption Certificates
Financial Credentials
Bank Account Data
Credit Card Data
Stock Trading Account
Mutual Fund/401k Account
AI-Generated Solution
Unlock instant AI solutions
Tap the button
to generate a solution