A E H D B C F G b) What will be the adjacency matrix of the above mentioned graph?
A E H D B C F G b) What will be the adjacency matrix of the above mentioned graph?
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
Answer 2 b only
Transcribed Image Text:Nilashish RoV
Active 24 minutes ago
31 83% i 9:27 a,m,
E Algo_Final_Sp21..
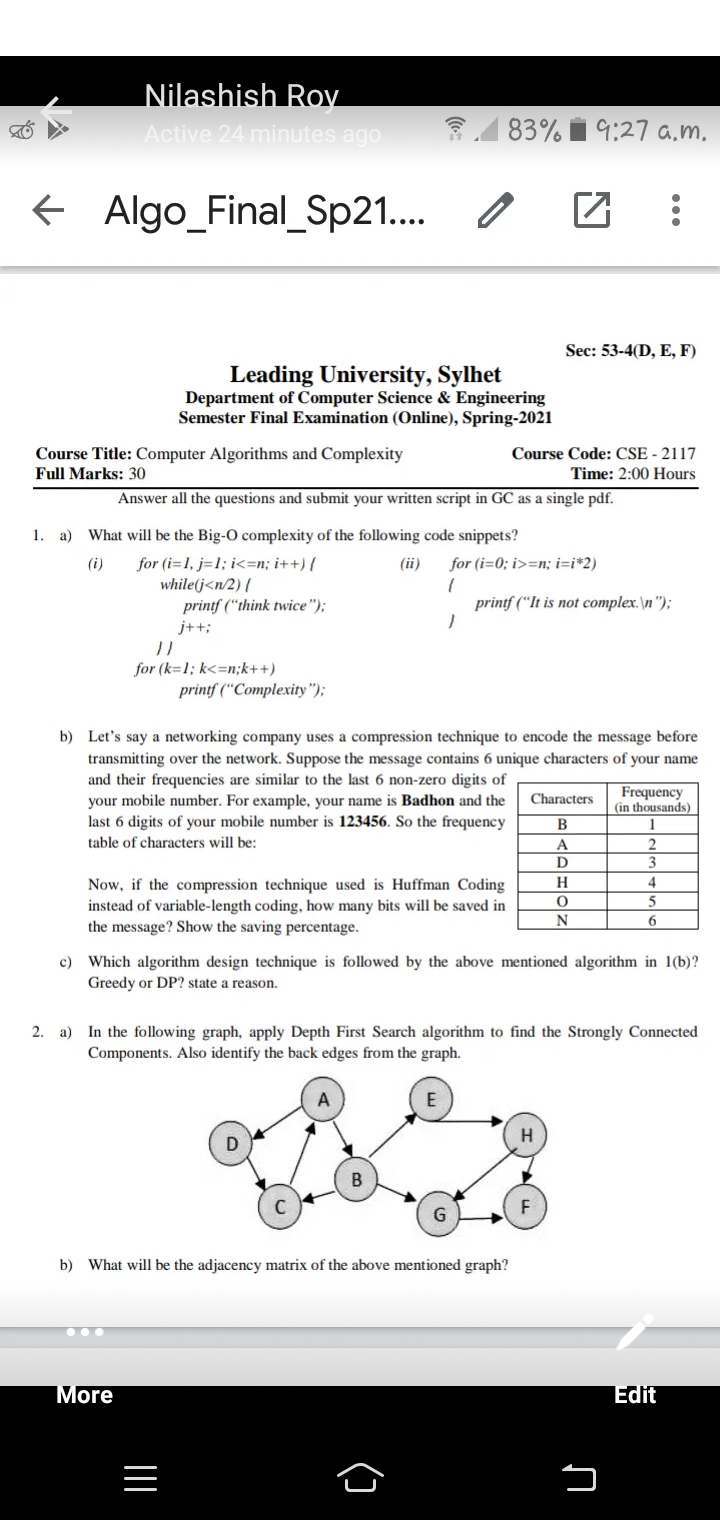
Sec: 53-4(D, E, F)
Leading University, Sylhet
Department of Computer Science & Engineering
Semester Final Examination (Online), Spring-2021
Course Code: CSE - 2117
Course Title: Computer Algorithms and Complexity
Full Marks: 30
Time: 2:00 Hours
Answer all the questions and submit your written script in GC as a single pdf.
1. a) What will be the Big-O complexity of the following code snippets?
for (i=1, j=1; i<=n; i++) {
while(j<n/2) {
printf (“think twice");
(i)
(ii)
for (i=0; i>=n; i=i*2)
printf ("It is not complex.\n");
j++;
for (k=1; k<=n;k++)
printf ("Complexity");
b) Let's say a networking company uses a compression technique to encode the message before
transmitting over the network. Suppose the message contains 6 unique characters of your name
and their frequencies are similar to the last 6 non-zero digits of
your mobile number. For example, your name is Badhon and the
last 6 digits of your mobile number is 123456. So the frequency
Frequency
(in thousands)
Characters
1
table of characters will be:
2
3
A
H.
4
Now, if the compression technique used is Huffman Coding
instead of variable-length coding, how many bits will be saved in
the message? Show the saving percentage.
5
c) Which algorithm design technique is followed by the above mentioned algorithm in 1(b)?
Greedy or DP? state a reason.
2. a) In the following graph, apply Depth First Search algorithm to find the Strongly Connected
Components. Also identify the back edges from the graph.
E
b) What will be the adjacency matrix of the above mentioned graph?
More
Edit
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 2 steps with 1 images

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY