Alice 1. GET Bob's home page 2. Fake home page with ET 3. E-(Message) Trudy 4. EB(Message) Figure 8-25 A way for Trudy to subvert public-key encryption. Bob
Alice 1. GET Bob's home page 2. Fake home page with ET 3. E-(Message) Trudy 4. EB(Message) Figure 8-25 A way for Trudy to subvert public-key encryption. Bob
Fundamentals of Information Systems
8th Edition
ISBN:9781305082168
Author:Ralph Stair, George Reynolds
Publisher:Ralph Stair, George Reynolds
Chapter4: Telecommunications And Networks
Section: Chapter Questions
Problem 5SAT
Related questions
Question
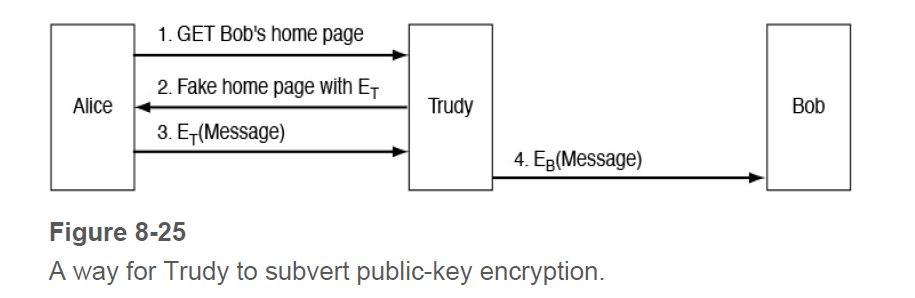
Consider the failed attempt of Alice to get Bob’s public key in
Fig. 8-25 . Suppose that Bob and Alice already share a
secret key, but Alice still wants Bob’s public key. Is there now a
way to get it securely? If so, how?
Transcribed Image Text:Alice
1. GET Bob's home page
2. Fake home page with ET
3. E+(Message)
Trudy
4. Eg(Message)
Figure 8-25
A way for Trudy to subvert public-key encryption.
Bob
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Fundamentals of Information Systems
Computer Science
ISBN:
9781305082168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Fundamentals of Information Systems
Computer Science
ISBN:
9781305082168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning