Alice received the following ciphertext from Bob, "08 01 08 05". Bob had encrypted it using the RSA cypher with Alice's public key (pq, e) = (55, 3), where p = 5 and q = 11. Note that (p-1)(9-1) = 40. The value for d in Alice's private key, (pq, d) is a positive inverse for 3 modulo (p-1)(91). It was found to be 27 in Examples 8.4.8(b) and 8.4.10. What is Bob's message after Alice decrypts it? (Assume Bob encoded one letter at a time using the encoding A = 01, 8 = 02, C = 03, ..., Z = 26.) To decrypt Bob's message, Alice uses the decryption formula mod where M is the code for a letter of the message, C is the encrypted version of the letter, (pq, e) = (55, 3) is the public key, and (pq, d) = (55, 27) is the private key. (a) To begin, Alice computes the values of a, b, c, d and e that are indicated below. 08¹a (mod 55) 082b (mod 55) 084 c (mod 55) 088 Ed (mod 55) 0816e (mod 55) She finds that a = |, C = [ ],d= and e = Because 27 = 16 + 8 + 2 + 1, 0827= 0816 +8+2+1 0816. 088.082.081, she uses the values of a, b, d, and e to compute 0827 mod 55 = (a.b.de) mod 55 = [ Thus, the first letter in Bob's message is 27 mod 55 = (b) Alice finds the second letter of Bob's message by computing (c) What is Bob's message after Alice finishes decrypting it?
Alice received the following ciphertext from Bob, "08 01 08 05". Bob had encrypted it using the RSA cypher with Alice's public key (pq, e) = (55, 3), where p = 5 and q = 11. Note that (p-1)(9-1) = 40. The value for d in Alice's private key, (pq, d) is a positive inverse for 3 modulo (p-1)(91). It was found to be 27 in Examples 8.4.8(b) and 8.4.10. What is Bob's message after Alice decrypts it? (Assume Bob encoded one letter at a time using the encoding A = 01, 8 = 02, C = 03, ..., Z = 26.) To decrypt Bob's message, Alice uses the decryption formula mod where M is the code for a letter of the message, C is the encrypted version of the letter, (pq, e) = (55, 3) is the public key, and (pq, d) = (55, 27) is the private key. (a) To begin, Alice computes the values of a, b, c, d and e that are indicated below. 08¹a (mod 55) 082b (mod 55) 084 c (mod 55) 088 Ed (mod 55) 0816e (mod 55) She finds that a = |, C = [ ],d= and e = Because 27 = 16 + 8 + 2 + 1, 0827= 0816 +8+2+1 0816. 088.082.081, she uses the values of a, b, d, and e to compute 0827 mod 55 = (a.b.de) mod 55 = [ Thus, the first letter in Bob's message is 27 mod 55 = (b) Alice finds the second letter of Bob's message by computing (c) What is Bob's message after Alice finishes decrypting it?
Elements Of Modern Algebra
8th Edition
ISBN:9781285463230
Author:Gilbert, Linda, Jimmie
Publisher:Gilbert, Linda, Jimmie
Chapter2: The Integers
Section2.7: Introduction To Coding Theory (optional)
Problem 12E: Suppose that the check digit is computed as described in Example . Prove that transposition errors...
Related questions
Question
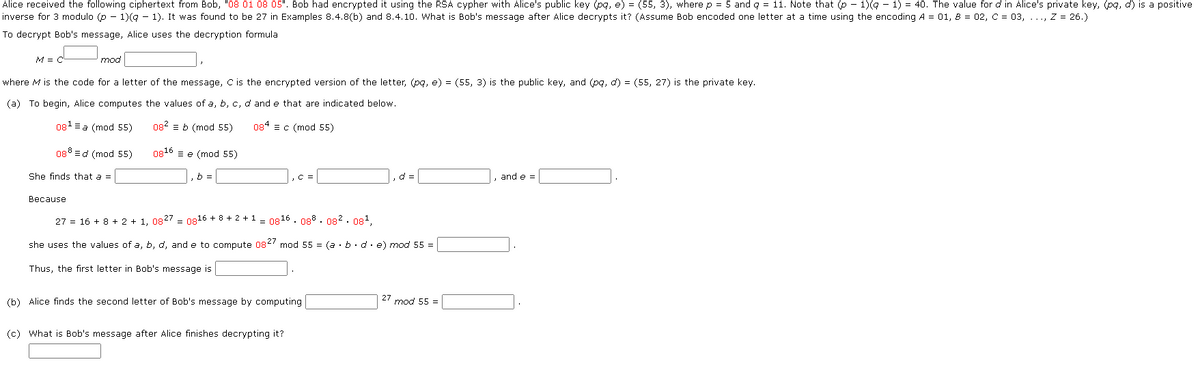
Transcribed Image Text:Alice received the following ciphertext from Bob, "08 01 08 05". Bob had encrypted it using the RSA cypher with Alice's public key (pq, e) = (55, 3), where p = 5 and q = 11. Note that (p − 1)(q − 1) = 40. The value for d in Alice's private key, (pq, d) is a positive
inverse for 3 modulo (p − 1)(q − 1). It was found to be 27 in Examples 8.4.8(b) and 8.4.10. What is Bob's message after Alice decrypts it? (Assume Bob encoded one letter at a time using the encoding A = 01, 8 = 02, C = 03, ..., Z = 26.)
To decrypt Bob's message, Alice uses the decryption formula
M = C
mod
where M is the code for a letter of the message, C is the encrypted version of the letter, (pq, e) = (55, 3) is the public key, and (pq, d) = (55, 27) is the private key.
(a) To begin, Alice computes the values of a, b, c, d and e that are indicated below.
084 c (mod 55)
08¹ = a (mod 55)
088 d (mod 55)
She finds that a =
082 b (mod 55)
0816e (mod 55)
b =
, C =
d=
and e =
Because
27 = 16 + 8 + 2 + 1, 0827= 0816 +8+2+1 = 0816. 088.082.08¹,
she uses the values of a, b, d, and e to compute 0827 mod 55 = (a.b.de) mod 55 =
Thus, the first letter in Bob's message is
27 mod 55 =
(b) Alice finds the second letter of Bob's message by computing
(c) What is Bob's message after Alice finishes decrypting it?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 2 images

Recommended textbooks for you

Elements Of Modern Algebra
Algebra
ISBN:
9781285463230
Author:
Gilbert, Linda, Jimmie
Publisher:
Cengage Learning,

Elements Of Modern Algebra
Algebra
ISBN:
9781285463230
Author:
Gilbert, Linda, Jimmie
Publisher:
Cengage Learning,