Analysis 1. From previous work with Boris and Natasha, you know that their encoding and decoding functions are always linear and have 1 as the coefficient of x. Write the general form of the linear function that could be used to decode the message.
Analysis 1. From previous work with Boris and Natasha, you know that their encoding and decoding functions are always linear and have 1 as the coefficient of x. Write the general form of the linear function that could be used to decode the message.
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
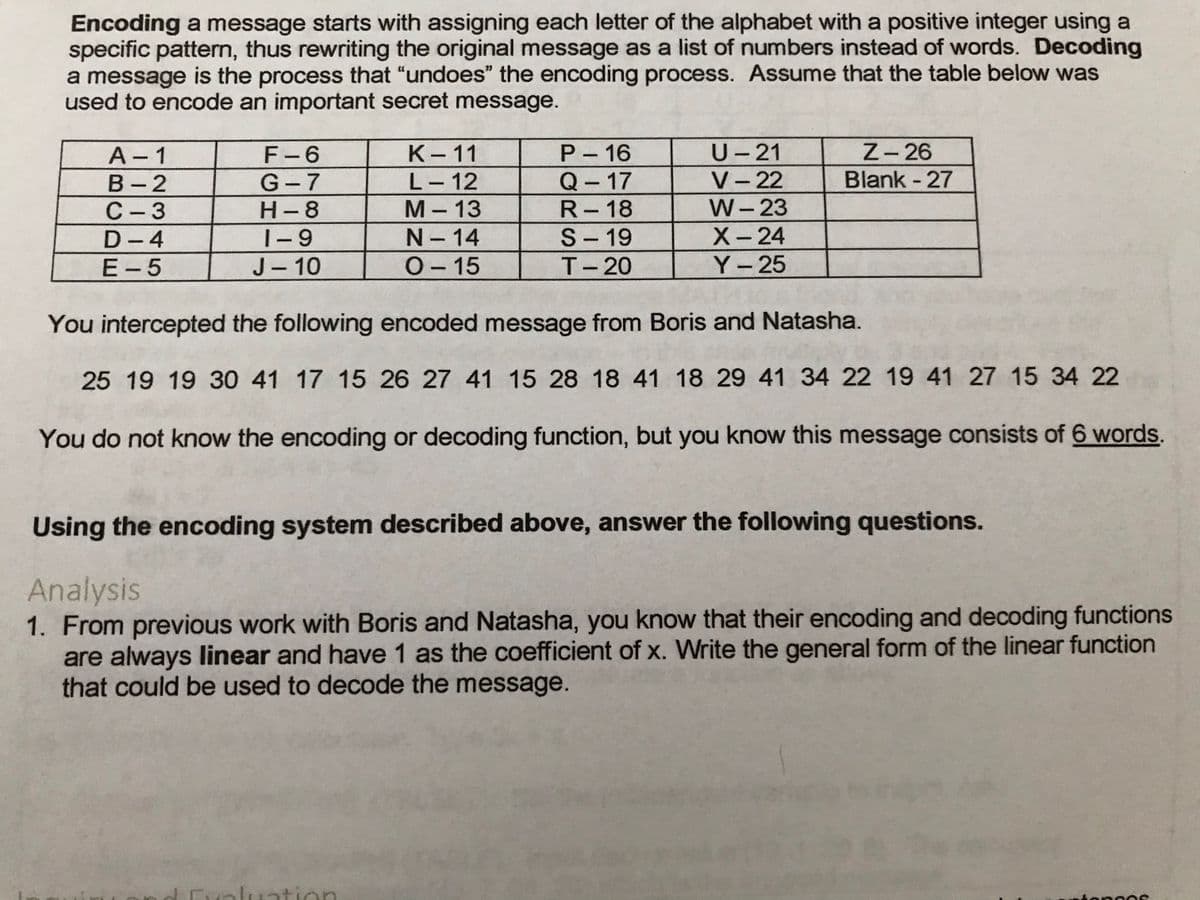
Transcribed Image Text:Encoding a message starts with assigning each letter of the alphabet with a positive integer using a
specific pattern, thus rewriting the original message as a list of numbers instead of words. Decoding
a message is the process that "undoes" the encoding process. ASsume that the table below was
used to encode an important secret message.
Z- 26
A - 1
В - 2
С — 3
D- 4
E- 5
U-21
V- 22
W- 23
F-6
К-11
P- 16
Blank - 27
G-7
H-8
L-12
M- 13
Q-17
R- 18
|-
1-9
N- 14
S-19
X-24
J- 10
О-15
T-20
Y-25
You intercepted the following encoded message from Boris and Natasha.
25 19 19 30 41 17 15 26 27 41 15 28 18 41 18 29 41 34 22 19 41 27 15 34 22
You do not know the encoding or decoding function, but you know this message consists of 6 words.
Using the encoding system described above, answer the following questions.
Analysis
1. From previous work with Boris and Natasha, you know that their encoding and decoding functions
are always linear and have 1 as the coefficient of x. Write the general form of the linear function
that could be used to decode the message.
aluntion
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 2 images

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY