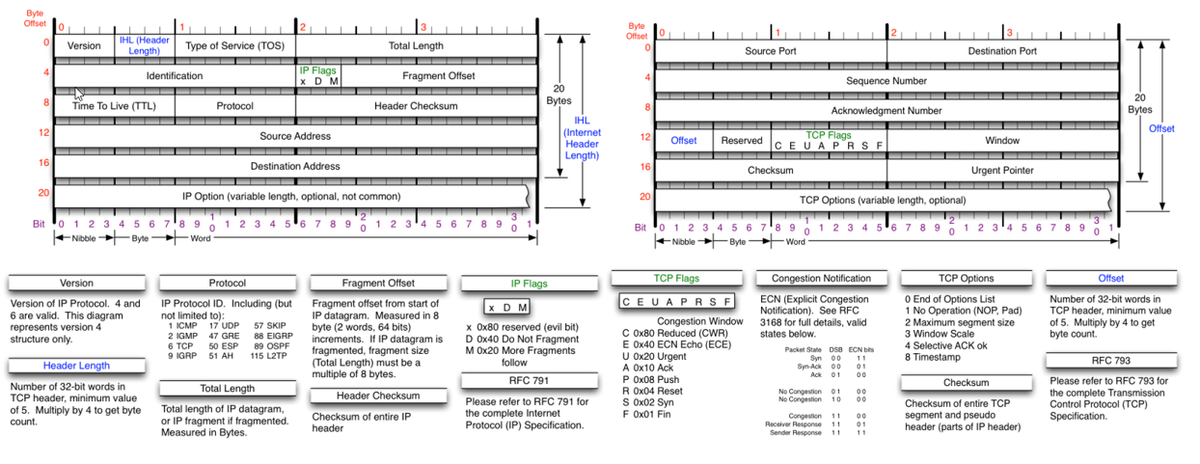
Answers should all be in lowercase with no spaces between hex characters when hexadecimal is the answer expected. All hex values must start with 0x, which stands for hexadecimal and therefore include 0x in your answers. Q1: What Transport protocol is encapsulated in the packet trace? Answer: The Transport protocol is encapsulated in the packet trace is: Q2. What is the value in hexadecimal of the Destination port address? Answer: The value in hexadecimal of the Destination Port Address is: Q3: What is the value in hexadecimal of the Transport header Checksum? Answer: The value in hexadecimal of the Transport header Checksum is: Q4: What is the value in hexadecimal of the Sequence Number? Answer: The value in hexadecimal of the Sequence Number is: Q5: What is the value in hexadecimal of the Source Transport Port Address? Answer: The value in hexadecimal of the Source Port Address is:
Answers should all be in lowercase with no spaces between hex characters when hexadecimal is the answer expected.
All hex values must start with 0x, which stands for hexadecimal and therefore include 0x in your answers.
Q1: What Transport protocol is encapsulated in the packet trace?
Answer: The Transport protocol is encapsulated in the packet trace is:
Q2. What is the value in hexadecimal of the Destination port address?
Answer: The value in hexadecimal of the Destination Port Address is:
Q3: What is the value in hexadecimal of the Transport header Checksum?
Answer: The value in hexadecimal of the Transport header Checksum is:
Q4: What is the value in hexadecimal of the Sequence Number?
Answer: The value in hexadecimal of the Sequence Number is:
Q5: What is the value in hexadecimal of the Source Transport Port Address?
Answer: The value in hexadecimal of the Source Port Address is:
![Ox0000: 4500 0611 66f9 4000 4006 c697 c0a8 e782 E...f.@.@..
Ox0010: 6b14 f416 9a88 0lbb bc20 5fld 15b9 654e k.
Ox0020: 5018 ab40 Od5a 0000 1703 0305 e400 0000 P..@.Z.
Ox0030: 0000 0000 037e d222 445d 3b59 5dc4 feea
Ox0040: ebc1 b5a6 39c8 a333 d716 2682 17c8 08ec
Ox0050: 7d39 8f87 2d13 0fa7 ebla 2cla 00c1 6bcd }9..
Ox0060: d4c1 de38 4862 a382 039c 83bd d390 ld9f
eN
"D];Y].
9..3..&..
.k.
....
...8Hb.
Ox0070: 3a05 e656 3740 bcb7 eded 72a3 9db9 fb66 :..V7@.
..r.
Ox0080: 3bfO 5f3f d579 095c 861c 2727 132d de0a
;._?.y.\..
Ox0090:
Оx00а0:
9067 db12 9204 c38d d413 5d4d 78bd 95e0
6f52 3900 9fac c59c 9df5 60fe 1901 37db oR9.
. ]Mx...
..7.
.g.
Оx00b0: f34a fbe5 5f52 сlа4 2ff5 67е3 9bdf 66f7
.J.. R../.g...f.](/v2/_next/image?url=https%3A%2F%2Fcontent.bartleby.com%2Fqna-images%2Fquestion%2F53e6c2af-4fe9-4776-a12b-71c4c9cd69aa%2Fd9a361dc-5acf-4d45-8b90-ea09c899083f%2F7n1c6i_processed.png&w=3840&q=75)
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 1 images









