b) Suppose a bank organization MyBank has designed a system in which a symmetric session key is established as below. the user's browser generates a 128-bit random key, K user's browser sends K to the server by encrypting it with the server's public key In terms of providing forward secrecy, do you think that the approach used for the session key establishment is appropriate? If your answer is YES, provide details to support your answer. If your answer is NO, explain why and what would you recommend instead to achieve forward secrecy.
b) Suppose a bank organization MyBank has designed a system in which a symmetric session key is established as below. the user's browser generates a 128-bit random key, K user's browser sends K to the server by encrypting it with the server's public key In terms of providing forward secrecy, do you think that the approach used for the session key establishment is appropriate? If your answer is YES, provide details to support your answer. If your answer is NO, explain why and what would you recommend instead to achieve forward secrecy.
Database System Concepts
7th Edition
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Chapter1: Introduction
Section: Chapter Questions
Problem 1PE
Related questions
Question

Transcribed Image Text:b) Suppose a bank organization MyBank has designed a system in which a symmetric
session key is established as below.
the user's browser generates a 128-bit random key, K
user's browser sends K to the server by encrypting it with the server's public key
In terms of providing forward secrecy, do you think that the approach used for the
session key establishment is appropriate?
If your answer is YES, provide details to support your answer.
If your answer is NO, explain why and what would you recommend instead to
achieve forward secrecy.
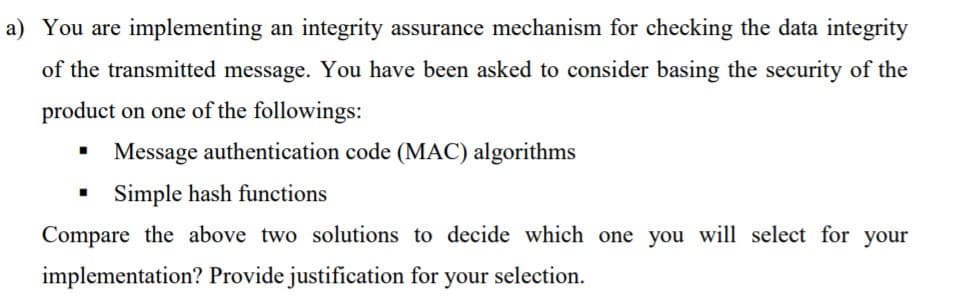
Transcribed Image Text:a) You are implementing an integrity assurance mechanism for checking the data integrity
of the transmitted message. You have been asked to consider basing the security of the
product on one of the followings:
Message authentication code (MAC) algorithms
Simple hash functions
Compare the above two solutions to decide which one you will select for your
implementation? Provide justification for your selection.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Database System Concepts
Computer Science
ISBN:
9780078022159
Author:
Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:
McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:
9780134444321
Author:
Tony Gaddis
Publisher:
PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:
9780132737968
Author:
Thomas L. Floyd
Publisher:
PEARSON

Database System Concepts
Computer Science
ISBN:
9780078022159
Author:
Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:
McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:
9780134444321
Author:
Tony Gaddis
Publisher:
PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:
9780132737968
Author:
Thomas L. Floyd
Publisher:
PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:
9780133976892
Author:
Paul J. Deitel, Harvey Deitel
Publisher:
PEARSON

Database Systems: Design, Implementation, & Manag…
Computer Science
ISBN:
9781337627900
Author:
Carlos Coronel, Steven Morris
Publisher:
Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:
9780073373843
Author:
Frank D. Petruzella
Publisher:
McGraw-Hill Education