c. Suppose Alice computes the Secret suffix MAC (page 322: secret suffix MAC(x) = h(x || key)) for the message ”AM” with key “G” that both Alice and Bob know. The hash function that is used is h(x1x2x3)= g(g(x1 XOR x2) XOR x3 ) where each xi is a character represented as 8 bits, and g(x) is a 8-bit string that is equal to the complement of bits in x. For example, g(10110011) = 01001100. The MAC is 8 bits. (8-bit ASCII representation of the characters is given below.) What is the Secret suffix MAC computed by Alice? Show the MAC as the single character. What information is sent by Alice to Bob.
**Please do C**
**C IS different from B**
a.
Compute CBC-MAC for a message of 16 bits, “8642” (in Hexa). Assume a block size of 8 bits with an IV=F1 (in hexa). For simplicity, assume the encryption to be a simple XOR of the key with the plaintext. Let the encryption key be B4 (in Hexa).
- What is the Secret prefix MAC computed by Alice? Show the MAC as the single character.
- What information is sent by Alice to Bob?
c.
Suppose Alice computes the Secret suffix MAC (page 322: secret suffix MAC(x) = h(x || key)) for the message ”AM” with key “G” that both Alice and Bob know. The hash function that is used is h(x1x2x3)= g(g(x1
XOR x2) XOR x3 ) where each xi is a character represented as 8 bits, and g(x) is a 8-bit string that is equal to the complement of bits in x. For example, g(10110011) = 01001100. The MAC is 8 bits. (8-bit ASCII representation of the characters is given below.)
-
- What is the Secret suffix MAC computed by Alice? Show the MAC as the single character.
- What information is sent by Alice to Bob.
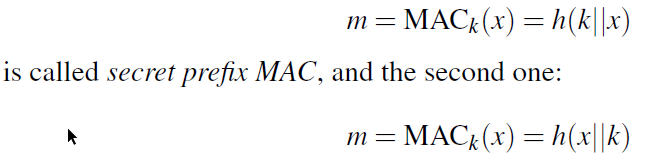
![Dec Hx Oct Char
Dec Hx Oct Html Chr
Dec Hx Oct Html Chr Dec Hx Oct Html Chr
0 000 NUL (null)
1 001 SOH (start of heading)
2 002 STX (start of text)
3 003 ETX (end of text)
4 004 EOT (end of transmission)
32 20 040   Space 64 40 100 @ @
3321 041 ! !
96 60 140 `
65 41 101 A A
97 61 141 a
98 62 142 b b
99 63 143 c
100 64 144 d d
69 45 105 E E 101 65 145 e e
70 46 106 F F 102 66 146 G#102; f
71 47 107 G G 103 67 147 G#103; g
72 48 110 H H 104 68 150 h h
105 69 151 i i
106 6A 152 j j
75 4B 113 K K 107 6B 153 k k
108 6C 154 l 1
109 6D 155 m m
a
rr
2.
34 22 042 "
66 42 102 B B
35 23 043 G#35; #
3624044 $ $
67 43 103 C C
68 44 104 D D
3
4
5 5 005 ENQ (enquiry)
37 25 045 % *
6 006 ACK (acknowledge)
7 007 BEL (bell)
8 010 BS
9 011 TAB (horizontal tab)
À 012 LF
в 013 VT
C 014 FF
D 015 CR
E 016 SO
F 017 SI
38 26 046 & &
7
39 27 047 ' '
40 28 050 G#40;
41 29 051 ) )
(NL line feed, new line) 42 2A 052 * *
43 2B 053 G#43; +
(NP form feed, new page) 44 2C 054 , ,
45 2D 055 -
46 2E 056 .
47 2F 057 G#47; /
48 30 060 0 0
(backspace)
73 49 111 I I
74 4A 112 J J
10
11
(vertical tab)
12
76 4C 114 L L
77 4D 115 M M
78 4E 116 N N
79 4F 117 O 0
80 50 120 P P
81 51 121 Q Q 113 71 161 q q
82 52 122 R R 11472 162 r r
13
(carriage return)
(shift out)
(shift in)
110 6E 156 n n
1l1 6F 157 &#lll; o
112 70 160 p p
14
15
16 10 020 DLE (data link escape)
17 11 021 Dci (device control 1)
18 12 022 DC2 (device control 2)
19 13 023 DC3 (device contrd 3)
20 14 024 DC4 (device controf 4)
21 15 025 NAK (negative acknowledge)
22 16 026 SYN (synchronous idle)
23 17 027 ETB (end of trans. block)
24 18 030 CAN (cancel)
25 19 031 EM
26 lA 032 SUB (substitute)
27 1B 033 ESC (escape)
28 10 034 FS
29 1D 035 GS
30 IE 036 RS
31 1F 037 US
49 31 061 1 1
50 32 062 2 2
51 33 063 3 3
52 34 064 4 4
53 35 065 5 5
83 53 123 S S
115 73 163 s s
84 54 124 T T 1l6 74 164 t t
85 55 125 U U 117 75 165 u u
86 56 126 V v 118 76 166 v v
54 36 066 6 6
55 37 067 7 7
56 38 070 G#56; 8
87 57 127 W W
119 77 167 w w
88 58 130 X X 120 78 170 x x
89 59 131 Y Y 121 79 171 y Y
90 5A 132 Z Z
91 5B 133 [ [
92 5C 134 \ \
(end of medium)
57 39 071 9 9
58 3A 072 : :
59 3B 073 ; ;
60 3C 074 G#60; <
61 3D 075 = =
62 3E 076 > >
63 3F 077 ? ?
122 7A 172 z z
(file separator)
(group separator)
(record separator)
(unit separator)
123 7B 173 { {
124 7C 174 | |
125 7D 175 } }
126 7E 176 ~
127 7F 177  DEL
Source: www.Lookup Tables.com
93 5D 135 ] ]
94 5E 136 ^ *
95 5F 137 _](/v2/_next/image?url=https%3A%2F%2Fcontent.bartleby.com%2Fqna-images%2Fquestion%2Fa124edfc-6a79-4450-9c47-a7b22302255e%2F14d1cd8c-22be-45e6-bc9b-e9b2c250b9b0%2Fs9pxcpo_processed.png&w=3840&q=75)
Step by step
Solved in 2 steps with 2 images









