Cy-a Encrypt Encrypt Encrypt (a) Eneryption Decrypt Decrypt Decrypt (b) Decryption Figure 2: Cipher Block Chaining Mode
Cy-a Encrypt Encrypt Encrypt (a) Eneryption Decrypt Decrypt Decrypt (b) Decryption Figure 2: Cipher Block Chaining Mode
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
100%
c) AES and DES are the two widely used block-ciphers in symmetric cryptography. For every following component of DES, state the comparable element in AES, or describe why it is not required/used in AES.
i) XOR of the f function output with the left half of the block
ii) The f function
iii) Permutation P
iv) Swapping of halves of the block
![ASCII Table
Char
Oct
Hex | Char
Dec
Oct
Hex | Char
Dec
Dec
Oct
Нех
Ox20 | @
Ox21 | A
Ox22 | B
Ох23 | С
Ox24 | D
Ох25 | E
0046 Ox26 | E
Ox27 | G
Ох28 | Н
Ох29 | 1
Ox2a i J
Ox2b | K
Ох2с | L
Ox2d | M
Ox2e | N
Ox2f | 0
Ох30 | P
Ox31 | Q
Ox32 | R
Ox33 i s
Ох34 | T
Ox35 | U
Ox36 | v
Ox37 | W
Ох38 | X
Ox39 | Y
ОхЗа | Z
Ox3b
Ох3с |
Ox3d | ]
Ox3e |
Ox3f |
Ox40 |
Ox41 | a
Ox42 | b
Ox43 | C
Ox44 | d
Ox45 | e
Ox46 | f
Ox47 | g
Ox48 | h
Ох49 | i
Ox4a | j
Ox4b | k
Ox4c ||
Ox4d | m
Ox4e | n
Ox4f | o
Ox50 | p
Ох51 | q
Ox52 |r
Ox53 | s
Ox54 it
Ox55 | u
Ox56 | v
Ox57 | w
Ox58 | x
Ox59 | y
Ох5а | z
Ox5b | {
Ox5c ||
Ox5d | }
Ox5e |
Ox5f
(sp)
32
0040
64
0100
96
0140
0141
0142
0143
0144
0145
0146
0147
Ox60
Ох61
Ox62
Ох63
Ох64
Ox65
Ох66
Ох67
Ох68
Ox69
Охба
Ox6b
33
34
35
36
37
38
39
0041
0042
0043
0044
0045
65
66
67
68
69
70
71
0101
0102
0103
0104
0105
0106
0107
97
98
99
100
101
102
103
#3
&
0047
40
41
42
43
44
45
46
47
0050
0051
0052
0053
0054
0055
0056
0057
72
73
74
75
76
77
78
79
0110
0111
0112
0113
0114
0115
0116
104
105
106
107
108
109
110
111
0150
0151
0152
0153
0154
0155
0156
0157
Охбс
Ox6d
Охбе
0117
Ox6f
48
49
50
51
52
53
54
55
0060
0061
0062
0063
0064
0065
0066
0067
80
81
82
83
84
85
86
87
0160
0161
0162
0163
0164
0165
0166
0167
0120
0121
0122
0123
0124
0125
0126
0127
0130
0131
0132
0133
0134
0135
0136
0137
112
113
114
115
116
117
118
119
Ox70
071
Ox72
Ox73
Ox74
Ox75
Ox76
Ox77
1
4
6.
56
57
58
59
60
61
62
63
0070
0071
0072
0073
0074
0075
0076
88
89
90
91
92
93
94
95
0170
0171
0172
0173
0174
0175
0176
120
121
122
123
124
125
126
Ox78
Ox79
Ox7a
Ox7b
Ox7c
Ox7d
Ox7e
>
0077](/v2/_next/image?url=https%3A%2F%2Fcontent.bartleby.com%2Fqna-images%2Fquestion%2Fba4626c0-7bfb-4f90-a884-5d952bb6fb24%2F84f4c245-5f72-493f-a4e9-ea389f70c42a%2Fxn7caw_processed.png&w=3840&q=75)
Transcribed Image Text:ASCII Table
Char
Oct
Hex | Char
Dec
Oct
Hex | Char
Dec
Dec
Oct
Нех
Ox20 | @
Ox21 | A
Ox22 | B
Ох23 | С
Ox24 | D
Ох25 | E
0046 Ox26 | E
Ox27 | G
Ох28 | Н
Ох29 | 1
Ox2a i J
Ox2b | K
Ох2с | L
Ox2d | M
Ox2e | N
Ox2f | 0
Ох30 | P
Ox31 | Q
Ox32 | R
Ox33 i s
Ох34 | T
Ox35 | U
Ox36 | v
Ox37 | W
Ох38 | X
Ox39 | Y
ОхЗа | Z
Ox3b
Ох3с |
Ox3d | ]
Ox3e |
Ox3f |
Ox40 |
Ox41 | a
Ox42 | b
Ox43 | C
Ox44 | d
Ox45 | e
Ox46 | f
Ox47 | g
Ox48 | h
Ох49 | i
Ox4a | j
Ox4b | k
Ox4c ||
Ox4d | m
Ox4e | n
Ox4f | o
Ox50 | p
Ох51 | q
Ox52 |r
Ox53 | s
Ox54 it
Ox55 | u
Ox56 | v
Ox57 | w
Ox58 | x
Ox59 | y
Ох5а | z
Ox5b | {
Ox5c ||
Ox5d | }
Ox5e |
Ox5f
(sp)
32
0040
64
0100
96
0140
0141
0142
0143
0144
0145
0146
0147
Ox60
Ох61
Ox62
Ох63
Ох64
Ox65
Ох66
Ох67
Ох68
Ox69
Охба
Ox6b
33
34
35
36
37
38
39
0041
0042
0043
0044
0045
65
66
67
68
69
70
71
0101
0102
0103
0104
0105
0106
0107
97
98
99
100
101
102
103
#3
&
0047
40
41
42
43
44
45
46
47
0050
0051
0052
0053
0054
0055
0056
0057
72
73
74
75
76
77
78
79
0110
0111
0112
0113
0114
0115
0116
104
105
106
107
108
109
110
111
0150
0151
0152
0153
0154
0155
0156
0157
Охбс
Ox6d
Охбе
0117
Ox6f
48
49
50
51
52
53
54
55
0060
0061
0062
0063
0064
0065
0066
0067
80
81
82
83
84
85
86
87
0160
0161
0162
0163
0164
0165
0166
0167
0120
0121
0122
0123
0124
0125
0126
0127
0130
0131
0132
0133
0134
0135
0136
0137
112
113
114
115
116
117
118
119
Ox70
071
Ox72
Ox73
Ox74
Ox75
Ox76
Ox77
1
4
6.
56
57
58
59
60
61
62
63
0070
0071
0072
0073
0074
0075
0076
88
89
90
91
92
93
94
95
0170
0171
0172
0173
0174
0175
0176
120
121
122
123
124
125
126
Ox78
Ox79
Ox7a
Ox7b
Ox7c
Ox7d
Ox7e
>
0077
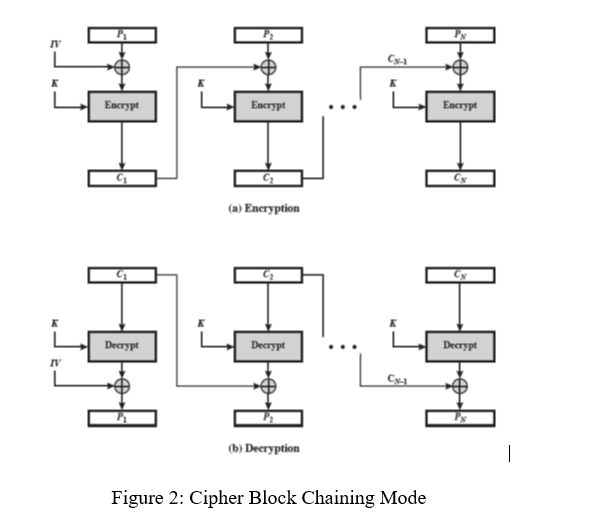
Transcribed Image Text:IV
Encrypt
Encrypt
Encrypt
Cy
(a) Eneryption
Decrypt
Decrypt
Decrypt
IV
(b) Decryption
Figure 2: Cipher Block Chaining Mode
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY