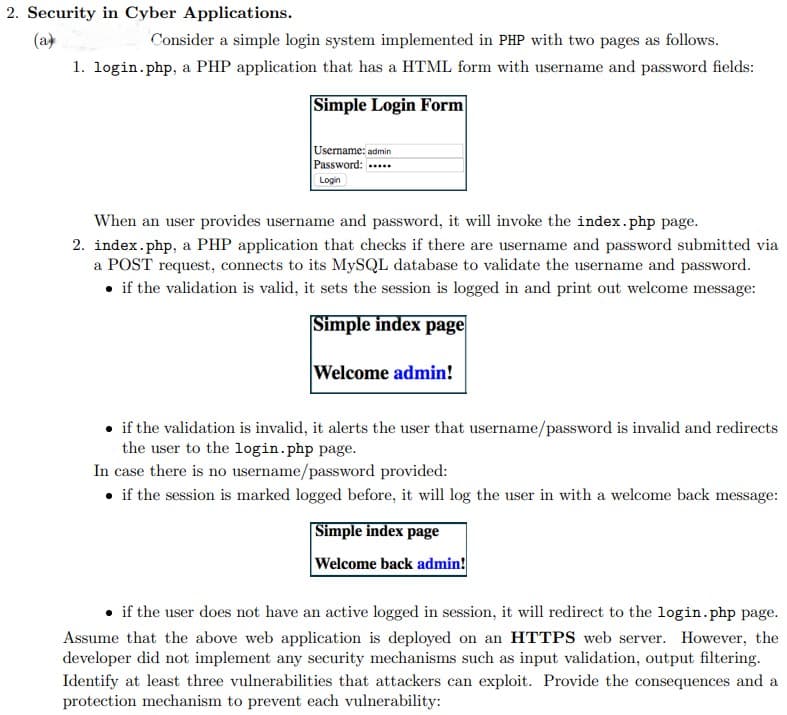
2. Security in Cyber Applications. (a Consider a simple login system implemented in PHP with two pages as follows. 1. login.php, a PHP application that has a HTML form with username and password fields: Simple Login Form Username: admin Password: Login When an user provides username and password, it will invoke the index.php page. 2. index.php, a PHP application that checks if there are username and password submitted via a POST request, connects to its MySQL database to validate the username and password. • if the validation is valid, it sets the session is logged in and print out welcome message: Simple index page Welcome admin! • if the validation is invalid, it alerts the user that username/password is invalid and redirects the user to the login.php page. In case there is no username/password provided: • if the session is marked logged before, it will log the user in with a welcome back message: Simple index page Welcome back admin! if the user does not have an active logged in session, it will redirect to the login.php page. Assume that the above web application is deployed on an HTTPS web server. However, the developer did not implement any security mechanisms such as input validation, output filtering. Identify at least three vulnerabilities that attackers can exploit. Provide the consequences and a protection mechanism to prevent each vulnerability:
Vulnerability 1: Name and consequences of the vulnerability:
As a hacker, how can you exploit the vulnerability to attack the system? Provide a concrete example or specific steps.
As a developer, how can you ensure that vulnerability will not exist in your program? You only need to provide a high-level solution.
Vulnerability 2: Name and consequences of the vulnerability:
As a hacker, how can you exploit the vulnerability to attack the system? Provide a concrete example or specific steps.
As a developer, how can you ensure that vulnerability will not exist in your program? You only need to provide a high-level solution.
Vulnerability 3: Name and consequences of the vulnerability:
As a hacker, how can you exploit the vulnerability to attack the system? Provide a concrete example or specific steps.
As a developer, how can you ensure that vulnerability will not exist in your program? You only need to provide a high-level solution.
Vulnerability in cybersecurity means the weakness in the system that cybercriminals/hackers can make use of and gain unauthorized access to the system. As a result malicious attacks happen. If attacks happen then data present in the system can be harmed or can be stolen. Data in present world is like a gold mine. So, protection from the vulnerabilities is important in today's world.
Login functionalities specially should be protected. If this is properly protected then there is less chance of attacks.
3 vulnerabilities , consequences , example/exploit the vulnerability to attack the system and ensuring that vulnerability will not exist are as follows :
Name of vulnerability : Default credentials
Consequence of this vulnerability (result) : Attacker can gain access to complete system and stole the data or harm the data present in the system.
Example : default credentials such as “admin:admin” is easy to guess.
Ensuring that vulnerability will not exist (remedy) : the developers of the login page need to ensure that the default credentials are disabled or changed and a strong pair of non-guessable credentials should be used.
Step by step
Solved in 4 steps
