Each of the following activities are commonly performed during the implementation of the Database Life Cycle (DBLC). Fill in the blank, before each activity, with the phase number of the DBLS that this activity would normally be performed. DBLC Task Numbers: 1. Database initial study 2. Database design 3. Implementation and loading 4. Testing and evaluation 5. Operation 6. Maintenance and evolution
Each of the following activities are commonly performed during the implementation of the Database Life Cycle (DBLC). Fill in the blank, before each activity, with the phase number of the DBLS that this activity would normally be performed. DBLC Task Numbers: 1. Database initial study 2. Database design 3. Implementation and loading 4. Testing and evaluation 5. Operation 6. Maintenance and evolution
Chapter7: Database Administration
Section: Chapter Questions
Problem 4CAT: Write, but do not execute, the commands to grant the following privileges: a. User Rodriquez must be...
Related questions
Question
Each of the following activities are commonly performed during the implementation of the
DBLC Task Numbers:
1. Database initial study
2. Database design
3. Implementation and loading
4. Testing and evaluation
5. Operation
6. Maintenance and evolution
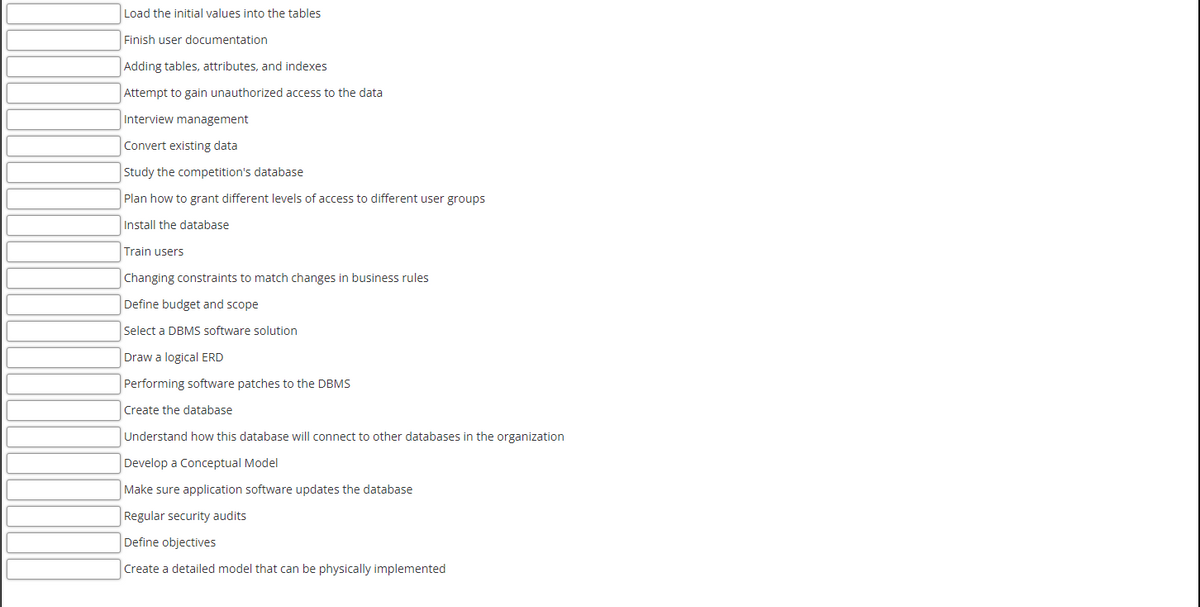
Transcribed Image Text:Load the initial values into the tables
Finish user documentation
Adding tables, attributes, and indexes
Attempt to gain unauthorized access to the data
Interview management
Convert existing data
Study the competition's database
Plan how to grant different levels of access to different user groups
Install the database
Train users
Changing constraints to match changes in business rules
Define budget and scope
Select a DBMS software solution
Draw a logical ERD
Performing software patches to the DBMS
Create the database
Understand how this database will connect to other databases in the organization
Develop a Conceptual Model
Make sure application software updates the database
Regular security audits
Define objectives
Create a detailed model that can be physically implemented
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 2 images

Recommended textbooks for you

A Guide to SQL
Computer Science
ISBN:
9781111527273
Author:
Philip J. Pratt
Publisher:
Course Technology Ptr

Fundamentals of Information Systems
Computer Science
ISBN:
9781305082168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning


A Guide to SQL
Computer Science
ISBN:
9781111527273
Author:
Philip J. Pratt
Publisher:
Course Technology Ptr

Fundamentals of Information Systems
Computer Science
ISBN:
9781305082168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning
