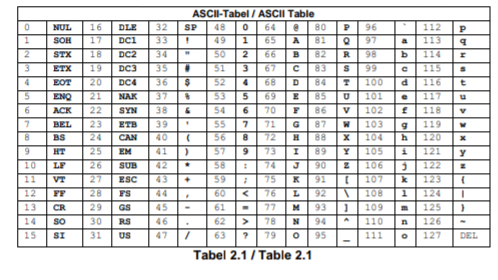
Encryption is commonly used to disguise messages on the internet. A Caesar cipher performs a shift of all of the characters in a string (based on their ASCII values, see Table 2.1), e.g. h e l l o → m j q q t The example shows a shift with a distance of 5 characters, i.e. h(ASCII:104) → m(ASCII:109) Write a C/C++ program that asks the user to input a line of plaintext and the distance value and outputs an encrypted text using a Caesar cipher, with the ASCII values range from 0 through 127. Use underscores (ASCII: 95) to represent space characters. Underscore characters should not be encrypted, and any character that is encrypted may not become an underscore. In this case, the character should be changed to the next character in the ASCII table. The program should work for any printable characters. NB: No strings (datatype) or library functions may be used.
Encryption is commonly used to disguise messages
on the internet. A Caesar cipher performs a shift of
all of the characters in a string (based on their ASCII
values, see Table 2.1), e.g.
h e l l o → m j q q t
The example shows a shift with a distance of 5
characters, i.e. h(ASCII:104) → m(ASCII:109)
Write a C/C++ program that asks the user to input a
line of plaintext and the distance value and outputs
an encrypted text using a Caesar cipher, with the
ASCII values range from 0 through 127. Use
underscores (ASCII: 95) to represent space
characters.
Underscore characters should not be encrypted,
and any character that is encrypted may not
become an underscore. In this case, the character
should be changed to the next character in the
ASCII table.
The program should work for any printable
characters.
NB: No strings (datatype) or library functions may
be used.
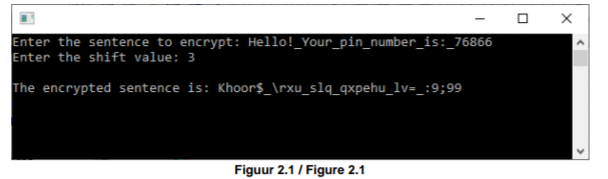
See Figure 2.1 for example output.
Trending now
This is a popular solution!
Step by step
Solved in 3 steps with 3 images


