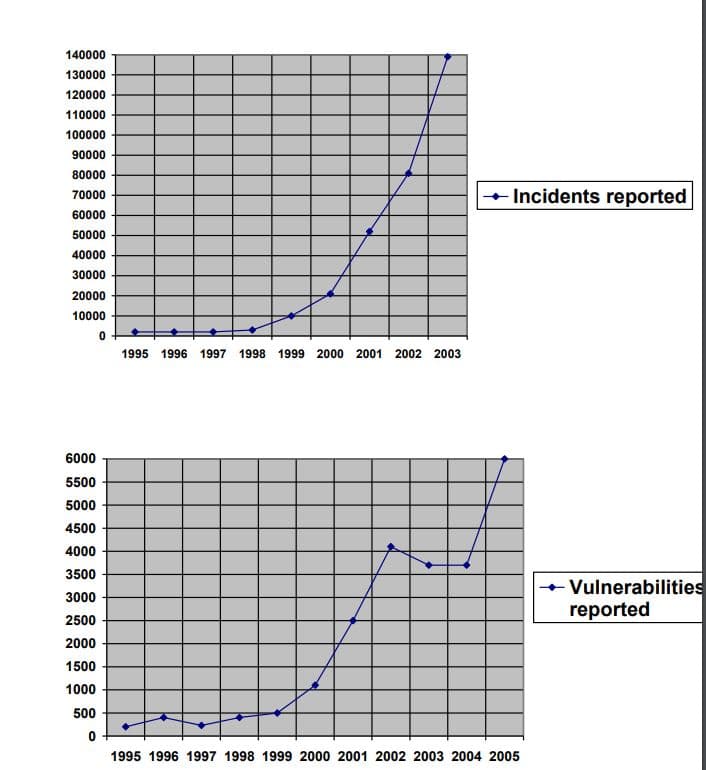
Facts regarding upwards trend in the number of incidents reported :
1. Hacking Attacks Are on the Rise :
According to recent data, there is an attack every 39 seconds. It's one of the cyber security statistics that's sure to keep any entrepreneur up at night.
- Government, Technology, and Retail Are Some of the Most Affected :In 2016, an estimated 95% of all breached records came from these three sectors. This is largely due to the large amount of data stored by these organizations, as well as the sensitive nature of such information.
- Data Breaches Are Extremely Costly :
- cber attacks will cost companies $10.5
trillion per year by 2025.
4. Small Businesses Are Especiall
Vulnerable : fact that, 43% of all cyber attacks are directed at small businesses. For anyone running a small business, it is critical to take data protection seriously and invest in robust cyber security measures that can keep your organization safe.
5.Covid-19 Led to an Increase in Attacks :there was a 300% increase in attacks right after Covid-19 began to spread.
6. Human Errors Are Responsible for Most Breaches : fact, 95% of all data breaches occur as a result of human error. These errors range from clicking on dangerous links to falling for email scams.
Reasoned arguments:
previous, Unpatched Security Vulnerabilities :
For years, data security specialists are assembling data on the exploitations that hackers have with success used on corporations in dozens of nations. These exploits square measure sorted into many Common Vulnerabilities and Exposures (CVEs) to spot them for future reference.
However, several of those security vulnerabilities go unfixed for long periods of your time. as an example, in line with Verizon's 2015 information Breach Investigations Report, "99.9% of the exploited vulnerabilities had been compromised quite a year once the associated CVE was printed." Leaving these previous security vulnerabilities unfixed provides hackers a free pass to your company's most sensitive data.
Human Error :
Unfortunately, one among the most important sources of a knowledge breach isn't some unknown or forgotten security bug, it's human error.
According to statistics from a CompTIA study cited by shrm.org, "Human error accounts for fifty two % of the basis causes of security breaches." the precise nature of the error could vary, however some situations include:
The use of weak passwords;
Sending sensitive data to the incorrect recipients;
Sharing password/account information; and Falling for phishing scams.Many of those human errors is prevented by ensuring staff apprehend their basic information security measures. As expressed within the SHRM article, "experts usually say a lot of worker coaching is required to handle the 'human firewall' issue."
Malware:
Malware isn't simply a retardant for private computers at the homes of staff, it's associate degree ever-expanding threat aimed directly at your company's systems. in line with the Verizon DBIR 2015, "5 malware events occur each second."
While several of those "malware events" square measure minor in nature, the sheer range of those events is worrying. Also, there exists an out of this world quantity of variation between malware samples.As observed within the Verizon DBIR, "we found that seventy to ninetieth (depending on the supply and organization) of malware samples square measure distinctive to one organization." Despite this reality, several malware programs hail from simply a couple of totally different
"families." in line with Verizon, "20 families diagrammatic regarding seventieth of all malware activity."Why? the most reason is that a lot of hackers build minor modifications to existing malware programs to do and build them unidentifiable to antivirus programs whereas still manufacturing the meant result by the hacker.
corporate executive Misuse :
While closely associated with human error, this explanation for company information is a lot of insidious in nature. Human error implies associate degree innocent accident or mistake. corporate executive misuse, on the opposite hand, is that the deliberate abuse of your company's systems by a licensed user, generally for private gain.
As observed in Verizon's 2015 DBIR, "it's all regarding grabbing some straightforward
Benjamins for these mendacious malefactors, with gain and convenience being the first motivators (40% of incidents)."
The issue here is that the malicious actor is somebody in whom your organization has placed trust. Worse yet, as observed by Verizon's report, "catching corporate executive abuse isn't easy... in several of the incidents we tend to reviewed, the corporate executive abuse was discovered throughout rhetorical examination of user devices once people left an organization."