Input In each test case, we will call your decrypt function with an open file that contains encrypted text, and the name of a file containing an English wordlist. An encrypted file contains the encrypted text; for example, it might look like this: Q svme pm nmtb smmvtg bpm ijamvkm wn pqa wev niugtg. An English wordlist has one word per line; here is a small example: abases abash abashed abashes abashing abashment Return Value Using the full English wordlist provided in the starter code, your function would return the following string for the above encrypted text: i knew he felt keenly the absence of his own family. Starter code Please find your starter code and test examples in MarkUs. In decrypt. py, youll find a function named decrypt whose implementation you must complete. Testing We have a thorough set of tests on which we'll run your code. Everything we'll test has been discussed here and in the starter code, so please read both carefully! The starter code includes the test case from this handout that you can try out by running test_decrypt.py. We have also provided several txt files that you can use to test as well.
Input In each test case, we will call your decrypt function with an open file that contains encrypted text, and the name of a file containing an English wordlist. An encrypted file contains the encrypted text; for example, it might look like this: Q svme pm nmtb smmvtg bpm ijamvkm wn pqa wev niugtg. An English wordlist has one word per line; here is a small example: abases abash abashed abashes abashing abashment Return Value Using the full English wordlist provided in the starter code, your function would return the following string for the above encrypted text: i knew he felt keenly the absence of his own family. Starter code Please find your starter code and test examples in MarkUs. In decrypt. py, youll find a function named decrypt whose implementation you must complete. Testing We have a thorough set of tests on which we'll run your code. Everything we'll test has been discussed here and in the starter code, so please read both carefully! The starter code includes the test case from this handout that you can try out by running test_decrypt.py. We have also provided several txt files that you can use to test as well.
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
Please in Python! Help question 1?
Transcribed Image Text:Q1: Finding the Key
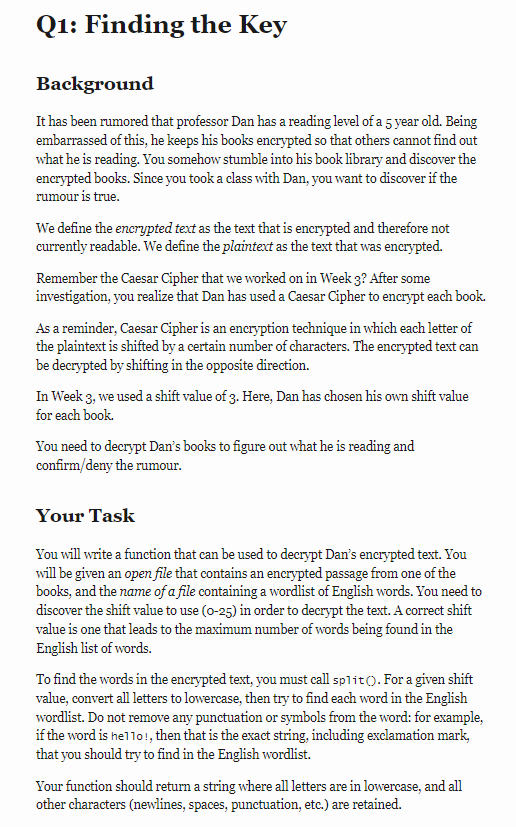
Background
It has been rumored that professor Dan has a reading level of a 5 year old. Being
embarrassed of this, he keeps his books encrypted so that others cannot find out
what he is reading. You somehow stumble into his book library and discover the
encrypted books. Since you took a class with Dan, you want to discover if the
rumour is true.
We define the encrypted text as the text that is encrypted and therefore not
currently readable. We define the plaintext as the text that was enerypted.
Remember the Caesar Cipher that we worked on in Week 3? After some
investigation, you realize that Dan has used a Caesar Cipher to enerypt each book.
As a reminder, Caesar Cipher is an encryption technique in which each letter of
the plaintext is shifted by a certain number of characters. The encrypted text can
be decrypted by shifting in the opposite direction.
In Week 3, we used a shift value of 3. Here, Dan has chosen his own shift value
for each book.
You need to decrypt Dan's books to figure out what he is reading and
confirm/deny the rumour.
Your Task
You will write a function that can be used to decrypt Dan's encrypted text. You
will be given an open file that contains an encerypted passage from one of the
books, and the name of a file containing a wordlist of English words. You need to
discover the shift value to use (o-25) in order to decrypt the text. A correct shift
value is one that leads to the maximum number of words being found in the
English list of words.
To find the words in the encrypted text, you must call split(). For a given shift
value, convert all letters to lowercase, then try to find each word in the English
wordlist. Do not remove any punctuation or symbols from the word: for example,
if the word is hello!, then that is the exact string, including exclamation mark,
that you should try to find in the English wordlist.
s are
Your function should return a string where all letters are in lowercase, and all
other characters (newlines, spaces, punctuation, etc.) are retained.

Transcribed Image Text:Input
In each test case, we will call your decrypt function with an open file that
contains encrypted text, and the name of a file containing an English wordlist.
An encrypted file contains the encrypted text; for example, it might look like this:
Q svme pm nmtb smmvtg bpm ijamvkm wn pqa
wev niugtg.
An English wordlist has one word per line; here is a small example:
abases
abash
abashed
abashes
abashing
abashment
Return Value
Using the full English wordlist provided in the starter code, your function would
return the following string for the above enerypted text:
i knew he felt keenly the absence of his
own family.
Starter code
Please find your starter code and test examples in MarkUs.
In decrypt. py, you'l find a function named decrypt whose implementation you
must complete.
Testing
We have a thorough set of tests on which we'll run your code. Everything we'll
test has been discussed here and in the starter code, so please read both carefully!
The starter code includes the test case from this handout that you can try out by
running test_decrypt.py. We have also provided several txt files that you can
use to test as well.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 4 steps with 2 images

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY