IPV4 ADDRESS 8+8+8+8=32 BITS NNNNNNNN.NNNNNNNN.NNNNNNNN.HHHHHHHH 192.168.30.0/24-Subnetmask N- Network Portion H- Host Portion No of valid Hosts= 2-2 = 28-2= 256-2=254 HOSTS 192.168.30.0 ----Network Address 192.168.30.1- First Useable Address 0+1=1 192.168.30. 254 ---------Last Useable Address 0+254=254 192.168.30.255 --------Broadcast Address 254+1=255 Subnetting IP Networks - Given the address block 192.168.30.0/24, create an IP addressing scheme that would allow for 2 subnets with 126 host IP addresses per subnet. Compute for the first two subnets only IPV4 ADDRESS 8+8+8+8=32 BITS NNNNNNNN.NNNNNNNN.NNNNNNNN.HHHHHHHH 192.168.30.0/24-Subnetmask N- Network Portion H- Host Portion N= Bits Borrowed-----1 BIT BORROW NNNNNNNN.NNNNNNNN.NNNNNNNN.NHHHHHHH No of Subnets= 2" =2=2 SUBNETS Remaining Host Bits(h) 8-1-7 No of valid Hosts= 2h-2 = 27-2= 128-2=126 HOSTS 192.168.30.0/25 Subnet 1
IPV4 ADDRESS 8+8+8+8=32 BITS NNNNNNNN.NNNNNNNN.NNNNNNNN.HHHHHHHH 192.168.30.0/24-Subnetmask N- Network Portion H- Host Portion No of valid Hosts= 2-2 = 28-2= 256-2=254 HOSTS 192.168.30.0 ----Network Address 192.168.30.1- First Useable Address 0+1=1 192.168.30. 254 ---------Last Useable Address 0+254=254 192.168.30.255 --------Broadcast Address 254+1=255 Subnetting IP Networks - Given the address block 192.168.30.0/24, create an IP addressing scheme that would allow for 2 subnets with 126 host IP addresses per subnet. Compute for the first two subnets only IPV4 ADDRESS 8+8+8+8=32 BITS NNNNNNNN.NNNNNNNN.NNNNNNNN.HHHHHHHH 192.168.30.0/24-Subnetmask N- Network Portion H- Host Portion N= Bits Borrowed-----1 BIT BORROW NNNNNNNN.NNNNNNNN.NNNNNNNN.NHHHHHHH No of Subnets= 2" =2=2 SUBNETS Remaining Host Bits(h) 8-1-7 No of valid Hosts= 2h-2 = 27-2= 128-2=126 HOSTS 192.168.30.0/25 Subnet 1
Chapter12: Network Configuration
Section: Chapter Questions
Problem 13RQ
Related questions
Question
Just answer please without explanation
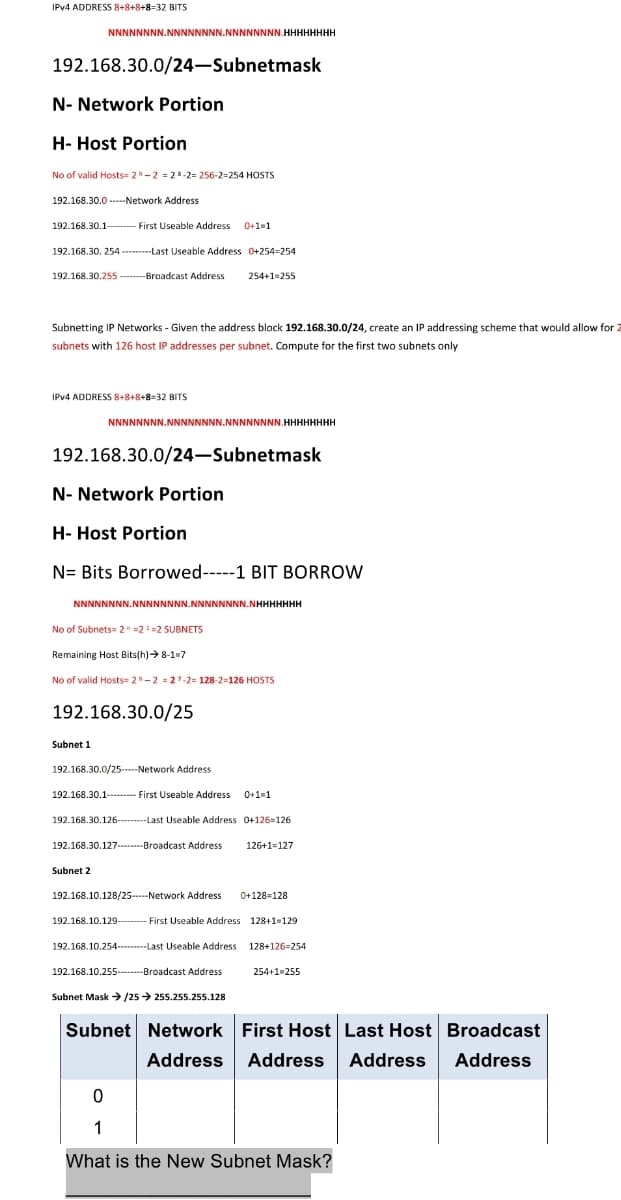
Transcribed Image Text:IPV4 ADDRESS 8+8+8+8=32 BITS
NNNNNNNN.NNNNNNNN.NNNNNNNN.HHHHHHHH
192.168.30.0/24-Subnetmask
N- Network Portion
H- Host Portion
No of valid Hosts= 2-2 = 28-2= 256-2=254 HOSTS
192.168.30.0 -----Network Address
192.168.30.1------ First Useable Address
0+1=1
192.168.30. 254 ---------Last Useable Address 0+254=254
192.168.30.255 -------Broadcast Address
254+1=255
Subnetting IP Networks - Given the address block 192.168.30.0/24, create an IP addressing scheme that would allow for 2
subnets with 126 host IP addresses per subnet. Compute for the first two subnets only
IPV4 ADDRESS 8+8+8+8=32 BITS
NNNNNNNN.NNNNNNNN.NNNNNNNN.HHHHHHHH
192.168.30.0/24–Subnetmask
N- Network Portion
H- Host Portion
N= Bits Borrowed-----1 BIT BORROW
NNNNNNNN.NNNNNNNN.NNNNNNNN.NHHHHHHH
No of Subnets= 2" =2=2 SUBNETS
Remaining Host Bits(h)> 8-1-7
No of valid Hosts= 2-2 = 27-2= 128-2=126 HOSTS
192.168.30.0/25
Subnet 1
192.168.30.0/25----Network Address
192.168.30.1----- First Useable Address 0+1=1
192.168.30.126----Last Useable Address 0+126=126
192.168.30.127.---Broadcast Address
126+1=127
Subnet 2
192.168.10.128/25-Network Address
0+128=128
192.168.10.129---
First Useable Address 128+1=129
192.168.10.254---Last Useable Address 128+126=254
192.168.10.255.-------Broadcast Address
254+1=255
Subnet Mask /25 > 255.255.255.128
Subnet Network First Host Last Host Broadcast
Address Address
Address
Address
1
What is the New Subnet Mask?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 1 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:
9781337569798
Author:
ECKERT
Publisher:
CENGAGE L

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:
9781337569798
Author:
ECKERT
Publisher:
CENGAGE L