Part 1: Configure Basic Switch Security Configure the following on S1: o Privileged EXEC mode encrypted password is ciscoenpa44. o Console line password is ciscoconpa44, exec-timeout is 10 minutes, and enable login. o Password for the VTY lines is ciscovtypa44, exec-timeout is 10 minutes, enable login, and add the logging synchronous command. o Encrypt all plaintext passwords. Configure the following on S3: o An MOTD banner should include the word unauthorized. o Shut down all unused physical ports on the switch. o Enable port security on F0/3, where the MAC address should be dynamically learned and added to the running configuration. Part 2: Configure Basic Router Security Configure the following on R3: o Minimum password length is 10 characters. o Privileged EXEC mode encrypted password is ciscoenpa44. Enable SSH connections on R3as follows: o The domain name is skillsexam.com o It will only allow 2 authentication attempts. o It will timeout after 120 seconds. o Create a user account of Admin03 in the local database of the router with a secret password of Admin03pa44. o The RSA key should be generated with 1024 modulus bits. o Only SSH is allowed on the VTY lines. o Verify the SSH configuration SSH to R3 from the command prompt of PC-B and PC-C. Part 3: Configure AAA Authentication Configure AAA Local Authenticationon R2 as follows: o Create a local user account of Admin02 with a secret password of Admin02pa44. o Enable AAA services. o Configure a named list called Co-Login to authenticate logins using local AAA. o Configure the line console to use the defined named AAA method. o Verify the user EXEC login using the local database. Part 4: Configure Access Control Lists Configure a Numbered IP ACL 110 on R3 as follows: o Verify that PC-A can access both HTTP and HTTPS services on the Web Server. o Create a Numbered IP ACL 110 that permit any outside host to only access HTTPS service on the Web Server. o Apply the created access list to incoming traffic on interface S0/0/1. o Verify that PC-A can only access HTTPS service on the Web Server; PC-A cannot access HTTP service anymore.
plz solve
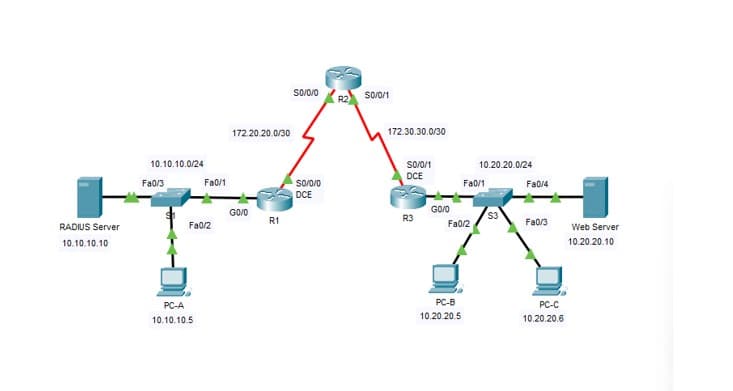
Provided with the topology, the addressing table, you are asked to configure the devices based on the questions below.
Addressing Table:
|
Device |
Interface |
IP Address |
Subnet Mask |
Default Gateway |
|
R1 |
G0/0 |
10.10.10.1 |
255.255.255.0 |
N/A |
|
S0/0/0 |
172.20.20.1 |
255.255.255.252 |
N/A |
|
|
R2 |
S0/0/0 |
172.20.20.2 |
255.255.255.252 |
N/A |
|
S0/0/1 |
172.30.30.2 |
255.255.255.252 |
N/A |
|
|
R3 |
G0/0 |
10.20.20.1 |
255.255.255.0 |
N/A |
|
S0/0/1 |
172.30.30.1 |
255.255.255.252 |
N/A |
|
|
PC-A |
NIC |
10.10.10.5 |
255.255.255.0 |
10.10.10.1 |
|
RADIUS Server |
NIC |
10.10.10.10 |
255.255.255.0 |
10.10.10.1 |
|
PC-B |
NIC |
10.20.20.5 |
255.255.255.0 |
10.20.20.1 |
|
PC-C |
NIC |
10.20.20.6 |
255.255.255.0 |
10.20.20.1 |
|
Web Server |
NIC |
10.20.20.10 |
255.255.255.0 |
10.20.20.1 |
Part 1: Configure Basic Switch Security
- Configure the following on S1:
o Privileged EXEC mode encrypted password is ciscoenpa44.
o Console line password is ciscoconpa44, exec-timeout is 10 minutes, and enable login.
o Password for the VTY lines is ciscovtypa44, exec-timeout is 10 minutes, enable login, and add the logging synchronous command.
o Encrypt all plaintext passwords.
- Configure the following on S3:
o An MOTD banner should include the word unauthorized.
o Shut down all unused physical ports on the switch.
o Enable port security on F0/3, where the MAC address should be dynamically learned and added to the running configuration.
Part 2: Configure Basic Router Security
- Configure the following on R3:
o Minimum password length is 10 characters.
o Privileged EXEC mode encrypted password is ciscoenpa44.
- Enable SSH connections on R3as follows:
o The domain name is skillsexam.com
o It will only allow 2 authentication attempts.
o It will timeout after 120 seconds.
o Create a user account of Admin03 in the local
o The RSA key should be generated with 1024 modulus bits.
o Only SSH is allowed on the VTY lines.
o Verify the SSH configuration SSH to R3 from the command prompt of PC-B and PC-C.
Part 3: Configure AAA Authentication
- Configure AAA Local Authenticationon R2 as follows:
o Create a local user account of Admin02 with a secret password of Admin02pa44.
o Enable AAA services.
o Configure a named list called Co-Login to authenticate logins using local AAA.
o Configure the line console to use the defined named AAA method.
o Verify the user EXEC login using the local database.
Part 4: Configure Access Control Lists
- Configure a Numbered IP ACL 110 on R3 as follows:
o Verify that PC-A can access both HTTP and HTTPS services on the Web Server.
o Create a Numbered IP ACL 110 that permit any outside host to only access HTTPS service on the Web Server.
o Apply the created access list to incoming traffic on interface S0/0/1.
o Verify that PC-A can only access HTTPS service on the Web Server; PC-A cannot access HTTP service anymore.
Trending now
This is a popular solution!
Step by step
Solved in 6 steps with 2 images









