QUESTION S You have hired an outside firm to develop a new vebsite for personal information trame, address, phone number, emal available to customers your IT department runs a few bests below in the report that the IT department sends you it shou will be stored on your company's servers (The format of the symbol A Meow12 edffadc2760blce8O0b193805471caed 8. "Meow124 cdffadc276absce800b193805471cae Based on this information, what can you conclude about O The hash function is lkely to create "hash collsions bet O The hash function is well-suited for your company's neer O The hash function is non-determinestie The hash function is not well-suited for your company's
QUESTION S You have hired an outside firm to develop a new vebsite for personal information trame, address, phone number, emal available to customers your IT department runs a few bests below in the report that the IT department sends you it shou will be stored on your company's servers (The format of the symbol A Meow12 edffadc2760blce8O0b193805471caed 8. "Meow124 cdffadc276absce800b193805471cae Based on this information, what can you conclude about O The hash function is lkely to create "hash collsions bet O The hash function is well-suited for your company's neer O The hash function is non-determinestie The hash function is not well-suited for your company's
Fundamentals of Information Systems
9th Edition
ISBN:9781337097536
Author:Ralph Stair, George Reynolds
Publisher:Ralph Stair, George Reynolds
Chapter5: Electronic Commerce And Enterprise Systems
Section: Chapter Questions
Problem 1PSE
Related questions
Question
Transcribed Image Text:QUESTION 5
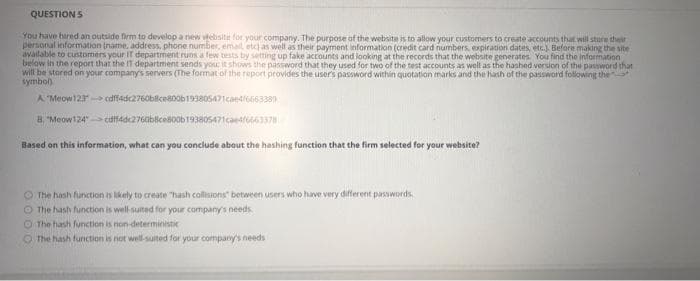
You have hired an outside firm to develop a new vebsitie for your company. The purpose of the website is to allow your customers to create accounts that will store their
personal information (name, address, phone number, email, etc) as well as their payment information (credit card numbers, expiration dates, etr.) Before making the site
available to customers your IT department runs a few tests by setting up fake accounts and looking at the records that the website generates. You find the information
below in the report that the IT department sends you: it shows the password that they used for two of the test accounts as well as the hashed version of the password that
will be stored on your company's servers (The format of the report provides the users password within quotation marks and the hash of the password following the
symbol)
A Meow12 edff4dc2760bilce800b193805471caedlo66338)
8, "Meow124" cutfadc276abscesoob193805471caeate6337
Based on this information, what can you conclude about the hashing function that the firm selected for your website?
O The hash function is ikely to create "hash collisions" between users who have very different passwords
O The hash function is well-suited for your company's needs
O The hash function is non-deterministic
The hash function is not well-suited for your company's needs
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Fundamentals of Information Systems
Computer Science
ISBN:
9781337097536
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Principles of Information Systems (MindTap Course…
Computer Science
ISBN:
9781285867168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Principles of Information Systems (MindTap Course…
Computer Science
ISBN:
9781305971776
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Fundamentals of Information Systems
Computer Science
ISBN:
9781337097536
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Principles of Information Systems (MindTap Course…
Computer Science
ISBN:
9781285867168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Principles of Information Systems (MindTap Course…
Computer Science
ISBN:
9781305971776
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Fundamentals of Information Systems
Computer Science
ISBN:
9781305082168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning
