What is the name given to the security attack when an opponent prevents messages from reaching a destination? Denial of service Masquerading Modification of messages Eavesdropping
What is the name given to the security attack when an opponent prevents messages from reaching a destination? Denial of service Masquerading Modification of messages Eavesdropping
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
Deluxe Bath Controller (This scenario is used by questions 14 and 15.)
At a touch of the Fill button the bath automatically fills with water. When it reaches the overflow point it automatically stops unless the user has already touched the Fill button again to stop the flow of water. There is also an Empty button to empty the bath.
- What is the name given to the security attack when an opponent prevents messages from reaching a destination?
- Denial of service
- Masquerading
- Modification of messages
- Eavesdropping
- Which of these is the highest-level part of the directory structure on Linux?
- Directory
- Topmost Directory
- File Allocation Table
- Superblock
- Which security goal aims to protect information from disclosure?
- Integrity
- Confidentiality
- Authenticity
- Accountability
- What does a network switch do?
- It broadcasts messages to all the computers that are connected to it
- It job is to disable part of the network
- It collects all the network cables in one place
- Routes a message to its destination computer/network only
- Why don't adjacent base stations interfere with each other?
- They are placed far apart
- They use different frequencies
- They use different encoding
- People use different mobile phones
- What is the benefit of having a LAN?
- You can surf the world-wide web
- Share resources
- Everybody has one
- It is cheaper than buying extra computers
- Set of Rules that govern the data communication and networks are:
- Standards
- IP Addresses
- MAC addresses
- Protocols
Operating System is
- Application Software
- Computer Hardware
- System Software
- File Server
- Variable which is used to control access by multiple processes in a common resource in an operating system is
- Semaphore
- Shell
- Kernel
- User Interface
- In a
computer network , when a performing task is divided among the computers, the phenomenon is called
- Distributed Systems
- Distributed Memory
- Distributed Processing
- Multitasking
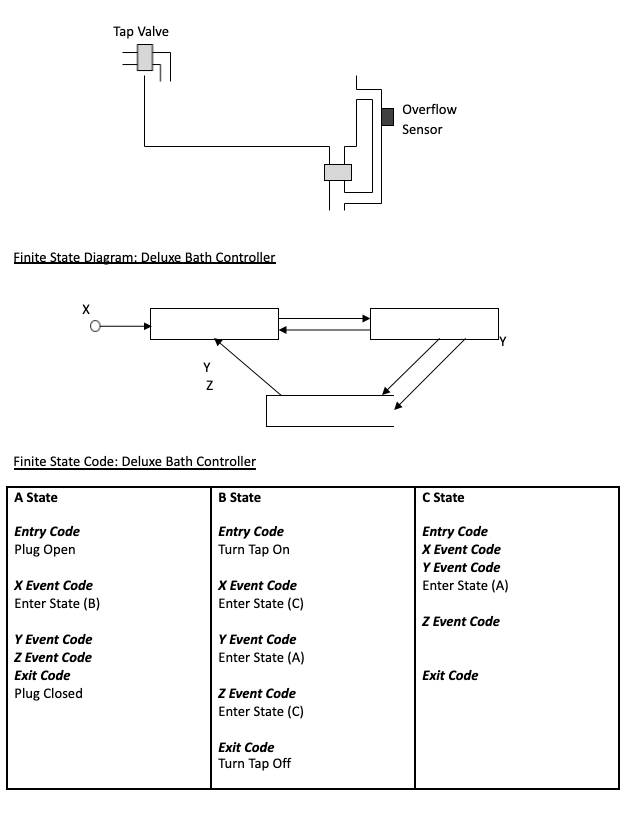
Transcribed Image Text:Тap Valve
Overflow
Sensor
Einite State Diagram: Deluxe Bath Controller
Y
Finite State Code: Deluxe Bath Controller
A State
B State
C State
Entry Code
Plug Open
Entry Code
Turn Tap On
Entry Code
X Event Code
Y Event Code
Enter State (A)
X Event Code
Enter State (B)
X Event Code
Enter State (C)
Z Event Code
Y Event Code
Z Event Code
Y Event Code
Enter State (A)
Exit Code
Exit Code
|Z Event Code
Enter State (C)
Plug Closed
Exit Code
Turn Tap Off
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 3 steps

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY