Which of the following are examples of Configuration Vulnerabilities: a. An organization manages its switches and routers using telnet, which sends user credentials unencrypted. Ob. An application uses a weak encryption standard to store passwords. Oc. While troubleshooting a problem, a Network Administrator removes access restrictions from critical operating system files. Od. A default password is not changed after installation.
Which of the following are examples of Configuration Vulnerabilities: a. An organization manages its switches and routers using telnet, which sends user credentials unencrypted. Ob. An application uses a weak encryption standard to store passwords. Oc. While troubleshooting a problem, a Network Administrator removes access restrictions from critical operating system files. Od. A default password is not changed after installation.
A+ Guide To It Technical Support
10th Edition
ISBN:9780357108291
Author:ANDREWS, Jean.
Publisher:ANDREWS, Jean.
Chapter17: Security Strategies And Documentation
Section: Chapter Questions
Problem 15TC
Related questions
Question
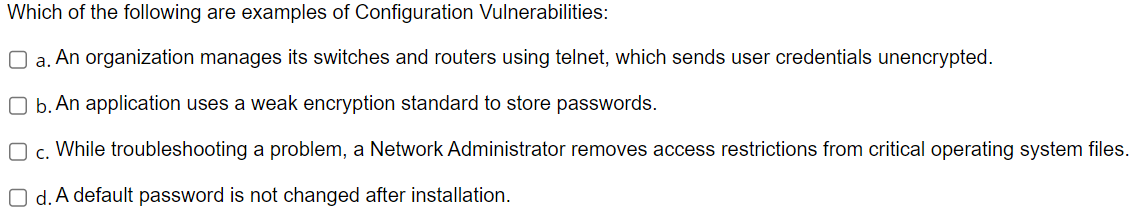
Transcribed Image Text:Which of the following are examples of Configuration Vulnerabilities:
O a. An organization manages its switches and routers using telnet, which sends user credentials unencrypted.
O b. An application uses a weak encryption standard to store passwords.
O c. While troubleshooting a problem, a Network Administrator removes access restrictions from critical operating system files.
Od. A default password is not changed after installation.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

A+ Guide To It Technical Support
Computer Science
ISBN:
9780357108291
Author:
ANDREWS, Jean.
Publisher:
Cengage,

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:
9781337569798
Author:
ECKERT
Publisher:
CENGAGE L

A+ Guide To It Technical Support
Computer Science
ISBN:
9780357108291
Author:
ANDREWS, Jean.
Publisher:
Cengage,

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:
9781337569798
Author:
ECKERT
Publisher:
CENGAGE L