Write a Python program that uses a function to find the area of Trapezoid. The function receives three values a, b, and h as shown in the figure. The function returns the area to the caller.
Write a Python program that uses a function to find the area of Trapezoid. The function receives three values a, b, and h as shown in the figure. The function returns the area to the caller.
C++ Programming: From Problem Analysis to Program Design
8th Edition
ISBN:9781337102087
Author:D. S. Malik
Publisher:D. S. Malik
Chapter6: User-defined Functions
Section: Chapter Questions
Problem 12PE: Write a program that takes as input five numbers and outputs the mean (average) and standard...
Related questions
Question
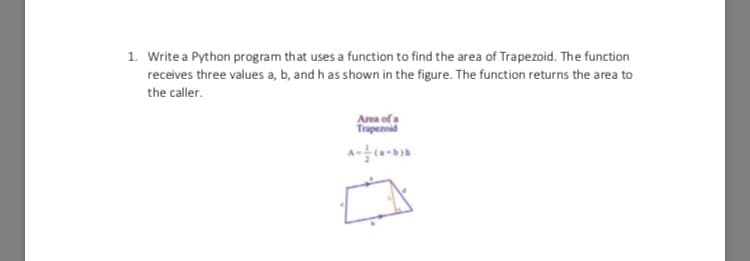
Transcribed Image Text:1. Write a Python program that uses a function to find the area of Trapezoid. The function
receives three values a, b, and h as shown in the figure. The function returns the area to
the caller.
Area ofa
Trapezoid
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 3 steps with 2 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

C++ Programming: From Problem Analysis to Program…
Computer Science
ISBN:
9781337102087
Author:
D. S. Malik
Publisher:
Cengage Learning

C++ for Engineers and Scientists
Computer Science
ISBN:
9781133187844
Author:
Bronson, Gary J.
Publisher:
Course Technology Ptr

C++ Programming: From Problem Analysis to Program…
Computer Science
ISBN:
9781337102087
Author:
D. S. Malik
Publisher:
Cengage Learning

C++ for Engineers and Scientists
Computer Science
ISBN:
9781133187844
Author:
Bronson, Gary J.
Publisher:
Course Technology Ptr