Your company is building a new corporate facility, as shown in Figure 1.2, to house its 5,000 headquarters employees. The facility will feature multiple floors. Some management personnel will use traditional offices with doors and windows, but the majority of the employees will work in open cubicles. STAIRS, ELEVATOR RESTROOMS (ALL FLOORS) OFFICES 日期 CUBICLE AREA FLOORS 6-7 (SAME LAYOUT) FLOORS 3-5 (SAME LAYOUT) IT DEPARTMENT. -EMERGENCY EXIT SHIPPING DOORS SHIPPING SERVER ROOM FLOOR 2
Your company is building a new corporate facility, as shown in Figure 1.2, to house its 5,000 headquarters employees. The facility will feature multiple floors. Some management personnel will use traditional offices with doors and windows, but the majority of the employees will work in open cubicles. STAIRS, ELEVATOR RESTROOMS (ALL FLOORS) OFFICES 日期 CUBICLE AREA FLOORS 6-7 (SAME LAYOUT) FLOORS 3-5 (SAME LAYOUT) IT DEPARTMENT. -EMERGENCY EXIT SHIPPING DOORS SHIPPING SERVER ROOM FLOOR 2
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
Book title:
Chapter 1 - Infrastructure security in the Real world
From the information provided in the second scenario, consider the NIST functions detailed in this section and then write what to observe as they relate to each category.
1. Sample type of response plan that might be necessary when general physical security is breached at the facility (NIST RS.AN-1, 2, 3)?
2. Considering the information kept on the company’s servers, which type of response plan might be necessary when physical security is breached in the server room (NIST RS.CO-4, 5)?
(Refer to screenshot for reference)
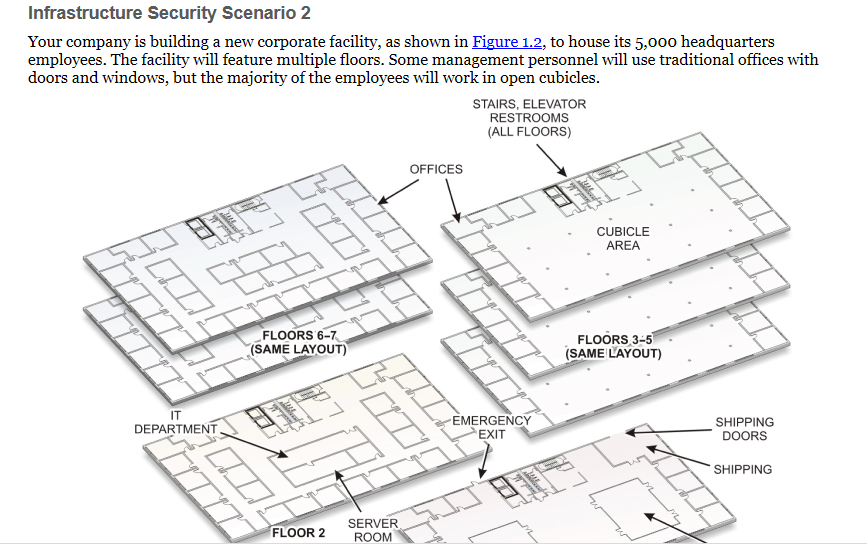
Transcribed Image Text:Infrastructure Security Scenario 2
Your company is building a new corporate facility, as shown in Figure 1.2, to house its 5,000 headquarters
employees. The facility will feature multiple floors. Some management personnel will use traditional offices with
doors and windows, but the majority of the employees will work in open cubicles.
STAIRS, ELEVATOR
RESTROOMS
(ALL FLOORS)
OFFICES
日期
CUBICLE
AREA
FLOORS 6-7
(SAME LAYOUT)
FLOORS 3-5
(SAME LAYOUT)
IT
DEPARTMENT.
-EMERGENCY
EXIT
SHIPPING
DOORS
SHIPPING
FLOOR 2
SERVER
ROOM
IT
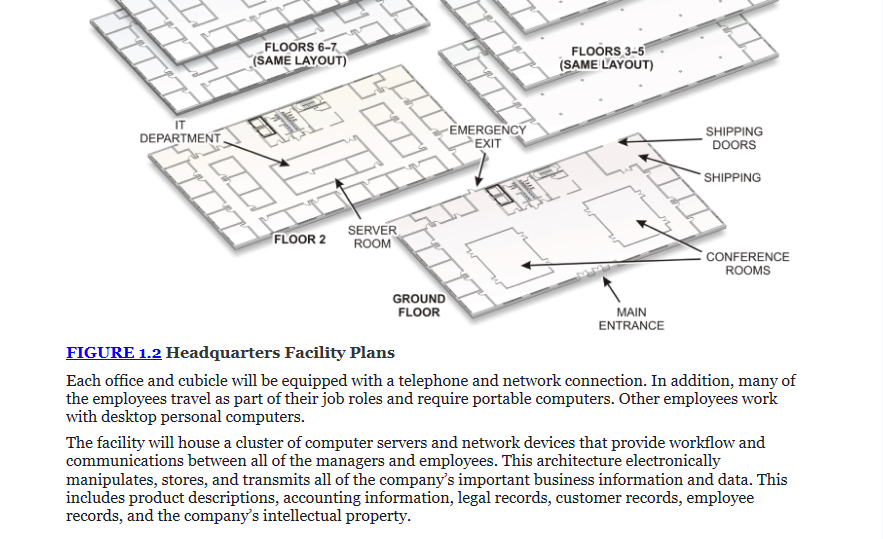
Transcribed Image Text:FLOORS 6-7
(SAME LAYOUT)
FLOORS 3-5
(SAME LAYOUT)
IT
DEPARTMENT
FEMERGENCY
EXIT
SHIPPING
DOORS
* SHIPPING
日期
SERVER
ROOM
FLOOR 2
CONFERENCE
ROOMS
GROUND
FLOOR
MAIN
ENTRANCE
FIGURE 1.2 Headquarters Facility Plans
Each office and cubicle will be equipped with a telephone and network connection. In addition, many of
the employees travel as part of their job roles and require portable computers. Other employees work
with desktop personal computers.
The facility will house a cluster of computer servers and network devices that provide workflow and
communications between all of the managers and employees. This architecture electronically
manipulates, stores, and transmits all of the company's important business information and data. This
includes product descriptions, accounting information, legal records, customer records, employee
records, and the company's intellectual property.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 3 steps

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY