. Question Comp
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
7. Question
Comp
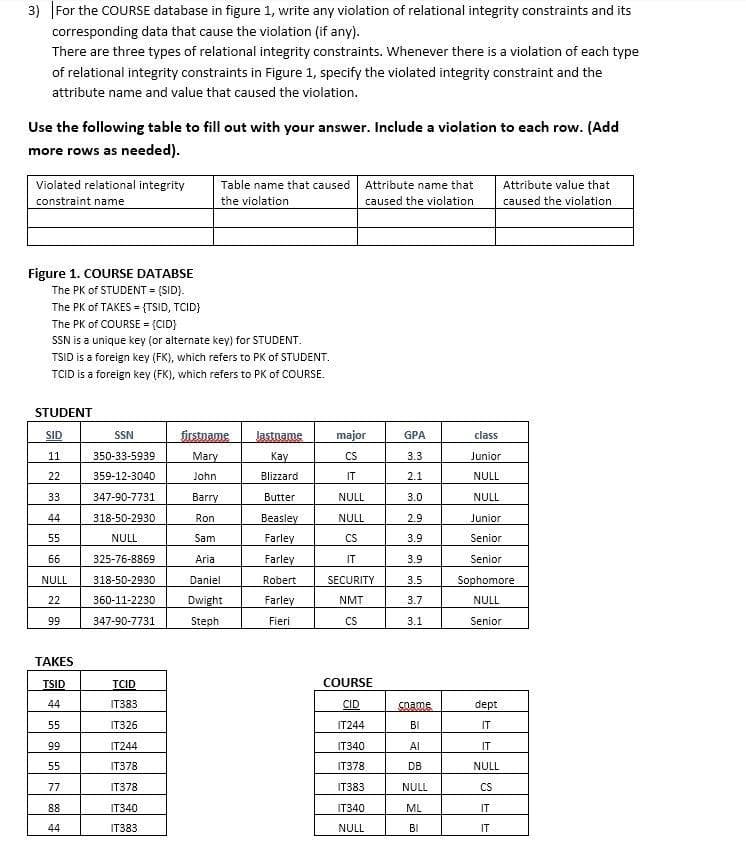
Transcribed Image Text:3) For the COURSE database in figure 1, write any violation of relational integrity constraints and its
corresponding data that cause the violation (if any).
There are three types of relational integrity constraints. Whenever there is a violation of each type
of relational integrity constraints in Figure 1, specify the violated integrity constraint and the
attribute name and value that caused the violation.
Use the following table to fill out with your answer. Include a violation to each row. (Add
more rows as needed).
Violated relational integrity
Table name that caused Attribute name that
Attribute value that
constraint name
caused the violation
the violation
caused the violation
Figure 1. COURSE DATABSE
The PK of STUDENT = (SID}.
The PK of TAKES = {TSID, TCID}
The PK of COURSE = (CID}
SSN is a unique key (or alternate key) for STUDENT.
TSID is a foreign key (FK), which refers to PK of STUDENT.
TCID is a foreign key (FK), which refers to PK of COURSE.
STUDENT
SID
SSN
ürstname
Jastname
major
GPA
class
11
350-33-5939
Mary
Kay
CS
3.3
Junior
22
359-12-3040
John
Blizzard
IT
2.1
NULL
33
347-90-7731
Barry
Butter
NULL
3.0
NULL
44
318-50-2930
Ron
Вeasley
NULL
2.9
Junior
55
NULL
Sam
Farley
CS
3.9
Senior
66
325-76-8869
Aria
Farley
IT
3.9
Senior
NULL
318-50-2930
Daniel
Robert
SECURITY
3.5
Sophomore
22
360-11-2230
Dwight
Farley
NMT
3.7
NULL
99
347-90-7731
Steph
Fieri
CS
3.1
Senior
ТАKES
TSID
TCID
COURSE
44
IT383
CID
Soame
dept
55
IT326
IT244
BI
IT
99
IT244
IT340
Al
IT
55
IT378
IT378
DB
NULL
77
IT378
IT383
NULL
CS
88
IT340
IT340
ML
IT
44
IT383
NULL
BI
IT
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 3 steps with 3 images

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY