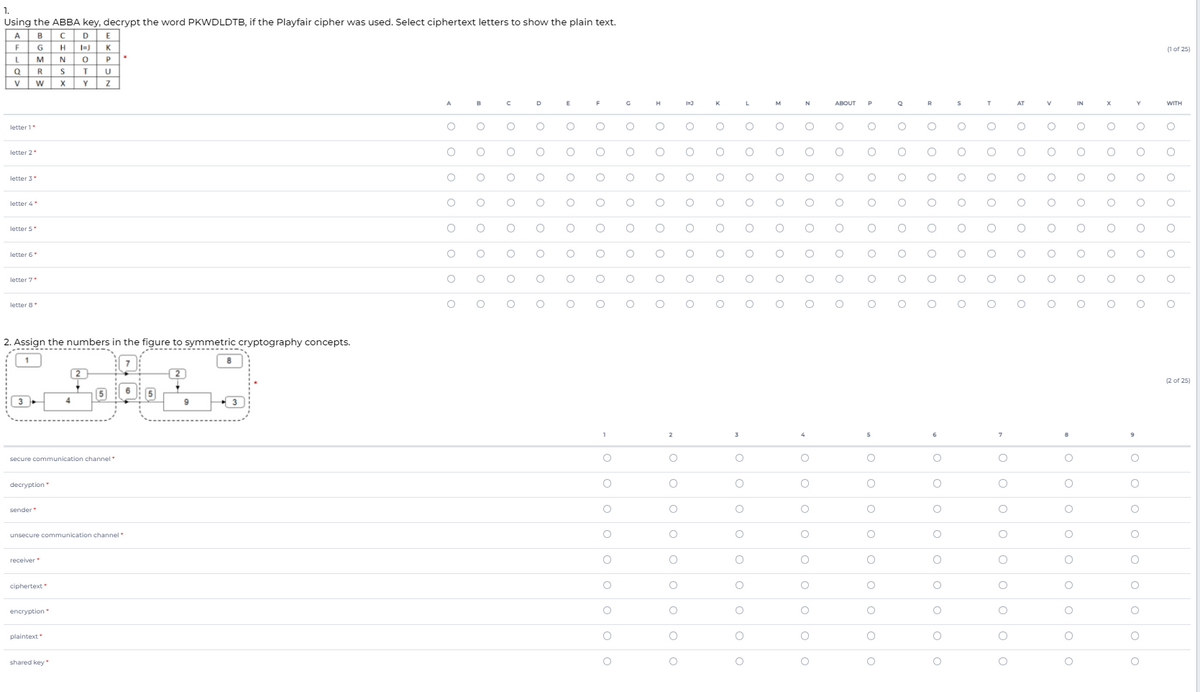
1. Using the ABBA key, decrypt the word PKWDLDTB, if the Playfair cipher was used. Select ciphertext letters to show the plain text. A BC DE F GH K MNO R ST yw xY Z (1 of 25) A K M ABOUT P R AT IN WITH letter 1 letter 2 letter 3 letter 4 letter 5 letter 6 letter 7 letter 8 2. Assign the numbers in the figure to symmetric cryptography concepts. 2 2 of 25) 3 2 secure communication channel decryption sender unsecure communication channel receiver ciphertext encryption plaintext shared key
1. Using the ABBA key, decrypt the word PKWDLDTB, if the Playfair cipher was used. Select ciphertext letters to show the plain text. A BC DE F GH K MNO R ST yw xY Z (1 of 25) A K M ABOUT P R AT IN WITH letter 1 letter 2 letter 3 letter 4 letter 5 letter 6 letter 7 letter 8 2. Assign the numbers in the figure to symmetric cryptography concepts. 2 2 of 25) 3 2 secure communication channel decryption sender unsecure communication channel receiver ciphertext encryption plaintext shared key
Management Of Information Security
6th Edition
ISBN:9781337405713
Author:WHITMAN, Michael.
Publisher:WHITMAN, Michael.
Chapter12: Protection Mechanisms
Section: Chapter Questions
Problem 19RQ
Related questions
Question
Transcribed Image Text:1.
Using the ABBA key, decrypt the word PKWDLDTB, if the Playfair cipher was used. Select ciphertext letters to show the plain text.
A
в
D
G
H
K
(1 of 25)
N O
ST
X Y
M
R
V
A
B
D
E
F
H
M
N
ABOUT
AT
IN
WITH
letter 1"
letter 2
letter 4
letter 5
letter 6
letter 7
letter 8
2. Assign the numbers in the figure to symmetric cryptography concepts.
2
2
(2 of 25)
5
6: 5
3
9
2
secure communication channel
decryption
sender
unsecure communication channel
receiver
ciphertext
encryption
plaintext
shared key
o o
O o o o
a o o o o o ooo O
O o O O
O o O
o o o o o
O o o ooo ooo o
O o
o o oO
AO O O o
O o o
O o
O o o
•o o o o
o o o
o o
O o
n o o ooo ooo o
O o
•o o ooo ooo o
O O
O o oo
O o
O o oO
mo o O ooo oo o
O o o
o o o ooo o o
O o o O
O ooO
O o
O o o
o o o oooO
o o o ooo o o o
O o O oo O
O O
o o o ooo o
O O
O o o
O o o
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 5 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Management Of Information Security
Computer Science
ISBN:
9781337405713
Author:
WHITMAN, Michael.
Publisher:
Cengage Learning,

Management Of Information Security
Computer Science
ISBN:
9781337405713
Author:
WHITMAN, Michael.
Publisher:
Cengage Learning,