A router receives a packet from another network for device in the local network that the router serves. However, it does not know the MAC address the intended recipient, it only knows the device's current IP address. What protocol would be used by the router to identify the intended recipient's MAC address -- which is needed to complete Destination MAC field of the Ethernet frame that would be used to deliver the packet to the recipient? (the format of an Ethernet frame is illustrated below). Ethernet II Туре 2 Bytes Frame Check Sequence 4 Bytes Destination MAC Source MAC Data 6 Bytes 6 Bytes 46 - 1500 Bytes
A router receives a packet from another network for device in the local network that the router serves. However, it does not know the MAC address the intended recipient, it only knows the device's current IP address. What protocol would be used by the router to identify the intended recipient's MAC address -- which is needed to complete Destination MAC field of the Ethernet frame that would be used to deliver the packet to the recipient? (the format of an Ethernet frame is illustrated below). Ethernet II Туре 2 Bytes Frame Check Sequence 4 Bytes Destination MAC Source MAC Data 6 Bytes 6 Bytes 46 - 1500 Bytes
Comptia A+ Core 1 Exam: Guide To Computing Infrastructure (mindtap Course List)
10th Edition
ISBN:9780357108376
Author:Jean Andrews, Joy Dark, Jill West
Publisher:Jean Andrews, Joy Dark, Jill West
Chapter8: Network Infrastructure And Troubleshooting
Section: Chapter Questions
Problem 7TC
Related questions
Question
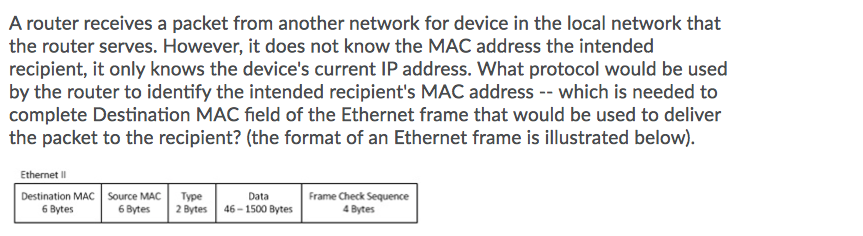
Transcribed Image Text:A router receives a packet from another network for device in the local network that
the router serves. However, it does not know the MAC address the intended
recipient, it only knows the device's current IP address. What protocol would be used
by the router to identify the intended recipient's MAC address -- which is needed to
complete Destination MAC field of the Ethernet frame that would be used to deliver
the packet to the recipient? (the format of an Ethernet frame is illustrated below).
Ethernet II
Destination MAC Source MAC
Туре
2 Bytes
Data
Frame Check Sequence
6 Bytes
6 Bytes
46 - 1500 Bytes
4 Bytes
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 1 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Comptia A+ Core 1 Exam: Guide To Computing Infras…
Computer Science
ISBN:
9780357108376
Author:
Jean Andrews, Joy Dark, Jill West
Publisher:
Cengage Learning

A+ Guide To It Technical Support
Computer Science
ISBN:
9780357108291
Author:
ANDREWS, Jean.
Publisher:
Cengage,

A+ Guide to Hardware (Standalone Book) (MindTap C…
Computer Science
ISBN:
9781305266452
Author:
Jean Andrews
Publisher:
Cengage Learning

Comptia A+ Core 1 Exam: Guide To Computing Infras…
Computer Science
ISBN:
9780357108376
Author:
Jean Andrews, Joy Dark, Jill West
Publisher:
Cengage Learning

A+ Guide To It Technical Support
Computer Science
ISBN:
9780357108291
Author:
ANDREWS, Jean.
Publisher:
Cengage,

A+ Guide to Hardware (Standalone Book) (MindTap C…
Computer Science
ISBN:
9781305266452
Author:
Jean Andrews
Publisher:
Cengage Learning

Management Of Information Security
Computer Science
ISBN:
9781337405713
Author:
WHITMAN, Michael.
Publisher:
Cengage Learning,

Systems Architecture
Computer Science
ISBN:
9781305080195
Author:
Stephen D. Burd
Publisher:
Cengage Learning

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:
9781337569798
Author:
ECKERT
Publisher:
CENGAGE L