Consider the below SWZ: 电烟相相 AC 2E 3D 5F 7E DA What is the best way to secure all the unused ports? Assume that the below Port Security Mac Addresses configuration is a applied on SW2. Specify which port(s) will preform violation? Ports Mac Address
Consider the below SWZ: 电烟相相 AC 2E 3D 5F 7E DA What is the best way to secure all the unused ports? Assume that the below Port Security Mac Addresses configuration is a applied on SW2. Specify which port(s) will preform violation? Ports Mac Address
Comptia A+ Core 1 Exam: Guide To Computing Infrastructure (mindtap Course List)
10th Edition
ISBN:9780357108376
Author:Jean Andrews, Joy Dark, Jill West
Publisher:Jean Andrews, Joy Dark, Jill West
Chapter9: Supporting Mobile Devices
Section: Chapter Questions
Problem 9TC
Related questions
Question
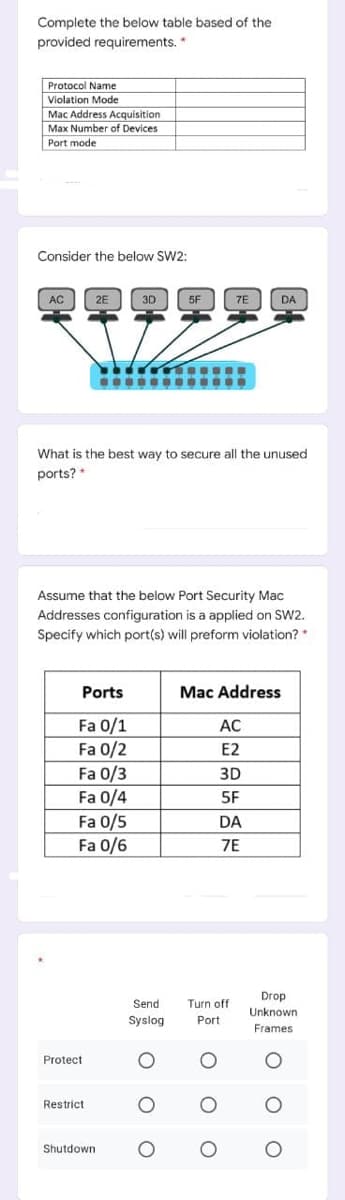
Transcribed Image Text:Complete the below table based of the
provided requirements. *
Protocol Name
Violation Mode
Mac Address Acquisition
Max Number of Devices
Port mode
Consider the below SW2:
相烟相烟烟相
AC
2E
3D
5F
7E
DA
What is the best way to secure all the unused
ports? *
Assume that the below Port Security Mac
Addresses configuration is a applied on SW2.
Specify which port(s) will preform violation?
Ports
Mac Address
Fa 0/1
Fa 0/2
Fa 0/3
Fa 0/4
Fa 0/5
Fa 0/6
AC
E2
3D
5F
DA
7E
Drop
Send
Turn off
Unknown
Syslog
Port
Frames
Protect
Restrict
Shutdown
o o o
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Comptia A+ Core 1 Exam: Guide To Computing Infras…
Computer Science
ISBN:
9780357108376
Author:
Jean Andrews, Joy Dark, Jill West
Publisher:
Cengage Learning

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:
9781337569798
Author:
ECKERT
Publisher:
CENGAGE L

Comptia A+ Core 1 Exam: Guide To Computing Infras…
Computer Science
ISBN:
9780357108376
Author:
Jean Andrews, Joy Dark, Jill West
Publisher:
Cengage Learning

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:
9781337569798
Author:
ECKERT
Publisher:
CENGAGE L