Direction: Match the meanings in column A with the terms in column B to identify the term/word being described.
Direction: Match the meanings in column A with the terms in column B to identify the term/word being described.
Fundamentals of Information Systems
8th Edition
ISBN:9781305082168
Author:Ralph Stair, George Reynolds
Publisher:Ralph Stair, George Reynolds
Chapter1: An Introduction To Information Systems In Organizations
Section: Chapter Questions
Problem 1WE
Related questions
Question
100%
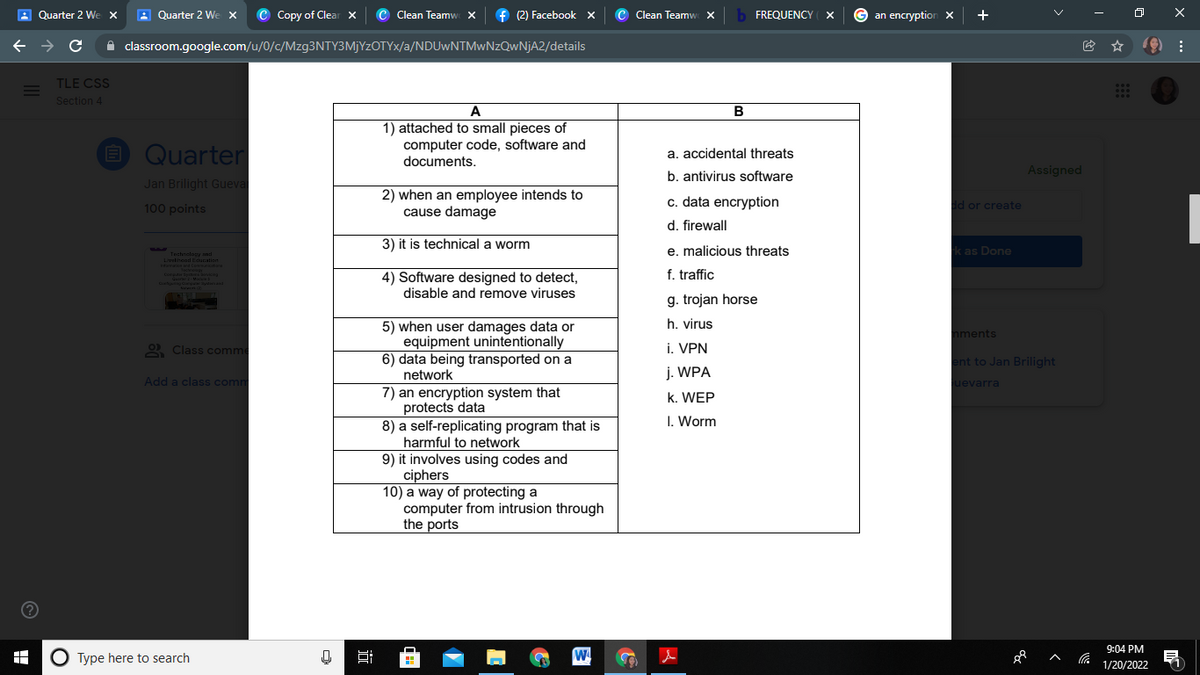
Direction: Match the meanings in column A with the terms in column B to identify
the term/word being described.
Transcribed Image Text:A Quarter 2 We x
A Quarter 2 We x
© Copy of Clear x
C Clean Teamw X
f (2) Facebook x
FREQUENCY
G an encryption
+
O X
Clean Teamw
A classroom.google.com/u/0/c/Mzg3NTY3MjYzOTYx/a/NDUWNTMWNZQWNJA2/details
TLE CSS
Section 4
A
1) attached to small pieces of
computer code, software and
documents.
B
Quarter
a. accidental threats
b. antivirus software
Assigned
Jan Brilight Gueva
2) when an employee intends to
cause damage
c. data encryption
d or create
100 points
d. firewall
3) it is technical a worm
e. malicious threats
k as Done
f. traffic
4) Software designed to detect,
disable and remove viruses
g. trojan horse
h. virus
5) when user damages data or
equipment unintentionally
6) data being transported on a
network
nments
9 Class comme
i. VPN
ent to Jan Brilight
j. WPA
Add a class comm
uevarra
7) an encryption system that
protects data
8) a self-replicating program that is
harmful to network
k. WEP
I. Worm
9) it involves using codes and
ciphers
10) a way of protecting a
computer from intrusion through
the ports
9:04 PM
O Type here to search
1/20/2022
近
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Fundamentals of Information Systems
Computer Science
ISBN:
9781305082168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning

Fundamentals of Information Systems
Computer Science
ISBN:
9781305082168
Author:
Ralph Stair, George Reynolds
Publisher:
Cengage Learning