Given the following Diffie-Hellman scheme, which of the sentences below is/are correct? Select all that apply. Alice to Bob - "I'm Alice", [gª mod plalice Bob to Alice - g mod p {.) is encryption with specified PUBLIC key. [. is encryption with specified PRIVATE key. Trudy can exchange a key between herself and Alice Trudy can share gabmod p with both parties O Trudy can exchange a key between herself and Bob Trudy cannot share any key with the two parties
Given the following Diffie-Hellman scheme, which of the sentences below is/are correct? Select all that apply. Alice to Bob - "I'm Alice", [gª mod plalice Bob to Alice - g mod p {.) is encryption with specified PUBLIC key. [. is encryption with specified PRIVATE key. Trudy can exchange a key between herself and Alice Trudy can share gabmod p with both parties O Trudy can exchange a key between herself and Bob Trudy cannot share any key with the two parties
Programming Logic & Design Comprehensive
9th Edition
ISBN:9781337669405
Author:FARRELL
Publisher:FARRELL
Chapter4: Making Decisions
Section: Chapter Questions
Problem 9RQ
Related questions
Question
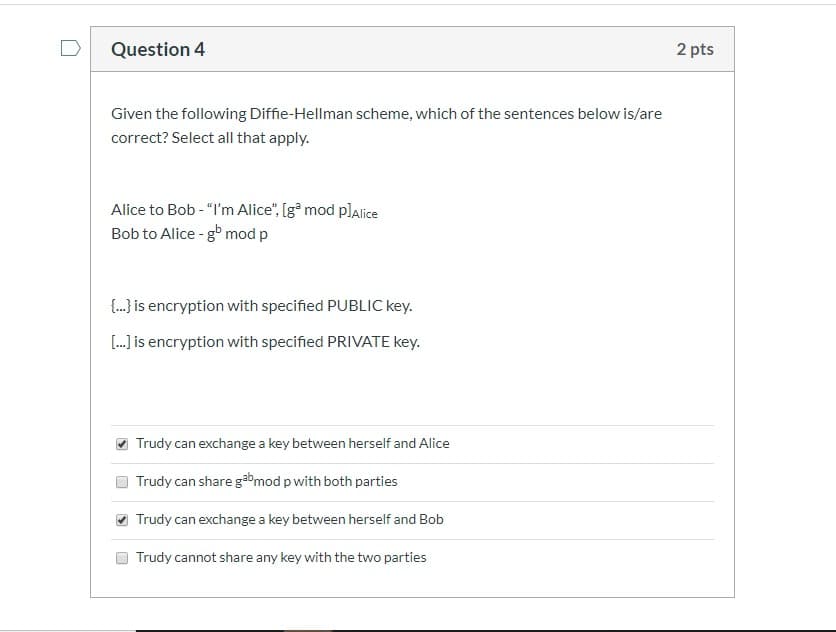
Transcribed Image Text:Given the following Diffie-Hellman scheme, which of the sentences below is/are
correct? Select all that apply.
Alice to Bob - "I'm Alice", [gª mod plalice
Bob to Alice - g mod p
{.) is encryption with specified PUBLIC key.
[. is encryption with specified PRIVATE key.
Trudy can exchange a key between herself and Alice
Trudy can share gabmod p with both parties
O Trudy can exchange a key between herself and Bob
Trudy cannot share any key with the two parties
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Programming Logic & Design Comprehensive
Computer Science
ISBN:
9781337669405
Author:
FARRELL
Publisher:
Cengage

Programming Logic & Design Comprehensive
Computer Science
ISBN:
9781337669405
Author:
FARRELL
Publisher:
Cengage