1. Inventory creation sample of physical assets (devices and systems) within the organization (NIST ID.AM-1)?
Book title:
Chapter 1 - Infrastructure security in the Real world
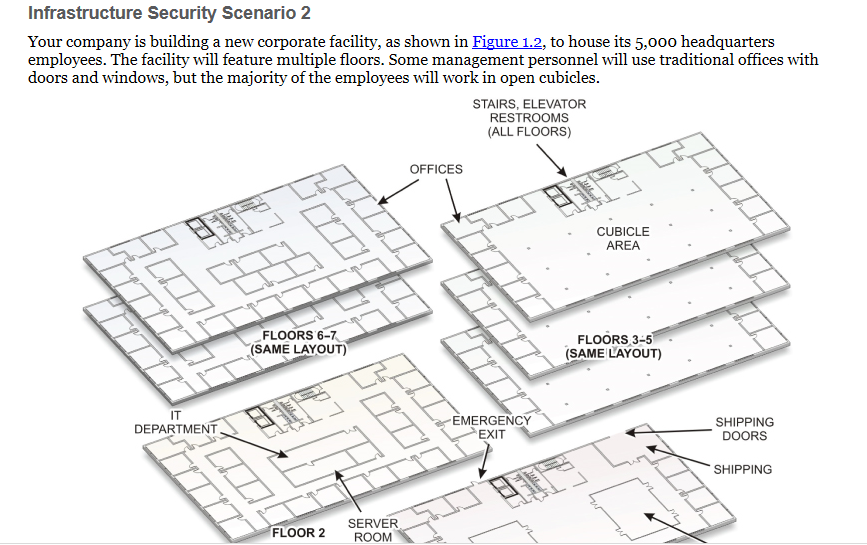
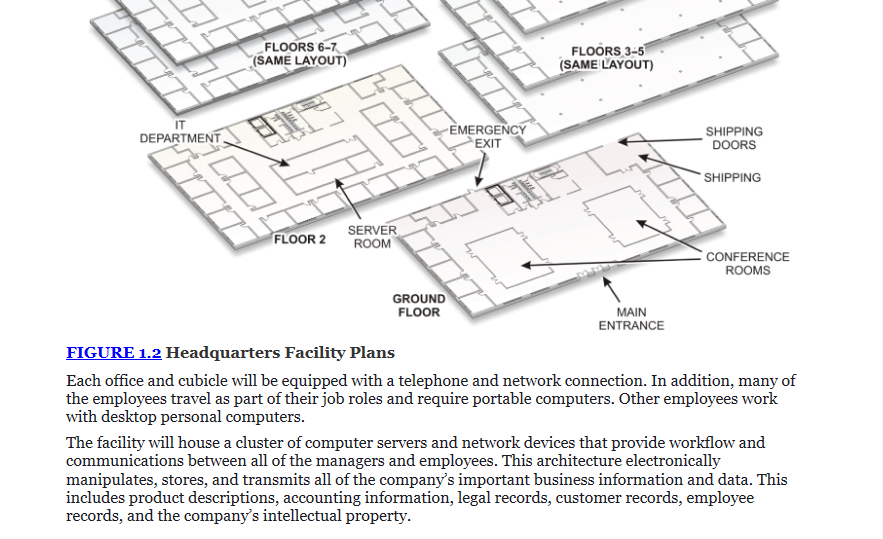
From the information provided in the second scenario, consider the NIST functions detailed in this section and then write what to observe as they relate to each category.
1. Inventory creation sample of physical assets (devices and systems) within the organization (NIST ID.AM-1)?
2. Inventory creation sample of cyber assets (software platforms and applications) within the organization (NIST ID.AM-2).
3. Prioritize the organization’s assets based on their criticality or value to the business functions of the organization (NIST ID.BE-3).
4. Identify any assets that produce dependencies or provide critical functions for any of the organization’s critical services (NIST ID.BE-4).
Create a risk assessment of asset vulnerabilities identified (NIST ID.RA-1, 3).
(Refer to screenshot for reference)
Trending now
This is a popular solution!
Step by step
Solved in 2 steps









