8.0. Create a table as in 8.3.1 Simple fixed-window-size analysis for a network A—R1—R2—R3—B. The A-R1 link is infinitely fast. The R1–R2 and R3–B links have a bandwidth delay of 1 packet/second with no additional propagation delay. The R2-R3 link has a bandwidth delay of 1 packet / 2 seconds, and no propagation delay. The reverse B-A direction (for ACKS) is infinitely fast. Assume winsize = 6. (a). Carry out the table for 10 seconds. Note that you will need to show the queue for both R1 and R2. (b). Continue the table at least partially until T=18, in sufficient detail that you can verify that RTT actual for packet 8 is as calculated in the previous exercise. To do this you will need more than 10 packets, but fewer than 16; the use of hex labels A, B, C for packets 10, 11, 12 is a convenient notation.
8.0. Create a table as in 8.3.1 Simple fixed-window-size analysis for a network A—R1—R2—R3—B. The A-R1 link is infinitely fast. The R1–R2 and R3–B links have a bandwidth delay of 1 packet/second with no additional propagation delay. The R2-R3 link has a bandwidth delay of 1 packet / 2 seconds, and no propagation delay. The reverse B-A direction (for ACKS) is infinitely fast. Assume winsize = 6. (a). Carry out the table for 10 seconds. Note that you will need to show the queue for both R1 and R2. (b). Continue the table at least partially until T=18, in sufficient detail that you can verify that RTT actual for packet 8 is as calculated in the previous exercise. To do this you will need more than 10 packets, but fewer than 16; the use of hex labels A, B, C for packets 10, 11, 12 is a convenient notation.
Principles of Information Security (MindTap Course List)
6th Edition
ISBN:9781337102063
Author:Michael E. Whitman, Herbert J. Mattord
Publisher:Michael E. Whitman, Herbert J. Mattord
Chapter6: Security Technology: Access Controls, Firewalls, And Vpns
Section: Chapter Questions
Problem 2RQ
Related questions
Question
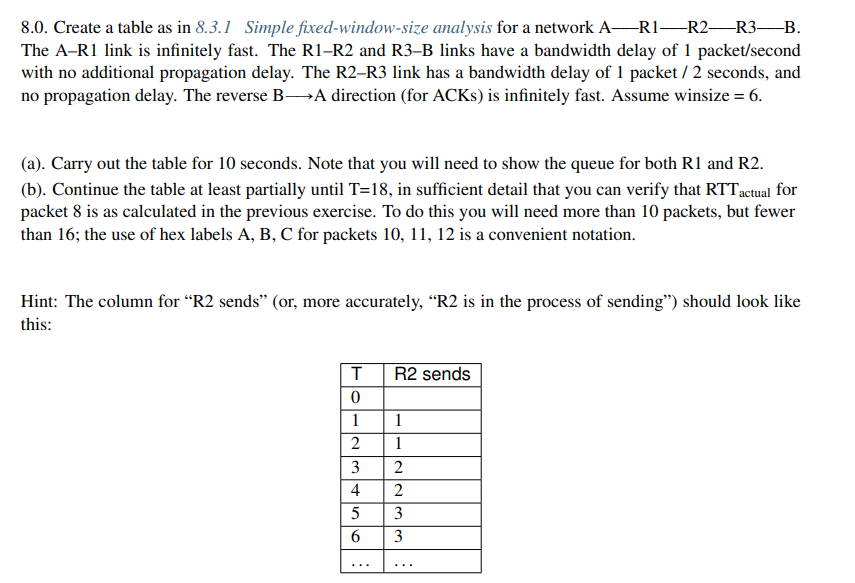
Transcribed Image Text:8.0. Create a table as in 8.3.1 Simple fixed-window-size analysis for a network A-R1 R2 R3-B.
The A-R1 link is infinitely fast. The R1-R2 and R3-B links have a bandwidth delay of 1 packet/second
with no additional propagation delay. The R2-R3 link has a bandwidth delay of 1 packet / 2 seconds, and
no propagation delay. The reverse B-A direction (for ACKS) is infinitely fast. Assume winsize = 6.
(a). Carry out the table for 10 seconds. Note that you will need to show the queue for both R1 and R2.
(b). Continue the table at least partially until T=18, in sufficient detail that you can verify that RTT actual for
packet 8 is as calculated in the previous exercise. To do this you will need more than 10 packets, but fewer
than 16; the use of hex labels A, B, C for packets 10, 11, 12 is a convenient notation.
Hint: The column for "R2 sends” (or, more accurately, "R2 is in the process of sending") should look like
this:
T
0
1
2
3
456
R2 sends
1
1
2
223
2
3
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 5 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Principles of Information Security (MindTap Cours…
Computer Science
ISBN:
9781337102063
Author:
Michael E. Whitman, Herbert J. Mattord
Publisher:
Cengage Learning

Principles of Information Security (MindTap Cours…
Computer Science
ISBN:
9781337102063
Author:
Michael E. Whitman, Herbert J. Mattord
Publisher:
Cengage Learning