a. Thinking ahead to implementing the hide and recover meth- ods, declare in this part any additional instance variables you will need and any additional code you may need in the constructor. // instance variables private String myCode; public Code (String code) { myCode = code; } b. Implement the hide method. c. Implement the recover method.
a. Thinking ahead to implementing the hide and recover meth- ods, declare in this part any additional instance variables you will need and any additional code you may need in the constructor. // instance variables private String myCode; public Code (String code) { myCode = code; } b. Implement the hide method. c. Implement the recover method.
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
The question is in the attached photos!

Transcribed Image Text:a. Thinking ahead to implementing the hide and recover meth-
will need and any additional code you may need in the
ods, declare in this part any additional instance variables
constructor.
// instance variables
private String myCode;
public Code (String code)
{
myCode = code;
}
b. Implement the hide method.
c. Implement the recover method.
you
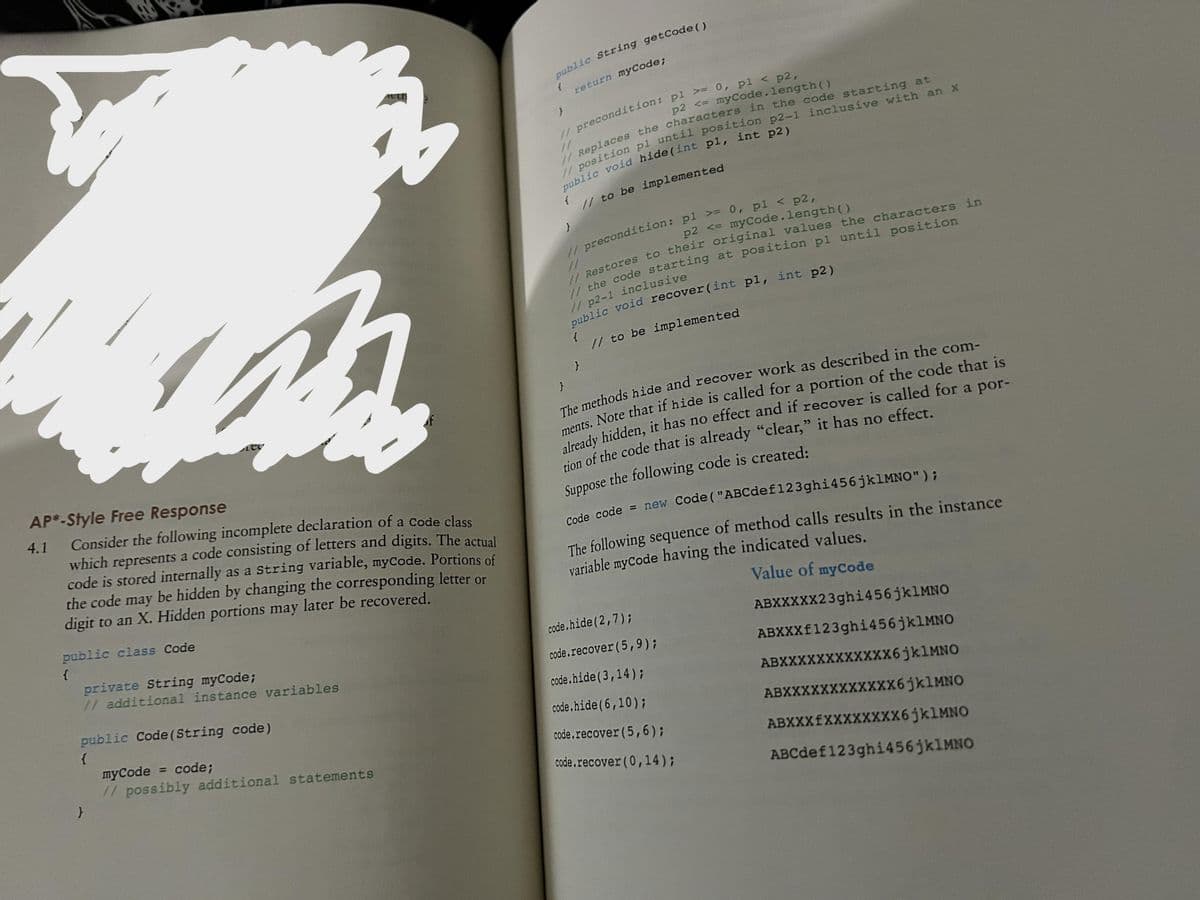
Transcribed Image Text:AP*-Style Free Response
Consider the following incomplete declaration of a code class
which represents a code consisting of letters and digits. The actual
code is stored internally as a string variable, myCode. Portions of
the code may be hidden by changing the corresponding letter or
digit to an X. Hidden portions may later be recovered.
4.1
public class Code
{
private String myCode;
// additional instance variables
public Code (String code)
{
3
}
myCode = code;
// possibly additional statements
public String getCode ()
(
}
// precondition: pl >= 0, pl < p2,
p2 <= myCode.length()
// Replaces the characters in the code starting at
// position pl until position p2-1 inclusive with an X
public void hide (int pl, int p2)
{
return myCode;
}
// precondition: pl >= 0, pl < p2,
p2 <= myCode.length()
// Restores to their original values the characters in
// to be implemented
// the code starting at position pl until position
// p2-1 inclusive
public void recover (int pl, int p2)
}
{
}
// to be implemented
The methods hide and recover work as described in the com-
ments. Note that if hide is called for a portion of the code that is
already hidden, it has no effect and if recover is called for a por-
tion of the code that is already "clear," it has no effect.
Suppose the following code is created:
Code code = new Code ("ABCdef 123ghi456jklMNO");
The following sequence of method calls results in the instance
variable mycode having the indicated values.
Value of myCode
ABXXXXX23ghi456jklMNO
ABXXXf123ghi456 jklMNO
ABXXXXXXXXXXXX6jklMNO
ABXXXXXXXXXXXX6jklMNO
ABXXXfXXXXXXXX6jklMNO
ABCdef123ghi456jklMNO
code.hide (2,7);
code.recover (5,9);
code.hide (3,14);
code.hide (6, 10);
code.recover (5,6);
code.recover (0,14);
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 4 steps with 3 images

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY