c) Suppose a router has built up the routing table shown in Table below: SubnetNumber SubnetMask NextHop 255.255.254.0 Interface 0 255.255.254.0 Interface 1 128.96.170.0 128.96.168.0 128.96.166.0 255.255.254.0 R2 128.96.164.0 255.255.252.0 R3 (defaule) R4 The router can deliver packets directly over interfaces 0 and 1, or it can forward packets to routers R2, R3, or R4. Assume the router does the longest prefix match. Describe what the router does with a packet addressed to each of the following destinations: i. 128.96.167.151. ii. 128.96.163.151 iii. 128.96.169.192. iv. 128.96.165.121. v. 171.1.2.3
c) Suppose a router has built up the routing table shown in Table below: SubnetNumber SubnetMask NextHop 255.255.254.0 Interface 0 255.255.254.0 Interface 1 128.96.170.0 128.96.168.0 128.96.166.0 255.255.254.0 R2 128.96.164.0 255.255.252.0 R3 (defaule) R4 The router can deliver packets directly over interfaces 0 and 1, or it can forward packets to routers R2, R3, or R4. Assume the router does the longest prefix match. Describe what the router does with a packet addressed to each of the following destinations: i. 128.96.167.151. ii. 128.96.163.151 iii. 128.96.169.192. iv. 128.96.165.121. v. 171.1.2.3
Principles of Information Security (MindTap Course List)
6th Edition
ISBN:9781337102063
Author:Michael E. Whitman, Herbert J. Mattord
Publisher:Michael E. Whitman, Herbert J. Mattord
Chapter6: Security Technology: Access Controls, Firewalls, And Vpns
Section: Chapter Questions
Problem 2RQ
Related questions
Question
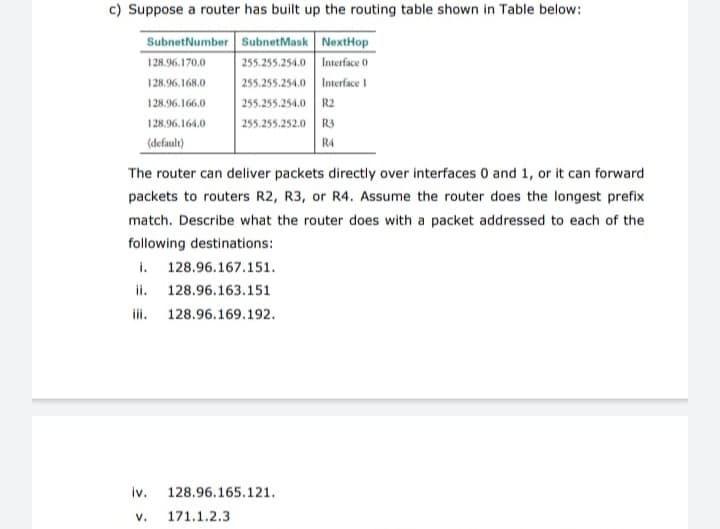
Transcribed Image Text:c) Suppose a router has built up the routing table shown in Table below:
SubnetNumber SubnetMask NextHop
255.255.254.0 Interface ()
255.255.254.0 Interface 1
128.96.170.0
128.96.168.0
128.96.166,0
255.255.254.0
R2
128.96.164.0
255.255.252.0 R3
(defaule)
R4
The router can deliver packets directly over interfaces 0 and 1, or it can forward
packets to routers R2, R3, or R4. Assume the router does the longest prefix
match. Describe what the router does with a packet addressed to each of the
following destinations:
i. 128.96.167.151.
ii. 128.96.163.151
ii.
128.96.169.192.
iv.
128.96.165.121.
v.
171.1.2.3
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 2 images

Recommended textbooks for you

Principles of Information Security (MindTap Cours…
Computer Science
ISBN:
9781337102063
Author:
Michael E. Whitman, Herbert J. Mattord
Publisher:
Cengage Learning

Systems Architecture
Computer Science
ISBN:
9781305080195
Author:
Stephen D. Burd
Publisher:
Cengage Learning

Principles of Information Security (MindTap Cours…
Computer Science
ISBN:
9781337102063
Author:
Michael E. Whitman, Herbert J. Mattord
Publisher:
Cengage Learning

Systems Architecture
Computer Science
ISBN:
9781305080195
Author:
Stephen D. Burd
Publisher:
Cengage Learning