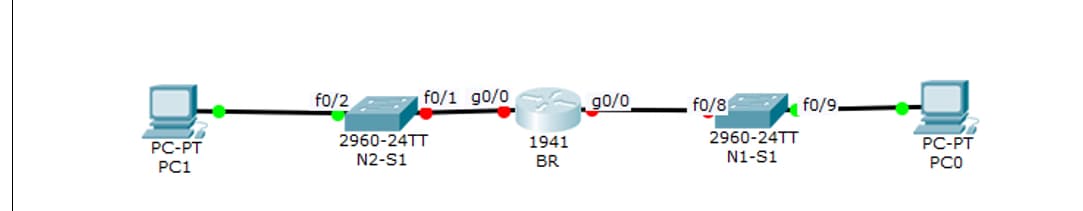
(Cisco Packet Tracer) Requirements A. Configure PCs host IP settings B. Configure the basic router 1. Prevent the router from attempting to translate incorrectly entered commands 2. Configure host names as shown in the topology. 3. Configure interface IP addresses . 4. set ciscoprv as the privilege password and ciscocon as the console passwords . 5. Vty lines accept Telnet connection only. Set ciscovty as the password for these lines. 6. Test vty connection using a telnet command and make any required setting to complete this connection. C. Configure the switches: 1. The initial settings: - Configure host names as shown in the topology. - Banner that includes the word warning - Console port login and password cPass - Encrypted enable password of pPass - Encrypt plain text passwords - Management interface addressing 2. Configure SSH to secure remote access with the following settings: - RSA key-pair parameters to support SSH version 2 - Set SSH version 2 - VTY lines only accept SSH connections and use local login for authentication - Test this secure connection and make any required setting to complete this connection. Note : To configure the above topology , use valid IPs of the private address ranges.
(Cisco Packet Tracer) Requirements A. Configure PCs host IP settings B. Configure the basic router 1. Prevent the router from attempting to translate incorrectly entered commands 2. Configure host names as shown in the topology. 3. Configure interface IP addresses . 4. set ciscoprv as the privilege password and ciscocon as the console passwords . 5. Vty lines accept Telnet connection only. Set ciscovty as the password for these lines. 6. Test vty connection using a telnet command and make any required setting to complete this connection. C. Configure the switches: 1. The initial settings: - Configure host names as shown in the topology. - Banner that includes the word warning - Console port login and password cPass - Encrypted enable password of pPass - Encrypt plain text passwords - Management interface addressing 2. Configure SSH to secure remote access with the following settings: - RSA key-pair parameters to support SSH version 2 - Set SSH version 2 - VTY lines only accept SSH connections and use local login for authentication - Test this secure connection and make any required setting to complete this connection. Note : To configure the above topology , use valid IPs of the private address ranges.
Enhanced Discovering Computers 2017 (Shelly Cashman Series) (MindTap Course List)
1st Edition
ISBN:9781305657458
Author:Misty E. Vermaat, Susan L. Sebok, Steven M. Freund, Mark Frydenberg, Jennifer T. Campbell
Publisher:Misty E. Vermaat, Susan L. Sebok, Steven M. Freund, Mark Frydenberg, Jennifer T. Campbell
Chapter7: Input And Output: Extending Capabilities Of Computers And Mobile Devices
Section: Chapter Questions
Problem 5TF
Related questions
Question
(Cisco Packet Tracer)
Requirements
A. Configure PCs host IP settings
B. Configure the basic router
1. Prevent the router from attempting to translate incorrectly entered commands
2. Configure host names as shown in the topology.
3. Configure interface IP addresses .
4. set ciscoprv as the privilege password and ciscocon as the console passwords .
5. Vty lines accept Telnet connection only. Set ciscovty as the password for these lines.
6. Test vty connection using a telnet command and make any required setting to complete this connection.
C. Configure the switches:
1. The initial settings:
- Configure host names as shown in the topology.
- Banner that includes the word warning
- Console port login and password cPass
- Encrypted enable password of pPass
- Encrypt plain text passwords
- Management interface addressing
2. Configure SSH to secure remote access with the following settings:
- RSA key-pair parameters to support SSH version 2
- Set SSH version 2
- VTY lines only accept SSH connections and use local login for authentication
- Test this secure connection and make any required setting to complete this connection.
Note : To configure the above topology , use valid IPs of the private address ranges.
Transcribed Image Text:f0/2
f0/1 g0/0
fo/8
90/0
fo/9.
2960-24TT
2960-24TT
N1-S1
PC-PT
PC-PT
1941
N2-S1
BR
PCO
PC1
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps with 8 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Enhanced Discovering Computers 2017 (Shelly Cashm…
Computer Science
ISBN:
9781305657458
Author:
Misty E. Vermaat, Susan L. Sebok, Steven M. Freund, Mark Frydenberg, Jennifer T. Campbell
Publisher:
Cengage Learning

Systems Architecture
Computer Science
ISBN:
9781305080195
Author:
Stephen D. Burd
Publisher:
Cengage Learning

Enhanced Discovering Computers 2017 (Shelly Cashm…
Computer Science
ISBN:
9781305657458
Author:
Misty E. Vermaat, Susan L. Sebok, Steven M. Freund, Mark Frydenberg, Jennifer T. Campbell
Publisher:
Cengage Learning

Systems Architecture
Computer Science
ISBN:
9781305080195
Author:
Stephen D. Burd
Publisher:
Cengage Learning