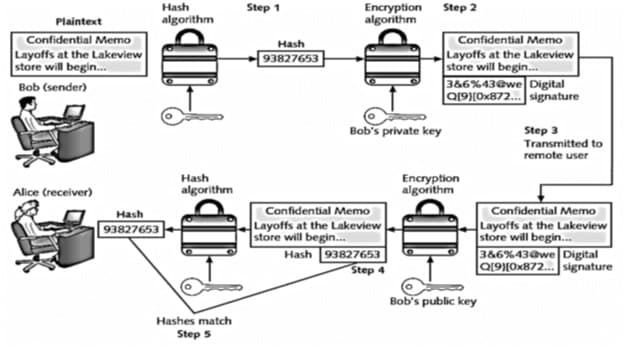
e to Alice and then answer the questions that follow: The statements below are the text version of the illustrated steps (step one to step five in the diagram above). Read each statement (step) and then correct all that are false. These are the steps for Bob to send a digitally signed message to Alice: Step
Study the diagram below showing the steps for Bob to send a digitally signed
message to Alice and then answer the questions that follow:
The statements below are the text version of the illustrated steps
(step one to step five in the diagram above).
Read each statement (step) and then correct all that are false.
These are the steps for Bob to send a digitally signed message to
Alice:
| Step Number |
Statement |
| 1 | After creating a memo, Alice generates a hash on it. |
| 2 | Bob then encrypts the hash with a public key. This encryption is a digital signature of the hash. |
| 3 | Bob only sends the digital signature to Alice. |
| 4 | When Alice receives them, she descripts the digital signature using Bob’s public key, revealing the hash. |
| 5 | Alice then hashes the memo with the different hash hash she received from Bob. |
You have verified that the correct keys have been used either encrypting and/or
decrypting the digital signatures as well as the correct has algorithm is used to hash
the memo.
Explain the implications of the following scenarios:
If Alice could not decrypt the digital signature.
If, after Alice hashing the memo, the hashes are not equal.
Trending now
This is a popular solution!
Step by step
Solved in 2 steps









