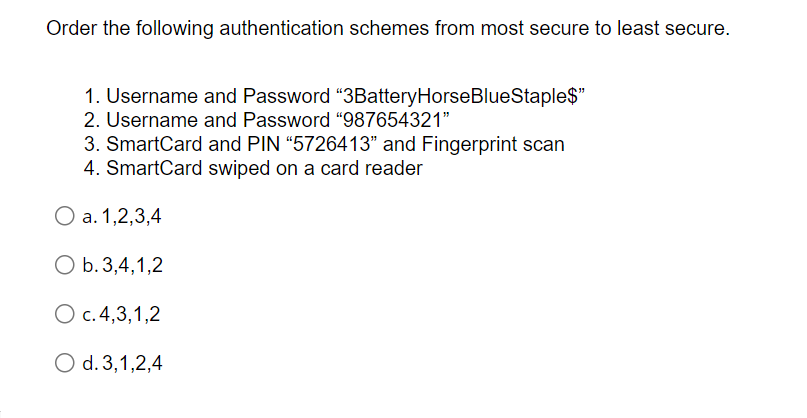
Order the following authentication schemes from most secure to least secure. 1. Username and Password "3BatteryHorseBlueStaple$" 2. Username and Password "987654321" 3. SmartCard and PIN "5726413" and Fingerprint scan 4. SmartCard swiped on a card reader O a. 1,2,3,4 O b. 3,4,1,2 O c. 4,3,1,2 O d. 3,1,2,4
Introduction
Authentication Schemas:
Authentication schemes are methods used to verify the identity of a user or system, ensuring that only authorized access is granted. Some common types of authentication schemes include:
-
Usernames and Passwords: This is a basic method of authentication that requires the user to enter a unique username and password. Passwords can be simple or complex and can be stored securely on a server or device.
-
Two-Factor Authentication (2FA): This method of authentication requires the user to provide two forms of identification, such as a password and a fingerprint scan or a password and a code sent to a mobile device.
-
Smart Cards: Smart Cards are physical tokens that store information about the user and are used to verify their identity. They can be swiped on a card reader or combined with a PIN or biometric scan for added security.
-
Biometric Authentication: This method of authentication uses biometric data such as fingerprints, facial recognition, or iris scans to verify the identity of the user.
-
Certificate-based Authentication: This method of authentication uses digital certificates and public key infrastructure (PKI) to verify the identity of the user.
The choice of authentication scheme will depend on the level of security required, the resources available, and the user's needs. A combination of different authentication methods can also be used for added security.
Trending now
This is a popular solution!
Step by step
Solved in 3 steps


