The key to cracking a substitution cipher was first discovered by Arab scholars in the ninth century, but it was not widely known in the West until the fifteenth century. Once frequency analysis of ciphers became widespread, the plain substitution cipher became useless. To fix the problems in the substitution cipher, Blaise de Vigenère invented the strategy of using multiple letter mappings. Rather than using one key for the whole message, Vigenère’s idea was to use a different key for each letter of the message. Using a different key for each letter makes the frequency analysis much more difficult.
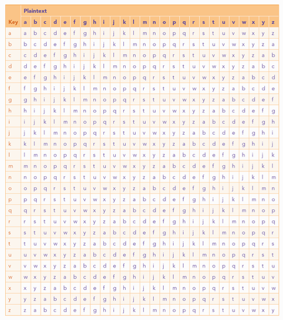
The key to the Vigenère cipher is the Vigenère square. The rows shown here are simple rotations of the alphabet. Each row in the table shifts the letters of the alphabet one place to the left. When a letter shifts out of the first .
The idea is to have the message we want to encode: secretmessage
Alongside a word we will use to encrypt: encryptencrypt
|
Plaint text |
s |
e |
c |
r |
e |
t |
m |
e |
s |
s |
a |
g |
e |
|
Key |
e |
n |
c |
r |
y |
p |
t |
e |
n |
c |
r |
y |
p |
To create the cipher text, match the plain text with the key:
|
Cipher text |
w |
r |
e |
h |
b |
h |
e |
i |
e |
u |
r |
d |
t |
Your program instructions:
You will create two functions, one to encrypt and one to decrypt. Write a function to encrypt a message using the Vigenere cipher. Your function will need to take in two arguments in the parameters, a key to encrypt the message and a message to encrypt. It will return the ciphertext. Create the second function to take in the cipher text and return the original message.
Step by step
Solved in 3 steps with 1 images


