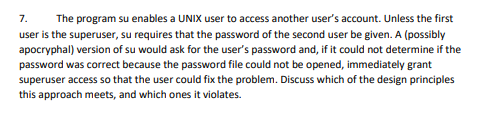
7. The program su enables a UNIX user to access another user's account. Unless the first user is the superuser, su requires that the password of the second user be given. A (possibly apocryphal) version of su would ask for the user's password and, if it could not determine if the password was correct because the password file could not be opened, immediately grant superuser access so that the user could fix the problem. Discuss which of the design principles this approach meets, and which ones it violates.
7. The program su enables a UNIX user to access another user's account. Unless the first user is the superuser, su requires that the password of the second user be given. A (possibly apocryphal) version of su would ask for the user's password and, if it could not determine if the password was correct because the password file could not be opened, immediately grant superuser access so that the user could fix the problem. Discuss which of the design principles this approach meets, and which ones it violates.
Operations Research : Applications and Algorithms
4th Edition
ISBN:9780534380588
Author:Wayne L. Winston
Publisher:Wayne L. Winston
Chapter20: Queuing Theory
Section20.10: Exponential Queues In Series And Open Queuing Networks
Problem 10P
Related questions
Question
Transcribed Image Text:7.
The program su enables a UNIX user to access another user's account. Unless the first
user is the superuser, su requires that the password of the second user be given. A (possibly
apocryphal) version of su would ask for the user's password and, if it could not determine if the
password was correct because the password file could not be opened, immediately grant
superuser access so that the user could fix the problem. Discuss which of the design principles
this approach meets, and which ones it violates.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution!
Trending now
This is a popular solution!
Step by step
Solved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Recommended textbooks for you

Operations Research : Applications and Algorithms
Computer Science
ISBN:
9780534380588
Author:
Wayne L. Winston
Publisher:
Brooks Cole

Operations Research : Applications and Algorithms
Computer Science
ISBN:
9780534380588
Author:
Wayne L. Winston
Publisher:
Brooks Cole