C. Jamal Encryption time limit per test: 1 second memory limit per test: 256 megabytes input: standard input output: standard output Jamal is a student in one of the UAE colleges. He has suggested the following code encryption. 1. The input is a positive integer in base 10. 2. First, it is converted to base 3. 3. Then, each digit d, is converted into (d, + 1) mod 3. In other words, 0 is converted into 1, 1 is converted into 2, 2 is converted into 0. 4. Resulting base 3 number is converted back to base 10. Your task is to implement Jamal's encryption code. Below is a description of what is a base 3 numeral system. Each positive integer n can be uniquely represented as sum do · 30 + d 3+ d2 32 +... + d, · 3', where d, > 0 and each d, satisfies 0 < d; < 2. Each d; is called a digit. Sequence of d; is called base 3 representation of n. Note, that uniqueness of representation holds for any base k > 1 numeral system. In particular, usually we are using base 10 numeral system, and for us it is natural that such representation is unique. Input First line of input contains single positive integer n (1
C. Jamal Encryption time limit per test: 1 second memory limit per test: 256 megabytes input: standard input output: standard output Jamal is a student in one of the UAE colleges. He has suggested the following code encryption. 1. The input is a positive integer in base 10. 2. First, it is converted to base 3. 3. Then, each digit d, is converted into (d, + 1) mod 3. In other words, 0 is converted into 1, 1 is converted into 2, 2 is converted into 0. 4. Resulting base 3 number is converted back to base 10. Your task is to implement Jamal's encryption code. Below is a description of what is a base 3 numeral system. Each positive integer n can be uniquely represented as sum do · 30 + d 3+ d2 32 +... + d, · 3', where d, > 0 and each d, satisfies 0 < d; < 2. Each d; is called a digit. Sequence of d; is called base 3 representation of n. Note, that uniqueness of representation holds for any base k > 1 numeral system. In particular, usually we are using base 10 numeral system, and for us it is natural that such representation is unique. Input First line of input contains single positive integer n (1
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:James Kurose, Keith Ross
Chapter1: Computer Networks And The Internet
Section: Chapter Questions
Problem R1RQ: What is the difference between a host and an end system? List several different types of end...
Related questions
Question
double check please in python, notgradedquestion
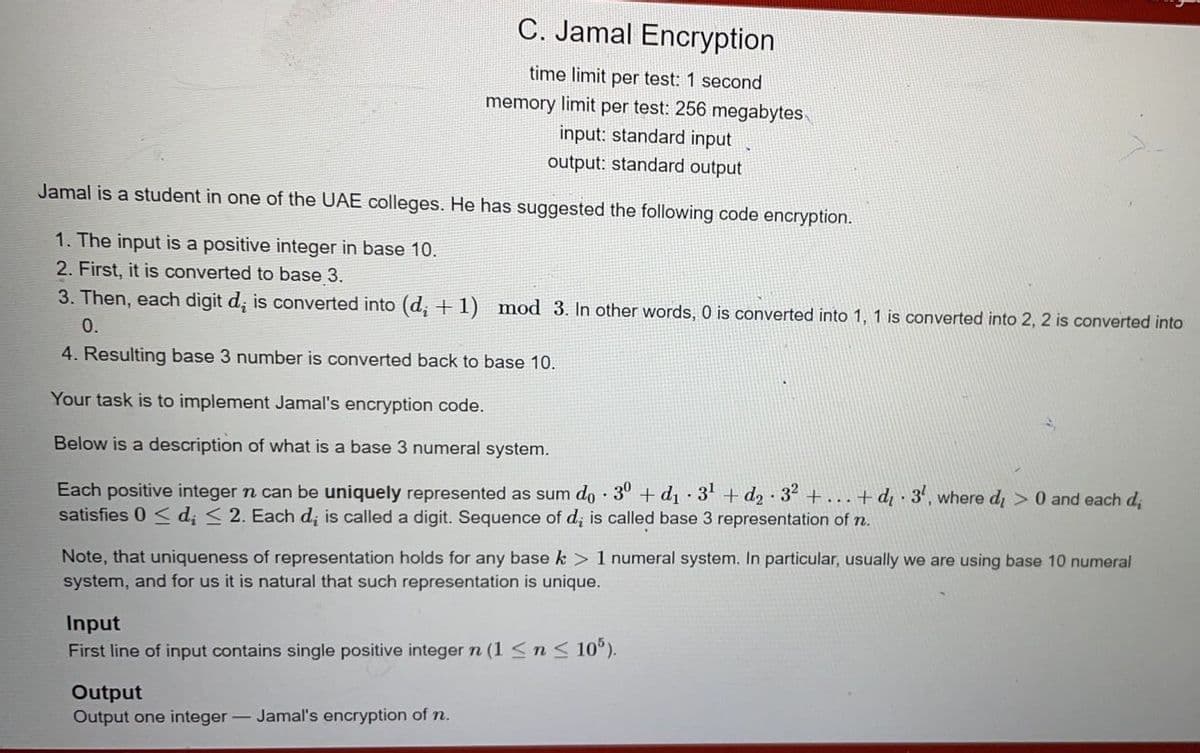
Transcribed Image Text:C. Jamal Encryption
time limit per test: 1 second
memory limit per test: 256 megabytes
input: standard input
output: standard output
Jamal is a student in one of the UAE colleges. He has suggested the following code encryption.
1. The input is a positive integer in base 10.
2. First, it is converted to base 3.
3. Then, each digit d, is converted into (d, + 1) mod 3. In other words, 0 is converted into 1, 1 is converted into 2, 2 is converted into
0.
4. Resulting base 3 number is converted back to base 10.
Your task is to implement Jamal's encryption code.
Below is a description of what is a base 3 numeral system.
Each positive integer n can be uniquely represented as sum do 30 +d1 3' + d2 32 +...+ dq · 3', where d, > 0 and each d,
satisfies 0 < d; < 2. Each d, is called a digit. Sequence of d; is called base 3 representation of n.
Note, that uniqueness of representation holds for any base k > 1 numeral system. In particular, usually we are using base 10 numeral
system, and for us it is natural that such representation is unique.
Input
First line of input contains single positive integer n (1 <n < 10°).
Output
Output one integer- Jamal's encryption of n.

Transcribed Image Text:Examples
input
Copy
output
Copy
input
Copy
9.
output
Copy
22
input
Copy
21
Copy
output
Note
In the first example, 2 = 2-1 in base 10 is represented as 2 in base 3. Applying our transformation, we get 0 in base 3. Converting it back
we get 0 in base 10.
In the second example, 9 =0.1+0.3+1.9 in base 10 is represented as 100 in base 3. Applying our transformation, we get 211 in
base 3. Converting it back we get 1 1+ 1.3+2.9%3 22.
In the third example, 21 in base 10 is represented as 210 in base 3. Applying transformation we get 021 (note that we have leading zero),
converting to base 10 we get 7.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by step
Solved in 4 steps with 2 images

Recommended textbooks for you

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Computer Networking: A Top-Down Approach (7th Edi…
Computer Engineering
ISBN:
9780133594140
Author:
James Kurose, Keith Ross
Publisher:
PEARSON

Computer Organization and Design MIPS Edition, Fi…
Computer Engineering
ISBN:
9780124077263
Author:
David A. Patterson, John L. Hennessy
Publisher:
Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:
9781337569330
Author:
Jill West, Tamara Dean, Jean Andrews
Publisher:
Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:
9781337093422
Author:
Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:
Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:
9780133750423
Author:
VENIT, Stewart
Publisher:
Pearson Education

Sc Business Data Communications and Networking, T…
Computer Engineering
ISBN:
9781119368830
Author:
FITZGERALD
Publisher:
WILEY