
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
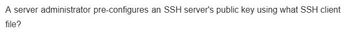
Transcribed Image Text:A server administrator pre-configures an SSH server's public key using what SSH client
file?
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- What is the name of the file on the SSH client that an administrator must use in order to pre-configure the public key for an SSH server?arrow_forwardWhat is the name of the SSH client file that a server administrator uses to set up an SSH server's public key in advance?arrow_forwardTo pre-configure the public key of an SSH server, an administrator must first generate an SSH client file containing the server's public key.arrow_forward
- How can an administrator use the SSH client to pre-configure the public key of an SSH server?arrow_forwardExperiencing slowdowns in performance is possible while using an application proxy due to the challenges of decrypting end-to-end encrypted traffic. It is possible that a proxy server might benefit from a solution that allows for communication via an encrypted protocol at the application layer.arrow_forwardEnterprise Virus Protection: You are the new system administrator for Precision Accounting Services, which has 45 computers on its network running Windows Defender Antivirus. All the computers have access to the Internet and update antivirus definitions as required. Last week, several users received an email with a link to an executable file stored on a cloud-based file sharing service. One user was tricked into downloading and running the malware. This malware was detected by Windows Defender Antivirus, but it could not be removed from memory while running. The user did not understand the malware detection messages and did not inform you. This created a security risk because the malware ran for an extended period and began accessing network file shares. How can you prevent this in the future?arrow_forward
- Note FTP ports. FTP transports control data "out of band," as is often believed?arrow_forwardHow can a client predict that a server request will fail?arrow_forwardWhat is the name of the file on the SSH client that an administrator has to utilize in order to pre-configure the public key for an SSH server?arrow_forward
- Network Security: A process can be in one of three states: running,ready, and blocked. A job is a kind of processand can be in one of three states: foreground, background, and paused. What’s the similarity between the three process states and the three job states? Hint: It’s not a one-to-one mapping.arrow_forwardHow can an administrator pre-configure the public key of an SSH server using the SSH client?arrow_forwardHow can an administrator pre-configure the public key of an SSH server using the SSH client?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education