
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
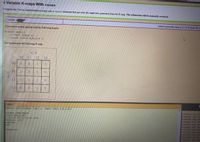
Transcribed Image Text:4 Variable K-maps With casez
Complete the Verilog implementation using only a casez statement that provides the implicates generated from the Kmap The sabmission will be mannally reviewed
Exercise 2
uhmit successful, time is 1316 30 hos 207.1
Complete a verilog module with the following header:
module testi(
output logic y.
input logic a,b,c,d ):
that inplements the following K-map:
C,d
00
01
11
10
00
01
11
1.
1
10
Editor
module teati (output 1ogic y, inpus logie s,b,c.dlz
alwaya comb begin
-00010 tt ve
EM00020 tat ve
1.5,6, ,10,11,13,141 y-1:
defaulti y-0I
endcase
end
E-O0040 Lt ve
endnodule
1,
1.
1.
1.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 4 steps with 2 images

Knowledge Booster
Similar questions
- language: Python Problem: Define a global variable, countcalls, and increment it inside a power(x, n) function, so that it counts the number of times the power function is called. Show that it produces the expected number of calls for power(2, 10) and power(5, 10) and power(5, 0), each separately.arrow_forwardWrite a kotlin code that tracks how much energy was produced in watts when a mobile phone is connected to its charger.arrow_forwardWrite in C Language Description Please write a program that read in anexpression and give its result. Input Input will be an expression content only digit, +, -, /, * and space. Output Please output the result of expression without consider the priority of +, -, *, /. When you do thedivision, please round down to integer. Sample Input 1 1 + 2 * 3 / 4 Sample Output 1 2arrow_forward
- Do it in C++ and use 1D and nested while loops for Fancy Print- 8 queensarrow_forwardZybooks C++ 1.7 LAB: Introduction to data structures labs Step 1: Producing correct output Three commented-out lines of code exist in main(). Uncomment the lines and click the "Run program" button. Verify that the program's output is: 2 + 2 = 4 Unknown function: PrintPlus2 Secret string: "abc" Submit your code for grading. Your submission will pass the "Compare output" test only, achieving 1 of the possible 10 points. Step 2: Inspecting the LabPrinter class Inspect the LabPrinter class implemented in the LabPrinter.h file. Access LabPrinter.h by clicking on the orange arrow next to main.cpp at the top of the coding window. Member functions Print2Plus2() and PrintSecret() print strings using std::cout. Step 3: Implementing CallFunctionNamed() Remove the three uncommented lines from main(). Then implement the CallFunctionNamed() function in main.cpp to handle three cases: If functionName is "Print2Plus2", call printer's Print2Plus2() member function. If functionName is "PrintSecret",…arrow_forwardThis needs to be done in C Programming. A manufacturing plant has an alarm monitor program that reports any of sixteen possible alarms. A 16-bit variable ALARM is examined, and each 1 bit found corresponds to an active alarm. The alarms are numbered 1 – 16, with the least significant bit (LSB) corresponding to Alarm 1 and the most significant bit (MSB) corresponding to Alarm 16. Prompt for the unsigned short integer ALARM, and then use bitwise logic to determine and display all corresponding active alarms, e.g., output “Alarm 12 Active”.arrow_forward
- THE TOPIC IS ALL ABOUT FOR LOOP. USING C PROGRAMMING ONLYarrow_forwardNeed help with this c++ codearrow_forwardConsider the following common task done repeatedly:• Read the next input (x = read())• If the input is not valid (valid(x)), exit the loop• Print the input read (print(x))• Repeat the loopUsing C++ syntax:Write the loop above using a pretest loop, posttest loop and a user-located loop control mechanism. From the three which one is more readable and why?arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY