
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Transcribed Image Text:1
6
0
2
4
7
3
5
Graph G
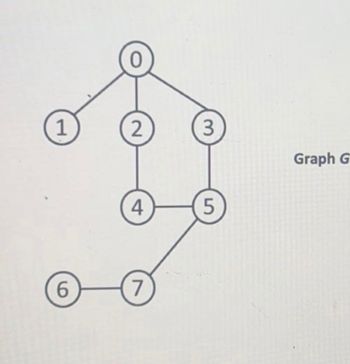
![Given the graph G from Question 2, using the Graph Breadth-First Search algorithm with a Queue,
please do the following:
Assume that the start node is 4 (e.g. node = 4),
Demonstrate a step-by-step, manual desk-check execution of the BFS algorithm, showing the values of
all variables and arrays (e.g. visited, inqueue, Q) for each step in each cycle of each loop, as
demonstrated in class. [
Algorithm: Graph breadth-first search
BFS (G, node) →visited
3
4
5
6
Input: G = (V, E), a graph
node, the starting vertex in G
1
2 visited CreateArray (VI)
10
11
Output: visited, an array of size [V] such that visited[i] is TRUE if we
have visited node i, FALSE otherwise
Q-CreateQueue ()
-
inqueue - CreateArray (VI)
for i0 to VI do
t
visited[i] FALSE
inqueue[i] FALSE
7 Enqueue (Q, node)
8
t
inqueue[node] <-TRUE
while not IsQueueEmpty (Q) do
c← Dequeue (Q)
inqueue[c] FALSE
visited[c] TRUE
t
foreach v in AdjacencyList (G, c) do
if not visited[v] and not inqueue[v] then
12
13
14
15
16
17 return visited
t
Enqueue (Q, v)
inqueue[v] - TRUE](https://content.bartleby.com/qna-images/question/c0851de8-3741-4c3e-9091-0420cbe43fc8/ce174faa-da3c-4fa5-9e19-73ca055af425/zdwu0g_thumbnail.jpeg)
Transcribed Image Text:Given the graph G from Question 2, using the Graph Breadth-First Search algorithm with a Queue,
please do the following:
Assume that the start node is 4 (e.g. node = 4),
Demonstrate a step-by-step, manual desk-check execution of the BFS algorithm, showing the values of
all variables and arrays (e.g. visited, inqueue, Q) for each step in each cycle of each loop, as
demonstrated in class. [
Algorithm: Graph breadth-first search
BFS (G, node) →visited
3
4
5
6
Input: G = (V, E), a graph
node, the starting vertex in G
1
2 visited CreateArray (VI)
10
11
Output: visited, an array of size [V] such that visited[i] is TRUE if we
have visited node i, FALSE otherwise
Q-CreateQueue ()
-
inqueue - CreateArray (VI)
for i0 to VI do
t
visited[i] FALSE
inqueue[i] FALSE
7 Enqueue (Q, node)
8
t
inqueue[node] <-TRUE
while not IsQueueEmpty (Q) do
c← Dequeue (Q)
inqueue[c] FALSE
visited[c] TRUE
t
foreach v in AdjacencyList (G, c) do
if not visited[v] and not inqueue[v] then
12
13
14
15
16
17 return visited
t
Enqueue (Q, v)
inqueue[v] - TRUE
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- Present an algorithm (in outline form) for inserting an element into a sorted linked list so that the list is always in sorted order. Do not utilize a sorting routine, but rather devise an insert (add) algorithm that will search the list and insert the new element in the proper place in the list so that the list is always in order. Assume that the objects involved all properly override both the equals (==) and the compareTo (>, <, >=, and <=) methods. The list is to be maintained in ascending order. Assume that the add method has the following signature. public void Add(E element)arrow_forwardCould you help me the following questions? Sara and her friends said they have discovered a way to get O(1) category performance for both insert and remove in a priority queue. Their description of the data structure and algorithms is as follows: They use an array implementation for the priority queue The index of the array represents the rank of an element – e.g. an element whose rank is 50 will be placed at index 49 Each element is the head node to a linked list – if a new element is inserted into the priority queue with the same rank as another element already in the queue, the new element is added to the linked list at its head Example: If an element “X” with rank 25 exists at index 24, and a new element “Y” also has a rank of 25, the linked list at index 24 is “Y” then “X” When remove is performed, the element at the highest index is removed. If there is more than one node at that index, the node at the head of the linked list there is removed Based on this description of the…arrow_forwardImplement two versions of the successor function for the 8-puzzle: one that generates all the successors at once by copying and editing the 8-puzzle data structure, and one that generates one new successor each time it is called and works by modifying the parent state directly (and undoing the modifications as needed). Write versions of iterative deepening depth-first search that use these functions and compare their performance.arrow_forward
- Array lists and linked lists are both examples of list implementations. Give an example of a case in which an array list might be preferable over a linked list. Justify your actions in each scenario.arrow_forwardGiven two (singly) linked lists, determine if the two lists intersect. Return the intersecting node. Note that the intersection is defined based on reference, not value. That is, if the kthnode of the first linked list is the exact same node (by reference) as the jth node of the secondlinked list, then they are intersecting.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY