
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
Given the list of possible active attacks; os exploits, virus, trojan, syn scan, Ack Scan, and web Attacks and given a firewall between the Internet (represented by a cloud) and your network router.
which of these types of attacks are not able to be prevented through the firewall?
why are these types of attacks not able to be prevented through the firewall?
How can these attacks be prevented from taking place?
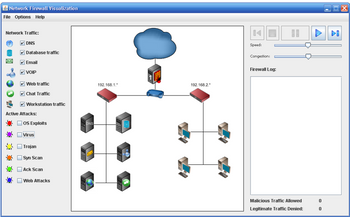
Transcribed Image Text:Network Firewall Visualization
File Options Help
Network Traffic:
✔DNS
Database traffic
Email
VOIP
je da je je
Web traffic
Chat Traffic
Workstation traffic
Active Attacks:
Os Exploits
Virus
Trojan
Syn Scan
Ack Scan
Web Attacks
DNS
192.168.1.
192.168.2.
14
Speed:
Congestion:
Firewall Log:
II
Malicious Traffic Allowed
Legitimate Traffic Denied:
0
0
'
X
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- For the ZeuS malware, please write a short paragraph based on the given background and website info: ZeuS – Trojan ZeuS is a modular banking trojan that uses keystroke logging to compromise credentials when a victim visits certain banking websites. Since the release of the ZeuS source code in 2011, many other malware variants have adopted parts of its codebase, which means that incidents classified as ZeuS may actually be other malware using parts of the original ZeuS code. https://www.cisecurity.org/insights/blog/top-10-malware-december-2022 Zeus malware can give attackers full access to infected machines. While the original Zeus variant primarily utilized man-in-the-browser keyloggers to gain access to an infected computer’s banking credentials and other financial information, many forms of the Zeus virus can also be used to add CryptoLocker ransomware to an operating system or add infected computers to a botnet to perform distributed denial-of-service (DDoS) attacks. The Zeus…arrow_forwardExplain the definition of the word "firewall" in terms of system privacy, and explain how it is employed in different network topologies.arrow_forwardTo what ends does a firewall primarily serve?At the moment, I'm developing a packet filtering programme. What are the guidelines I must follow?arrow_forward
- In what order of prevalence do you think the various types of known threats should be presented and supported with URLs?arrow_forwardLook at the connection between network and computer security and viruses of all kinds. Is there a specific kind of virus that, in your view, poses a greater danger to the security of data and systems than others?arrow_forwardJustify your comparison of a firewall to a stream of packetized data.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education