
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Linked list question. The answer is highlighted in red. Could you show me step by step how to solve this. Thanks!
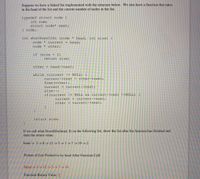
Transcribed Image Text:Suppose we have a linked list implemented with the structure below. We also have a function that takes
in the head of the list and the current number of nodes in the list.
typedef struct node {
int num;
struct node* next;
} node;
int whatDoesItDo (node * head, int size) {
node * current = head;
node * other;
if (size < 2)
return size;
other = head->next;
while (current != NULL) {
current->next = other->next;
free (other);
current = current->next;
size--;
if(current != NULL & & current->next !=NULL) {
current = current->next;
other = current->next;
return size;
If we call what DoesItDo(head, 8) on the following list, show the list after the function has finished and
state the return value.
head -> 3 -> 8 -> 12 -> 5 -> 1 ->7 -> 19 -> 2
Picture of List Pointed to by head After Function Call:
Head -> 3 -> 12 -> 5 -> 7 -> 19
Function Return Value: 5
Expert Solution
arrow_forward
Step 1
Step by stepSolved in 2 steps with 2 images

Knowledge Booster
Similar questions
- Describe the challenges and strategies for managing keyword databases in large-scale web applications. How can developers optimize keyword-based search functionality?arrow_forwardDescribe the 3 different types of graphs utilized by quantitative researchers during our week in the computer lab. When is each type of graph appropriate for the display of data?arrow_forwardA project on marriage planning in spreadsheetarrow_forward
- Explain the concept of federated search and its application in aggregating search results from multiple sources, such as databases and web services.arrow_forwardWhat is a horse of Troy? Three instances.arrow_forwardFaigley & Selzer give a checklist (with six criteria) for evaluating online sources. What are some of these criteria that they offer for evaluating the credibility of Web sites? Explain with details and examples.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY