
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Can I please get help?!
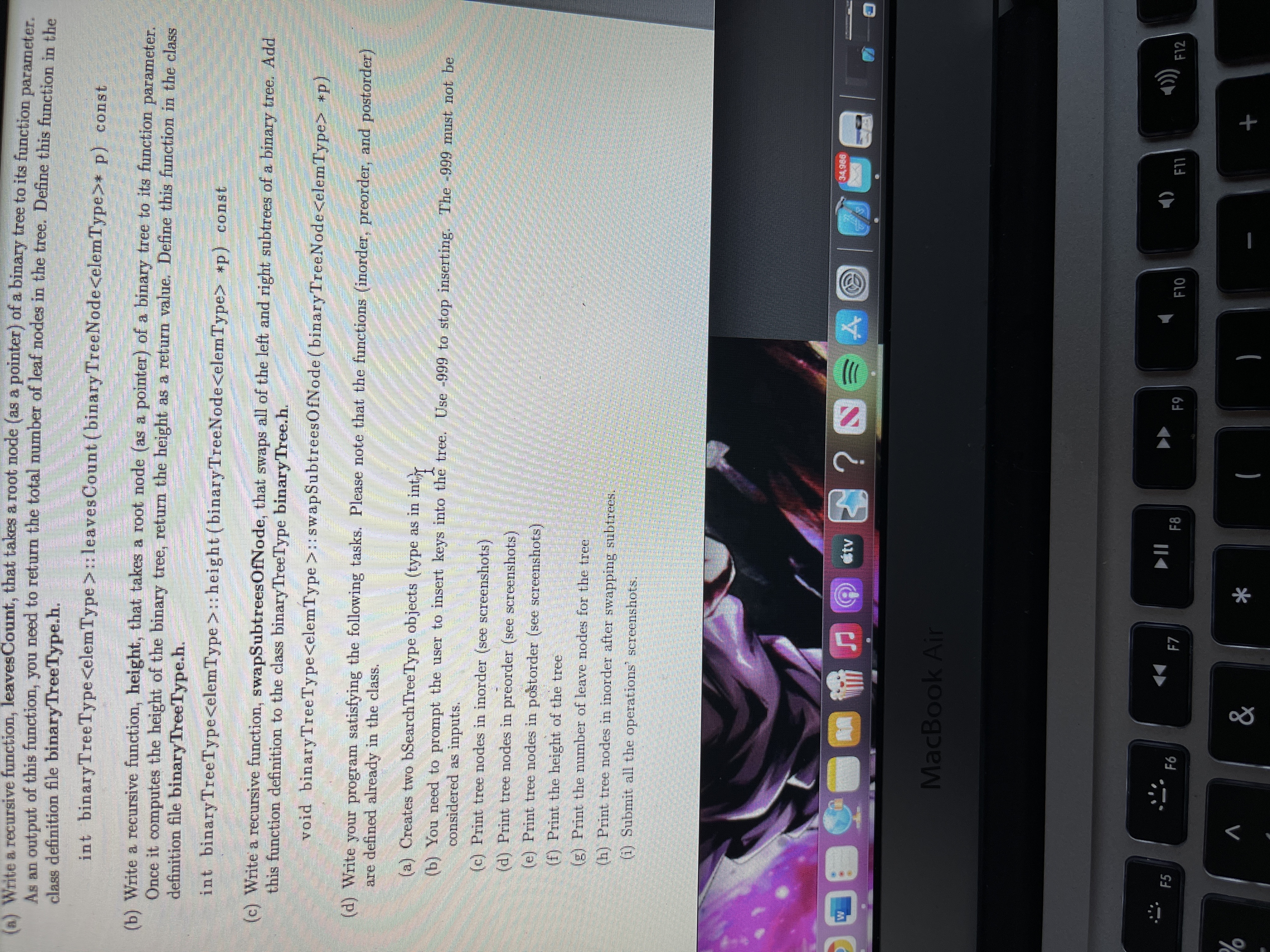
Transcribed Image Text:Write a recursive function, leavesCount, that takes a root node (as a pointer) of a binary tree to its function parameter
As an output of this function, you need to return the total number of leaf nodes in the tree. Define this function in the
class definition file binaryTreeType.h.
int binaryTreeType<elem Type >:: leaves Count (binary TreeNode<elemType> p) const
(b) Write a recursive function, height, that takes a root node (as a pointer) of a binary tree to its function parameter.
Once it computes the height of the binary tree, return the height as a return value. Define this function in the class
definition file binaryTreeType.h.
int binaryTreeType<elemType>:: height (binaryTreeNode<elemType> *p) const
(c) Write a recursive function, swapSubtreesOfNode, that swaps all of the left and right subtrees of a binary tree. Add
this function definition to the class binaryTreeType binaryTree.h.
void binaryTreeType<elemType>::swapSubtreesOfNode (binaryTreeNode<elemType> *p)
(d) Write your program satisfying the following tasks. Please note that the functions (inorder, preorder, and postorder)
are defined already in the class.
(a) Creates two bSearch TreeType objects (type as in intr
(b) You need to prompt the user to insert keys into the tree. Use -999 to stop inserting. The -999 must not be
Considered as inputs.
(c) Print tree nodes in inorder (see screenshots)
(d) Print tree nodes in preorder (see screenshots)
(e) Print tree nodes in postorder (see screenshots)
(f) Print the height of the tree
(g) Print the number of leave nodes for the tree
(h) Print tree nodes in inorder after swapping subtrees.
(i) Submit all the operations' screenshots.
134988
étv
MacBook Air
F5
F7
F8
F12
OL
V
%
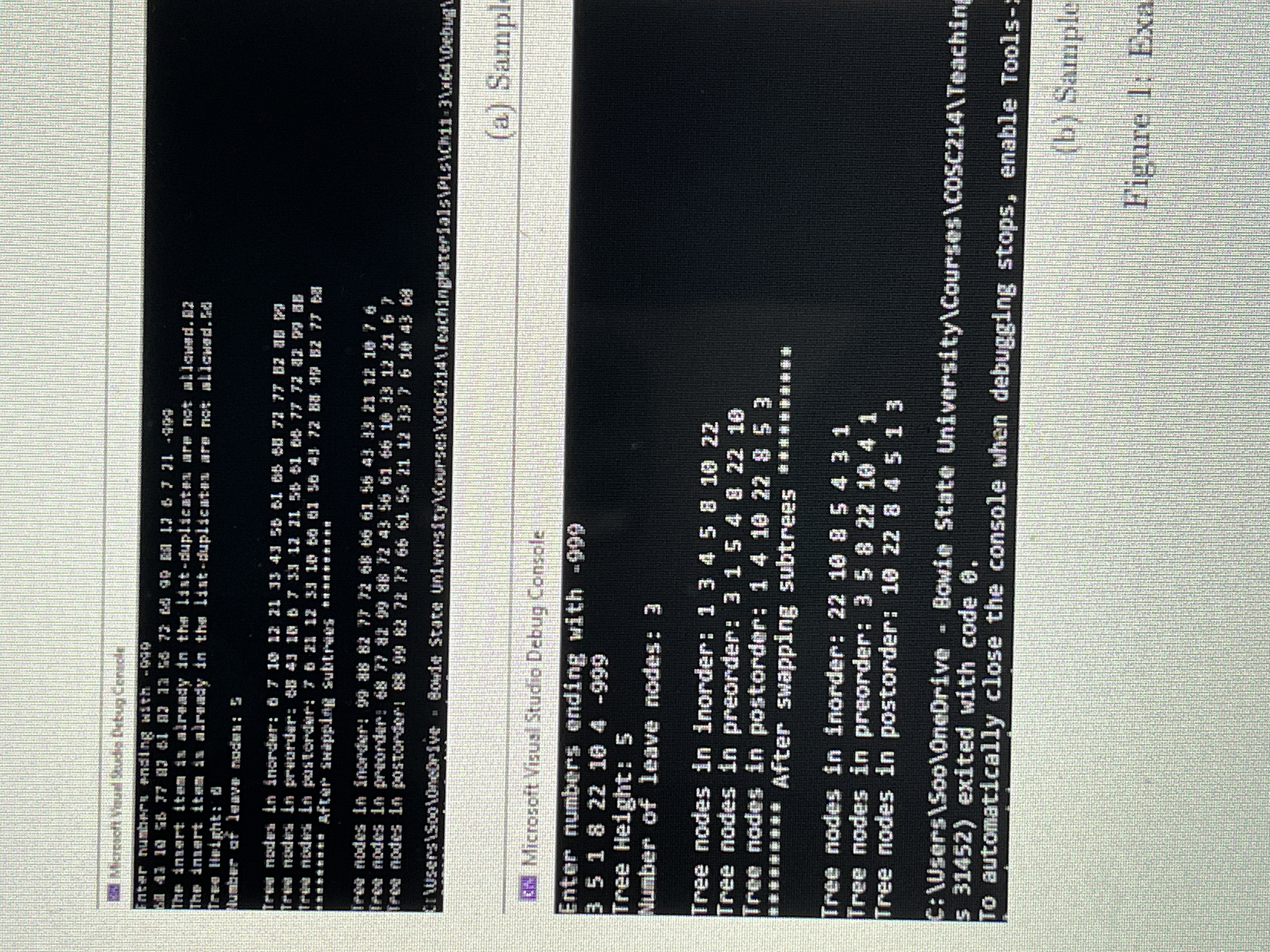
Transcribed Image Text:Microacft Vnual Studio Debug Censole
aiready in the list-duplicaten are not allewed. 02
The insert item
The innert iten is alrady in the lint-duplicutan are not alicwad. Ea
Tree lieight: 0
EE 2主 L 1件 1E ET E宝よ C :p uT apau aal
劉 2 長 Z E t ES 2T EE よ pA1B uT apu al
我台动老曲 具ftr SHapsiae Subtrees e時相的水世会信和图
Iree nodes in inorder: 99 8 82 F 68 66 61 56 43 4 21 12 10 76
Iree nodes In preorder: 68 77 a2 99 88 72 43 56 61 66 1033 12 21 67
iree nodes in postorde! 99 82 72 77 66 61 56 21 12 3376 10 43 68
trWsers\Soo\ữneorive
Bowie State UniversityCoursesC0SC214\TeachingtaterialsPLs\Chi1-3x64\Debug
(a) Sample
N Microsoft Visual Studio Debug Console
Enter numbers ending with -999
351822 10 4 -999
Tree Height: 5
Number of leave nodes: 3
Tree nodes in inorder: 1 3 4 5 8 10 22
Tree nodes in preorder: 3 1 5 4 8 22 10
Tree nodes in postorder: 1 4 10 22 8 5 3
*車非車車車車*After swapping subtrees 車車曲1
Tree nodes in inorder: 22 10 8 5 4 3 1
Tree nodes in preorder: 3 5 8 22 10 4 1
Tree nodes in postorder: 10 22 8 45 1 3
C:\Users\Soo\OneDrive Bowie State University\Courses\CosC214\Teaching
s 31452) exited with code e.
To automatically close the console when debugging stops, enable Tools-:
(b) Sample
Figure 1: Exa
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- Write a command to determine the following questions. 1) Which stores are the most popular black Friday either online or instore ? 2) Do people prefer online or instore black Friday shopping?arrow_forwardThe term for this kind of assault is a poison package. What are two examples of this sort of assault that you can provide?arrow_forwardcreate a search statement on: The effect of the COVID-19 pandemic on higher education. Using Boolean operatorsarrow_forward
- Do the restrictions that are presently in place offer adequate protections to prevent children younger than 16 years old from being injured online? What further measures may governments possibly think of implementing if this is not the case?arrow_forwardWhat exactly does it mean when someone says they are going to assault you with a poison package, and what does it imply? Please provide two examples of this kind of violent attack.arrow_forwardDo we expect that minors under the age of 16 will be protected from harm online by the current regulations? What other measures may governments think about doing if this is not the case?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY