
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
thumb_up100%
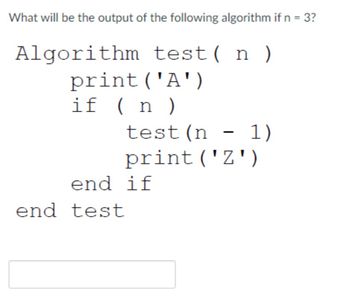
Transcribed Image Text:What will be the output of the following algorithm if n = 3?
Algorithm test (n)
print ('A')
if (n)
test (n − 1)
print ('Z')
end if
end test
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- Divide and Conquer is one of the important design method for Algorithm. What is the major feature to design an algorithm applying the Divide and Conquer idea ? 單選: a. Recursive in Assign, Calculate, Output. O b. Recursive in Assign, Divide, Conquer. O c. Recursive in Divide, Calculate, Combine. d. Recursive in Divide, Conquer, Combine. e. Recursive in Calculate, Conquer, Combine. We call it as 3C.arrow_forwardThe following code is used to derive Fibonacci algorithm with this sequence: (0, 1, 1, 2, 3, 5, 8, 13, 21, …) where each number is “add” of two previous ones. int fib(int n){ if (n==0) return 0; else if (n == 1) return 1; else return fib(n−1) + fib(n−2); } Explain why the following RISC-V assembly code works, you need to explain all the details using the comments as hints? # IMPORTANT! Stack pointer must remain a multiple of 16!!!! addi x10,x10,8 # fib(8), you can change it fib: beq x10, x0, done # If n==0, return 0 addi x5, x0, 1 beq x10, x5, done # If n==1, return 1 addi x2, x2, -16 # Allocate 2 words of stack space sd x1, 0(x2) # Save the return address sd x10, 8(x2) # Save the current n addi x10, x10, -1 # x10 = n-1 jal x1, fib # fib(n-1) ld x5, 8(x2) # Load old n from the stack sd x10, 8(x2) # Push fib(n-1) onto the stack addi x10, x5, -2 # x10 = n-2 jal x1, fib # Call fib(n-2)…arrow_forward
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY