
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
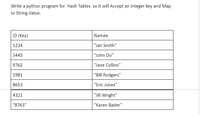
Transcribed Image Text:Write a python program for Hash Tables so it will Accept an integer key and Map
to String Value.
ID (Key)
Namee
1234
"Jan Smith"
3445
"John Do"
9762
"Jane Collins"
1981
"Bill Rodgers"
8653
"Eric Jones"
4321
"Jill Wright"
"8763"
"Karen Bader"
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Follow-up Questions
Read through expert solutions to related follow-up questions below.
Follow-up Question
Please update the code so that the user can insert integer key and assign map to string value. THANK YOU!!
Solution
by Bartleby Expert
Follow-up Questions
Read through expert solutions to related follow-up questions below.
Follow-up Question
Please update the code so that the user can insert integer key and assign map to string value. THANK YOU!!
Solution
by Bartleby Expert
Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- The factors that affect a hash table's Big-O performance are listed below in decreasing order of significance:arrow_forwardThe following variables, listed in order of importance, affect a hash table's Big-O performance:arrow_forwardUse the following values to answer the questions bellow 66 47 87 900 126 140 145 500 177 285 393 395 467 566 620 735Store the values into a hash table with ten buckets, each containing three slots. If a bucket is full, use the next (sequential) bucket that contains a free slot.arrow_forward
- The following are applications of hash functions EXCEPT FOR Question 15 options: AES encryption algorithm Storing Passwords File synchronization Digital Signaturesarrow_forwardUsing double Hashing, insert items with keys: 69, 86, 33, 47, 17, 55 into an empty hash table. tableSize: 7 hash1(x) = x mod tableSize. hash₂(x) = R-(x mod R), R is a prime number smaller than tableSize hash1(x) + hash2(x) mod tableSizearrow_forwardImplement a hash table and write a function to find the most frequently occurring word in a large text file.arrow_forward
- Write the lines of code to insert the key (book's ISBN) and value ("book") pair into "my_hash_table".arrow_forwardUse Python to program a hash with a couple of people and their interconnected birth years. Next, show the people's names and their birth years, and have the user enter one. Reverse the hash and show the birth years, having the user choose a birth year. Then, show the person's name for that birth year. Also, the user should have the option to add and delete entries.arrow_forwardjava Draw a picture of the HashSet created by the data shown below. Assume the HashSet (1) has an initial size of 11, (2) uses separate chaining, and (3) inserts new nodes at the start (not end) of the chain. -4, 2, 18, 23, -15, 47, 87, 2032, 5393, 2, 53432arrow_forward
- Consider the following two functions written in pseudocode: functionA() print "what is your age?" return the input value functionB(int age) look up life expectancy for a person who is age years old in a hash table return the life expectancy Which function has referential transparency? O neither O functionB O functionA O botharrow_forwardJava programming Computer science Please please help mearrow_forwardA typical hash function often consists of the following three steps:arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education