
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Output should be in java
Transcribed Image Text:Excep 10 Design_Test (Compatibility Model - Word
Draw
Design
Layout
References
Mailings
Review
View
Help
O Tell me what you want
alibri (Body)
-A A Aa- E-E- E.
11
AaBbCcDc AaBbCcDc A
IU abe x, X
A y A
1 Normal
1 No Spac
Font
Paragraph
17
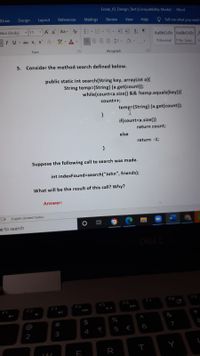
5. Consider the method search defined below.
public static int search(String key, arrayList a){
String temp=(String) (a.get(count));
while(count<a.size() && !temp.equals(key)}{
count++;
temp=(String) (a.get(count));
if(count<a.size())
return count;
else
return -1;
}
Suppose the following call to search was made.
int indexFound%3search("John", friends);
What will be the result of this call? Why?
Answer:
English (United States)
re to search
F9
F7
F6
F5
F3
F4
F1
F2
%23
€
6
Y
R
%244
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 1 images

Knowledge Booster
Similar questions
- Use the pseudocode methods below to answer the questions in C++. FIRST METHOD: COMMENT parameters should be integers METHOD largestValue(parameters: num1, num2) BEGIN IF(num1 >= num2) THEN result ← num1 ELSE result ← num2 ENDIF END largestValue SECOND METHOD: COMMENT parameters should be doubles METHOD largestValue(parameters: num1, num2) BEGIN IF(num1 >= num2) THEN result ← num1 ELSE result ← num2 ENDIF RETURN result END largestValue THIRD METHOD: COMMENT parameters should be integers METHOD largestValue(parameters: num1, num2, num3) BEGIN IF(num1 >= num2 AND num1 >= num3) THEN result ← num1 ELSE IF (num2 >= num3) THEN result ← num2 ELSE result ← num3 ENDIF RETURN result END largestValue Given the pseudocode methods above and on the previous page, which method corresponds to each of the method calls specified? What would that method return based on…arrow_forwardpython code Merge following two Python dictionaries into one. dict1 = {'One': 1, 'Eleven': 11, 'Twelve': 12} dict2 = {'Twelve': 12, 'Twenty': 20, 'Thirty': 30} Expected Output: {'One': 1, 'Eleven': 11, 'Twelve': 12, 'Twenty': 20, 'Thirty': 30}arrow_forwardIn Java, an identifier, which can be class name or method name, is a series (string) of the following groups/types of characters: {fill/continue from 2) (1) Lower-case alphabet characters: a – z, (2) ……………..… (3) …………….…… (4) ……………... (5) ………….arrow_forward
- Problem Statement: A painting company has determined that for every 115 square feet of wall space, one gallon of paint and eight hours of labor will be required. The company charges $20.00 per hour for labor. Develop a Java program that performs the following: Input Requirements: Set up the data for the following as named constants for one gallon of paint: 115 square feet of wall space eight hours of labor Also, set up a named constant for the following: $20.00 per hour for labor Enter the following input data at the keyboard: The square feet of wall space to be painted The price of the paint per gallon Processing: Your program is to perform the following calculations: The number of gallons of paint required The hours of labor required The cost of the paint The labor charges The total cost of the paint job Output Requirements: The square feet of wall space to be painted The price of the paint per gallon The number of gallons of paint required The hours of labor…arrow_forwardb. Java programing question provide a solution for the following with the most basic understanding of Java so I understandarrow_forwardTHIS IS FOR C++ ONLY Part 2b: Password Verification A secure password is critically important in today's world. Organizations typically have stringent requirements to ensure a password is complex enough so as not to be easily hacked. Write a program that will accept as input a potential password and determine whether or not it is valid in meeting the following criteria: at least eight characters long at least one uppercase letter at least one lowercase letter at least one digit at least one special character (you can determine what is acceptable) If the password is valid, ask the user to enter it again. If it matches, indicate the password has been accepted. If the password does not meet any of the above criteria, indicate which it does not meet.arrow_forward
- JAVA Data type Java assignment meaning of operator int float double and string Pick one Java polymorphic arithmetic operator and write Java code statements that demonstrate its function for ints, floats, doubles, and strings. Also, indicate what role the operator is performing in the table below.arrow_forwardPlease answer question. This is pertaining to Java programming language 2-17arrow_forwardVariable W X Y Z arr for (x = 0; x <= z; x++) { W = W + x; y = y - 1; Register $50 $s1 $s2 Translate the following code from Java to MIPS: } $s3 $s4arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY