
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
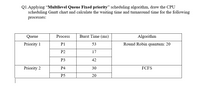
Transcribed Image Text:Q1.Applying "Multilevel Queue Fixed priority" scheduling algorithm, draw the CPU
scheduling Gantt chart and calculate the waiting time and turnaround time for the following
processes:
Queue
Process
Burst Time (ms)
Algorithm
Priority 1
P1
53
Round Robin quantum: 20
P2
17
P3
42
Priority 2
Р4
30
FCFS
P5
20
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps with 2 images

Knowledge Booster
Similar questions
- An operating system uses the banker’s algorithm for deadlock avoidance when managing the allocation of three resource types X, Y and Z to three processes P0, P1 and P2. The table given below presents the current system state. Here, the Allocation matrix shows the current number of resources of each type allocated to each process and the Max matrix shows the maximum number of resources of each type required by each process during its execution Allocation Max X Y Z X Y Z P0 0 0 1 8 4 3 P1 3 2 0 6 2 0 P2 2 1 1 3 3 3 There are 3 units of type X, 2 units of type Y and 2 units of type Z still available. The system is currently in safe state. Consider the following independent requests for additional resources in the current state- REQ1: P0 requests 0 units of X, 0 units of Y and 2 units of Z REQ2: P1 requests 2 units of X, 0 units of Y and 0 units of Z Write a program to check whether: Only REQ1 can be permitted Only REQ2 can be permitted…arrow_forwardSuppose that an operating system supports two kinds of sequential processes: high-priority interactive processes, and low-priority non-interactive processes. The behavior of the high-priority processes is to alternate between periods of computation of duration Tc and periods of blocking (waiting for input) of duration Tb. The behavior of the low-priority processes is to compute constantly, with no blocking. The operating system’s scheduling policy is round-robin with a quantum q, where Tc < q. Scheduling decisions are made only when a quantum expires, or when the running process blocks. The scheduler selects a low-priority process to run only if no high-priority processes are ready. Suppose there is one high-priority process and one low-priority process in the system, and that both processes will run for a long time. For what fraction of the time does the low-priority process run?arrow_forwardA) In pseudocode, implement and explain the time complexity analysis of the quicksort algorithm, detailing the best-case, worst-case, and average-case scenarios. Additionally, discuss the factors that influence these scenarios and how they impact the overall efficiency of the algorithm. B) In pseudocode, implement and explain the time complexity analysis of the merge sort algorithm, detailing the best-case, worst-case, and average-case scenarios. Additionally, discuss the factors that influence these scenarios and how they impact the overall efficiency of the algorithm.arrow_forward
- Assume we have a free space management system as described in the book, for example one used to provide us with virtual addresses on the heap (with physical addresses handled by a much simpler system since we assume paging). Assume the system uses the following very simple rules; A memory request traverses the free list, and finds the first block large enough to handle the request (i.e., the first fit algorithm from the book). It then: Splits the block into 2 pieces: The first piece will be the requested size + 1k (for a header). The second will be the remaining The first piece will be returned to the caller, but the address returned will be the address of the memory for the user, that is the header + 1k The second will be put back into the linked list If there's insufficient contiguous memory, the allocation will fail (return 0) Free memory is stored as a linked list in address order Assume we start with a single contiguous block of FREE memory of size 64k starting at location…arrow_forwardReal-time Scheduling: Choose all true assertions. Rate Monotonic (RM) scheduling divides time into equal parts and requires each process to seek a portion upon starting. RM schedules real-time systems with CPU utilization below 1. When CPU utilization is less than 1, Earliest Deadline First (EDF) may schedule a real-time system. A process is initiated every p time unit. RM scheduling prioritizes shorter processes. EDF scheduling prioritizes processes with the shortest time frame.arrow_forwardFor Question, put your answer in the following blanks. Note: You must put answer only, no need to put the unit. One answer per blank.arrow_forward
- Merge sort is an efficient sorting algorithm with a time complexity of O(n log n). This means that as the number of elements (chocolates or students) increases significantly, the efficiency of merge sort remains relatively stable compared to other sorting algorithms. Merge sort achieves this efficiency by recursively dividing the input array into smaller sub-arrays, sorting them individually, and then merging them back together. The efficiency of merge sort is primarily determined by its time complexity, which is , where n is the number of elements in the array. This time complexity indicates that the time taken by merge sort grows logarithmically with the size of the input array. Therefore, even as the number of chocolates or students increases significantly, merge sort maintains its relatively efficient performance. Regarding the distribution of a given set of x to y using iterative and recursive functions, the complexity analysis depends on the specific implementation of each…arrow_forwardAn operating system uses the banker's algorithm for deadlock avoidance when managing the allocation of three resource types X, Y and Z to three processes P0, P1 and P2. The table given below presents the current system state. Here, the Allocation matrix shows the current number of resources of each type allocated to each process and the Max matrix shows the maximum number of resources of each type required by each process during its execution Allocation Маx X Y X Y PO 1 8 3 P1 3 2 6 2 P2 1 3 3 3 There are 3 units of type X, 2 units of type Y and 2 units of type Z still available. The system is currently in safe state. Consider the following independent requests for additional resources in the current state- REQ1: PO requests 0 units of X, 0 units of Y and 2 units of Z REQ2: P1 requests 2 units of X, 0 units of Y and 0 units of Z Write a program to check whether: Only REQ1 can be permitted Only REQ2 can be permitted Both REQ1 and REQ2 can be permitted Neither REQ1 nor REQ2 can be…arrow_forwardConsider the following processes schedule using RR Scheduling algorithm If the CPU scheduling policy is Round Robin with time quantum = 3 unit: Process Arrival time Burst Time P1 P2 P3 P4 P5 5 P6 4 3 1 2 5 6 6 7 9 2 Turn around time 3 Draw the ready queue, Gantt Chart for the schedule and find the TAT, WT, RT for each process then, find the Average waiting time, Response Time and the average turnaround time. Waiting Time Response Timearrow_forward
- Now suppose that you are given two unsorted arrays A and B, containing m and n elements respectively. You are also given a black box O(n) selection algorithm SEL that can be called on A and B separately and, in addition, a small number (say, ten) of extra memory words that can be used to store some extra data. Using SEL as a subroutine, design an O(n + m) algorithm for finding the kth smallest element in the combined set of O(m + n) elements. You may not merge the two arrays in another array and call an algorithm (either SEL or something you wrote) on this third array. This is because there is no extra memory available to build this third array.arrow_forwardAlgorithm A, Algorithm B, and Algorithm C perform the same task. On input of size n, Algorithm A executes 10500n instructions, Algorithm B performs 30n2 instructions, and Algorithm C executes the ceiling of (1/1024) * 2n instructions. Assume each instruction requires the same amount of time in each algorithm. Algorithm A is slower than Algorithm B when the size of the input is less than .... Algorithm A is slower than Algorithm C when the size of the input is less than .... Algorithm C is fastest of the three when the size of the input is less than ....arrow_forwardBriefly discuss the main differences between preemptive and non- preemptive algorithm. Then discuss the following statement (Shortest job first (SJF) scheduling can be implemented in preemptive and non- preemptive way.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY